Appendix F: Copying Files from Production to Test Environments (Field Procedures)
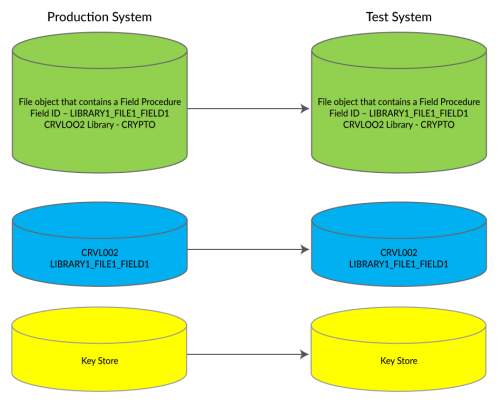
When a field is encrypted in a file using Field Procedures, the Field Identifier and Library that holds the Field Registry (CRVL002) are saved into the file. This tells Powertech Encryption for IBM i in which library to find the Field Registry (CRVL002) and which entry to use in the registry to get the information about the encryption, such as key stores, masking information, authorization lists, which method was used to encrypt (Field Procedures with AUTH method), and the library where the file exists.
- When the file is saved and then restored to another system:
- The Field Registry (CRVL002) must exist in the Library that is saved with the File.
- An entry in the Field Registry (CRVL002) must exist with the same name that was stored in the file object.
- The entry saves the Key Store name and Library for both Encryption and Decryption Keys. The Keys must be the same Key that was created on the source machine. WARNING: You cannot just create a new random generated Key with the same label as what was used on the source machine. This generates a new key that will not decrypt the data correctly.
-
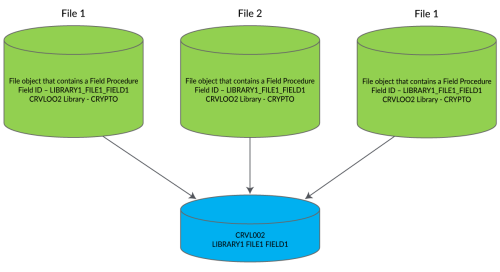
When a file is copied using either CRTDUPOBJ or CPYF with parameter CRTFILE(*YES) the two values stay with the file. The new object will use the same entry in the Field Registry (CRVL002) that the original file uses. If the entry has a status of *ACTIVE the encryption and decryption of the field will work normally in the new file.
- WARNING: If the original file is deactivated and the status is changed to *INACTIVE the Field Procedures will still exist on the newly created file and the encryption and decryption will not work on the file.
- WARNING: The new file cannot be deactivated.
- Copying a file from one file to another with an encrypted field not using CPYF WITH CRTFILE(*YES):
When you read the field you get either the Fully decrypted value, the partially masked data, or the fully masked data depending on what you are authorized to.
- If you are authorized to the full value, you may get a value like ‘8765238790874325’. This value would be inserted into the destination file.
- If you are authorized to a partially masked value, you may get a value like ‘XXXX23879087XXXX’. This value would be inserted into the destination file.
- If you are authorized to a fully masked value, you may get a value like ‘XXXXXXXXXXXXXXXX’. This value would be inserted into the destination file.
If the field in the destination file is encrypted, the value you read out of the source file gets encrypted as it is written to the destination file.