Disaster Recovery
Follow the steps below to restore the Powertech Encryption for IBM i product, user settings, Master Keys and Key Stores in a disaster recovery situation.
-
IBM objects, user profiles and authorization lists should be restored before proceeding.
-
As of IBM i 7.5, modified validation list objects cannot be saved to previous releases. Powertech Encryption cannot be replicated or moved from a system running IBM i 7.5 to a system running a lower version of IBM i.
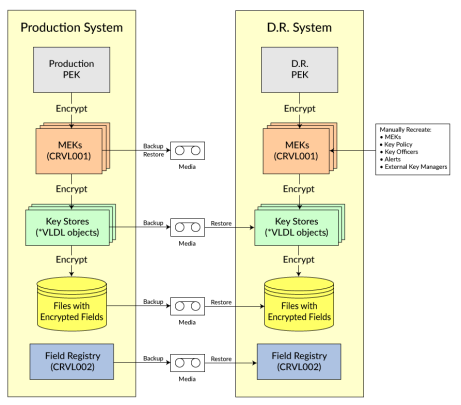
If restoring to the same IBM i serial number:
- Locate the Powertech Encryption for IBM i licensed program on your backup media. If it is not available on the backup media, you can download the product from www.fortra.com.
- Restore the user-created Key Stores from your backup media. The Key Stores are Validation List (*VLDL) objects.
- Restore the CRVL001 *VLDL object from your backup media. This holds the Key Policy, Key Officers, Security Alerts and Master Encryption Keys. By default, the CRVL001 object is located in the CRYPTO library (unless other environments were set up).
- If you use the Field Encryption Registry in Powertech Encryption for IBM i, restore the CRVL002 *VLDL object from your backup media. By default, this object is located in the CRYPTO library (unless other environments were set up).
- If you use the Field Encryption Registry and are using external files to store encrypted database field values and if the ‘last index numbers used’ are stored in the physical file option [LSTINDSTG(*PF) parm on the Registry], then restore the file named CRPF002 from your backup media. By default, the CRPF002 file is located in the CRYPTO library (unless other environments were set up).
- If using external files to store the encrypted database field values, then restore those files (default prefix of CRXX).
If restoring to a different IBM i serial number:
- Locate the Powertech Encryption for IBM i licensed program on your backup media. If it is not available on the backup media, you can download the product from www.fortra.com.
- Follow step 3 only if you did not previously obtain and back up a license key, as defined in the Backup (to external media), Backup: License Keys section. Otherwise, skip to step 4.
-
If needed, contact Fortra Technical Support to obtain a usable license key for the IBM i machine you are restoring to.
- Restore the user-created Key Stores from your backup media. The Key Stores are Validation List (*VLDL) objects.
- If you use the Field Encryption Registry in Powertech Encryption for IBM i, restore the CRVL002 *VLDL object from your backup media. By default, the CRVL002 object is located in the CRYPTO library (unless other environments were set up).
NOTE: The CRVL001 *VLDL object should not be restored if the IBM i Serial number changed, because CRVL001 was encrypted under a different Product Encryption Key (PEK) on the other machine.
- If you use the Field Encryption Registry and are using external files to store encrypted database field values and if the ‘last index numbers used’ are stored in the physical file option [LSTINDSTG(*PF) parm on the Registry], then restore the file named CRPF002 from your backup media. By default, the CRPF002 file is located in the CRYPTO library (unless other environments were set up).
- If using external files to store the encrypted database field values, then restore those files (default prefix of CRXX).
- Reestablish the Key Policy settings using the CHGKEYPCY command.
- Reestablish the Security Alert settings using the WRKCCALR command.
- Reestablish the Key Officers using the WRKKEYOFR command.
- Enter the passphrase parts for each Master Encryption Key (MEK) using the LODMSTKEY (Load Master Key) command. These passphrase parts must be entered exactly as they were on the original system using the same part numbers. Passphrases are case sensitive.
- Generate (set) each Master Encryption Key (MEK) using the SETMSTKEY command.
- The Key Stores, and the Keys stored within them, should then be available for use.
Disaster Recovery Diagram using Field Procedures