Print Audit Log (PRTAUDLOG)
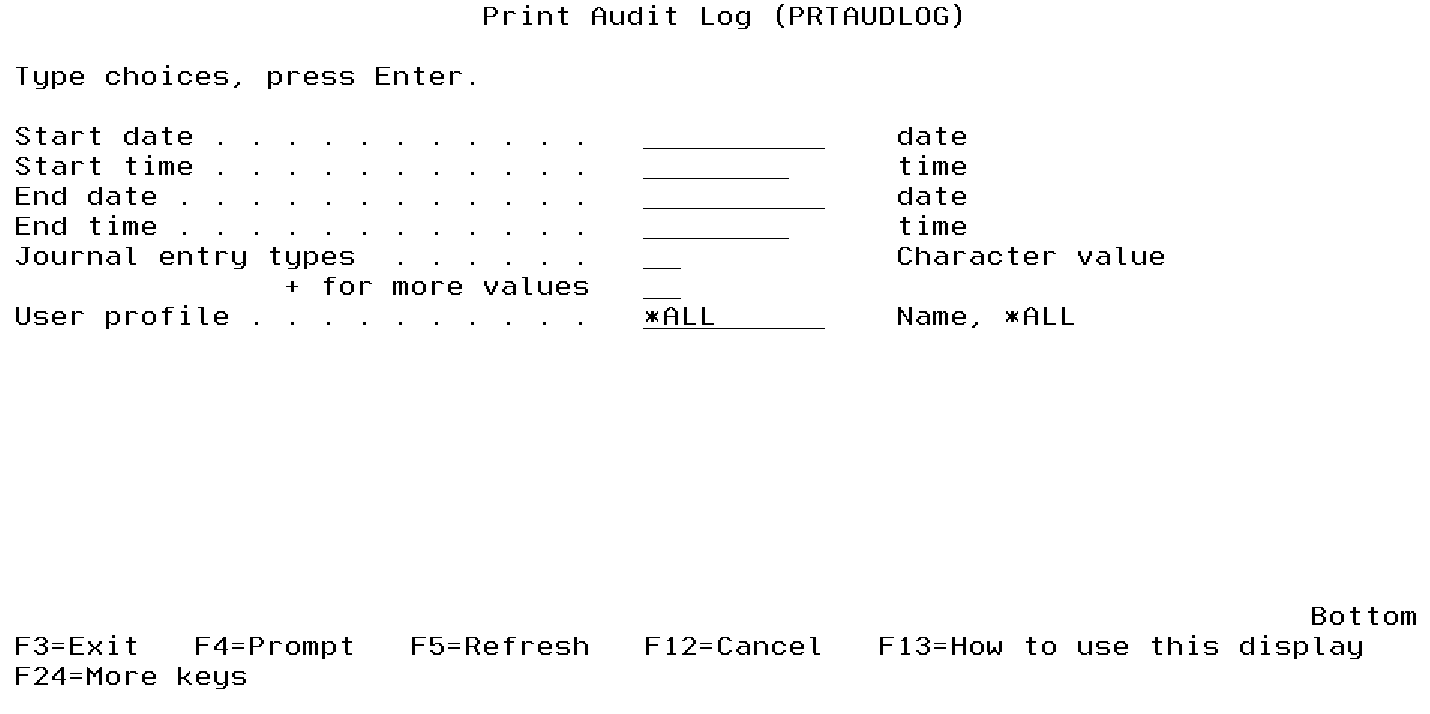
The Print Audit Log (PRTAUDLOG) command allows authorized users to print the Powertech Encryption for IBM i audit log entries. This command provides selection criteria of date and time ranges, audit types and user IDs.
How to Get There
From the Key Policy and Security Menu, choose option 20, Print Audit Log Report. Or, prompt (F4) the command CRYPTO/PRTAUDLOG.
Options
Start date (STRDATE)
Specify the starting date. All audit entries in the range from the starting date and time will be included in the report. The date should be specified in mmddyy or mmddccyy format, with or without date separators.
Start time (STRTIME)
Specify the starting time. All audit entries in the range from the starting date and time will be included in the report.
The time should be specified in 24-hour format, with or without a time separator.
End date (ENDDATE)
Specify the ending date. All audit entries in the range up to the ending date and time will be included in the report. The date should be specified in mmddyy or mmddccyy format, with or without date separators.
End time (ENDTIME)
Specify the ending time. All audit entries in the range up to the ending date and time will be included in the report.
The time should be specified in 24-hour format, with or without a time separator.
Journal entry type (JRNTYPE)
If the journal entry type parameter is left blank, then all Powertech Encryption for IBM i audit entries will be selected. Otherwise, if any journal entry types are entered, then only the entries which match those journal entry types will be selected.
You can specify up to 25 journal entry types to filter on.
Below is a list of Powertech Encryption for IBM i journal entry types.
User profile (USERPRF)
Specify the user profile(s) to select in the audit log.
The possible values are:
Example
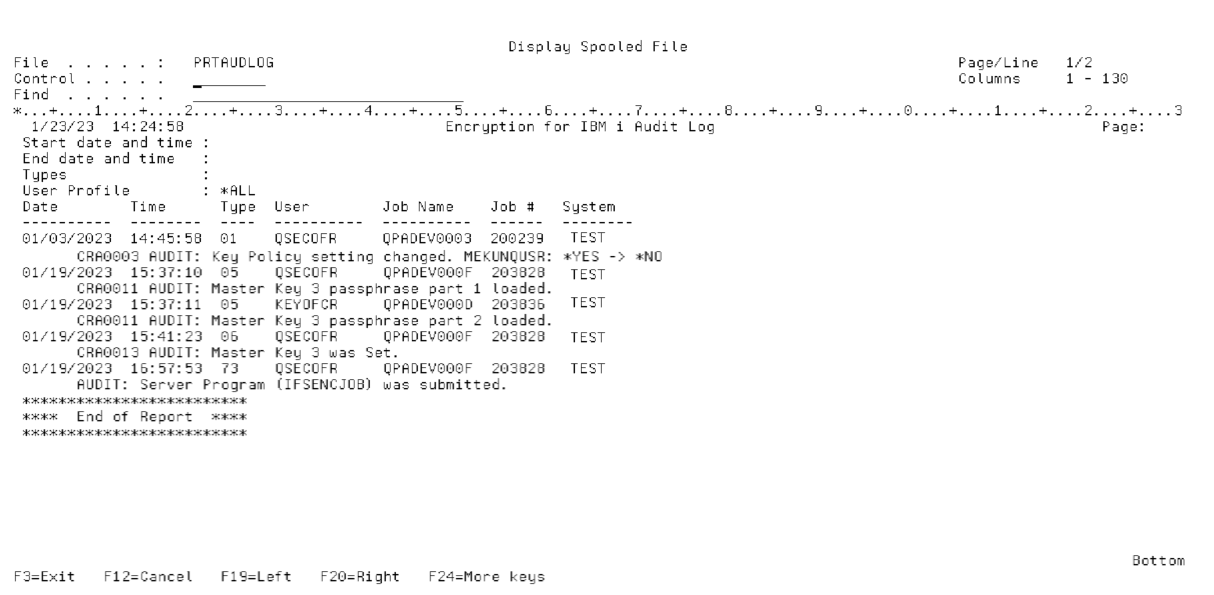
A formatted report will be generated with the audit log entries. For each audit entry printed, it will include the audit date, time, user, job name, job number, audit type and message.