Fuzz Testing with the ARP Protocol
Overview
This topic describes how to test the ARP (Address Resolution Protocol) protocol in beSTORM.
Testing environment requirements
-
beSTORM 13.3.0 or later (licensed)
-
Windows 10 or later
-
A device that supports the ARP protocol (this will be the device under test [DUT])
Fuzzing with beSTORM
To fuzz with the ARP protocol in beSTORM, do the following:
-
Using a network cable, connect the ARP-supported device (DUT) to the beSTORM computer's Ethernet adapter.
-
Open beSTORM Client.
-
Select New Project. The beSTORM New Project Wizard opens.
-
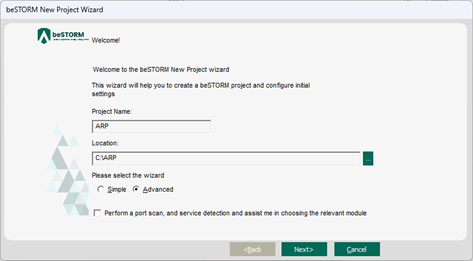
On the Welcome page, do the following:
-
In the Project Name box, enter a name.
-
Optionally, select a different file location for your project in the Location Name box.
-
For Please select the wizard, select Advanced.
-
Leave Perform a port scan, and service detection and assist me in choosing the relevant module unchecked.
-
-
Select Next.
-
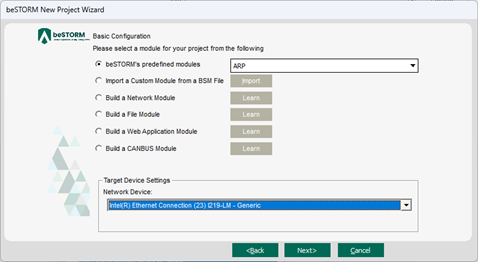
On the Basic Configuration page, do the following:
-
In thebeSTORM's predefined modules list, select ARP.
-
In the Network Device list, select the beSTORM computer's Ethernet adapter where you connected your network cable.
-
-
Select Next.
-
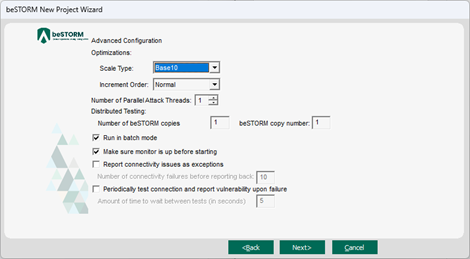
On the Advanced Configuration page, adjust Scale Type to reduce the number of combinations and overall testing duration. For the least number of combinations and shortest testing duration, select Base10.
-
Select Next.
-
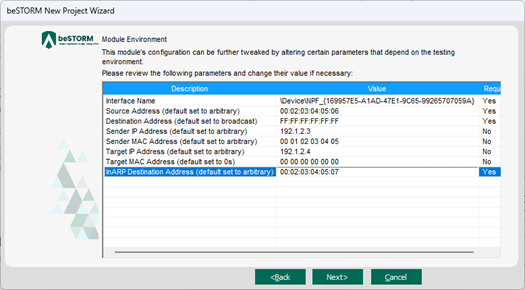
On the Module Environment page, verify the following default values appear in the corresponding Value box for each parameter:
-
Interface Name – In the Value box, confirm it is set to the Ethernet adapter you selected in step 6b.
-
Source Address - Double-click the Value box. In the MAC Address Finder dialog, enter the IPv4 Address of the beSTORM computer and then select Find. The MAC Address box will refresh and display the MAC address of the beSTORM computer. Select OK.
-
Destination Address - Double-click the Value box. In the MAC Address Finder dialog, enter the IPv4 Address of the DUT and then select Find. The MAC Address box will refresh and display the MAC address of the IPsec computer. Select OK.
NOTE: You can also leave this parameter to the default FF:FF:FF:FF:FF:FF value which is the Ethernet broadcast address. Using this value will allow it to be transmitted to all of the hosts on the local subnet. -
Sender IP Address – Leave this parameter set to the default value. This field is one of the fuzzed fields of an ARP packet and it will take a lot of different values.
-
Sender MAC Address – You can leave this parameter set to the default value as this field is one of the fuzzed fields of an ARP packet and it will take a lot of different values, or if you want to set the default value as an specific MAC address, double-click the Value box. In the MAC Address Finder dialog, enter the IPv4 Address of the beSTORM computer and then select Find. The MAC Address box will refresh and display the MAC address of the beSTORM computer. Select OK.
-
Target IP Address – Leave this parameter set to the default value. This field is one of the fuzzed fields of an ARP protocol packet and it will take a lot of different values, and it's the specific IP address you are attempting to resolve in the ARP protocol.
-
Target MAC Address – Leave this parameter to the default value as it refers to one of the fields of an ARP Protocol packet and specifically where the resolved MAC Address will be stored in the response to the ARP request (this is why the default value is all 0s).
-
InARP Destination Address – This value is specific for Inverse ARP request type and cannot be set to the same broadcast address used with the Destination Address parameter. Double-click the Value box. In the MAC Address Finder dialog, enter the IPv4 Address of the DUT and then select Find. The MAC Address box will refresh and display the MAC address of the IPsec computer. Select OK.
-
-
Select Next.
-
On the Test Selection page, select the ARP request types you want to fuzz.
NOTE: R/ARP Request is a random ARP type that contains many combinations and is not ARP-specfic.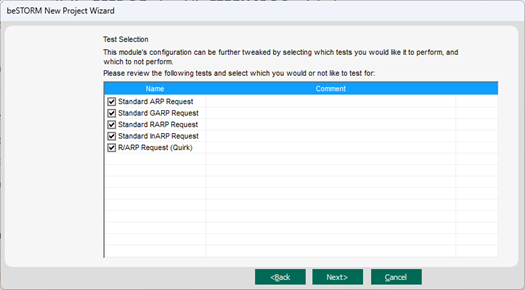
-
Select Next.
-
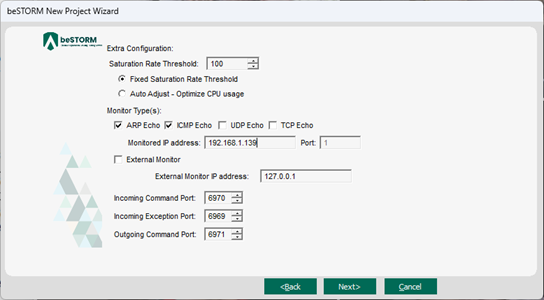
On the Extra Configuration page, do the following:
-
Select the ARP Echo and ICMP Echo checkboxes.
- Set the Monitored IP Address to the DUT's IP address.
-
Leave all other parameters to their default setting.
-
-
Select Next.
-
On the Complete beSTORM wizard page, select Finish to begin fuzzing, or clear the Auto-start beSTORM scan now checkbox to run the test later.
-
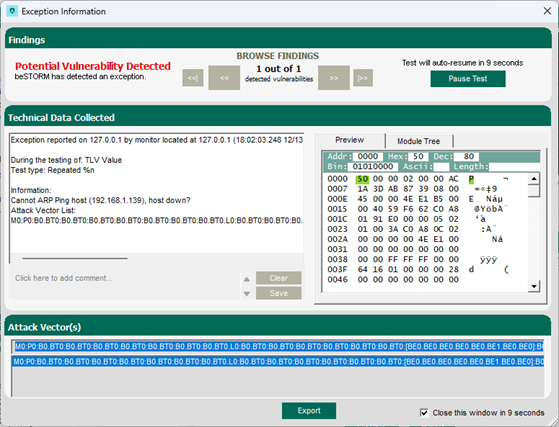
Once your test begins, if an exception occurs (that is, an attack was successful), a message will appear in an Exception Information dialog informing you that the router is not responding. This indicates a possible vulnerability. Testing will resume after five seconds unless you select Pause Test.
-
When fuzzing is complete, select Report > Generate Report from the beSTORM Client to generate a more comprehensive report of your Configuration page.