Fuzz Testing Files
Overview
In this topic, you will learn what file fuzzing is and how beSTORM can help you perform black box testing on your software or application by injecting slightly malformed files.
beSTORM includes the following file modules:
| ANI | HWP | MPEG 4 | TGA |
| AVI H2646-AC3 / AVI XVID | ICO | PAL | TIFF |
| BMP | JASC-PAL | PCAP | UPX |
| DOC | JPEG | WAV (PCM) | |
| GIF | MKV | PNG | WMV |
| HTML | MP3 / MP4 | PPT | XLS |
Why file fuzzing?
As cybersecurity professionals, we are all aware of ransomware attacks started by a dropper hidden within a PDF code, vulnerabilities such as arbitrary code execution on Apple devices, or CVEs published regarding issues in commonly used files that are an opening a backdoor for remote-code execution log in bypass or a buffer overflow. While the vendors normally tend to those vulnerabilities by releasing updates (for example, Microsoft patches or Adobe security updates), developers should still check their software integrity and ability to digest certain files.
For example, a data loss prevention process (DLP) that handles thousands of XLS files daily should be checked as often for its integrity and ability to stand an exhaustive test. Verify the DLP will not crash when scanning malformed XLS files prepared by an attacker.
Other examples are a company that builds a storage application or a company that handles audio files. In fact, any application or device which processes a user input in forms of files should be tested for its ability to do so.
Setup
To configure beSTORM to fuzz files, do the following:
-
Open beSTORM Client.
-
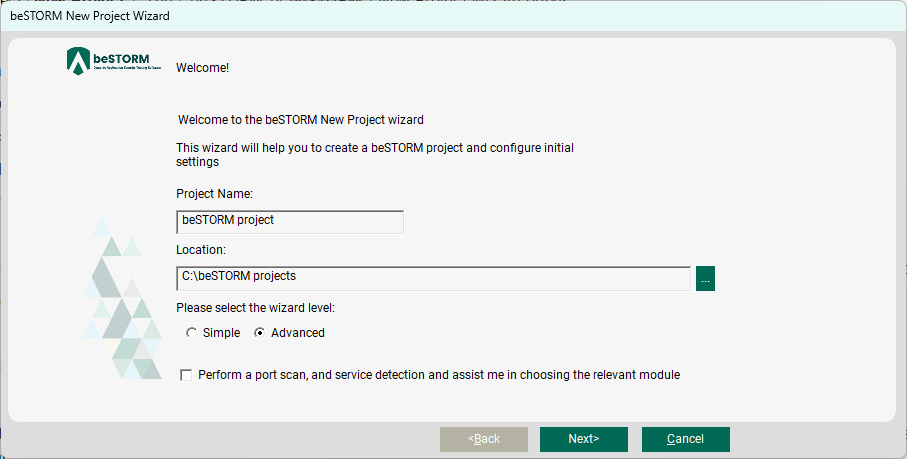
Select New Project. The beSTORM New Project Wizard opens.
-
On the Welcome page, do the following:
-
Select Next.
-
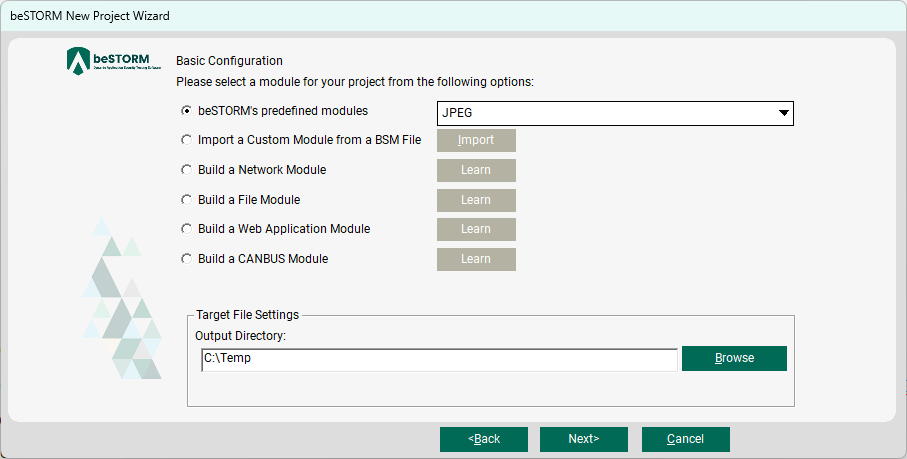
On the Basic Configuration page, do the following:
-
Select Next.
-
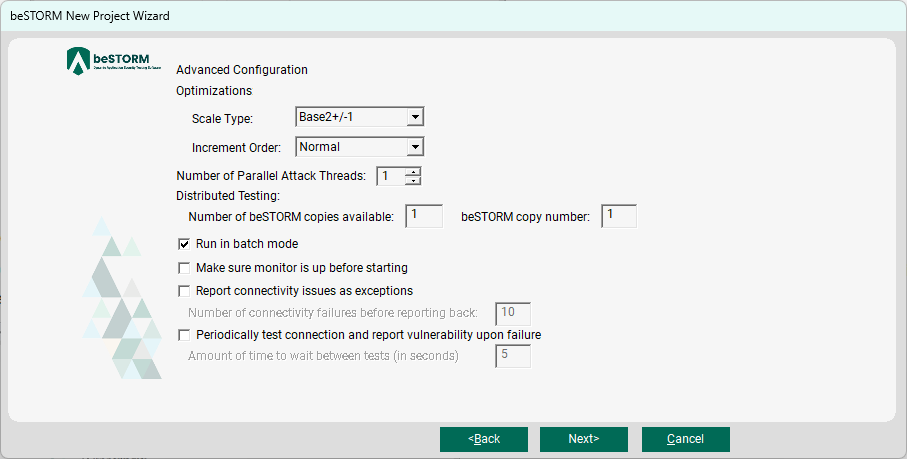
On the Advanced Configuration page, leave these parameters to their default settings.
-
Select Next.
-
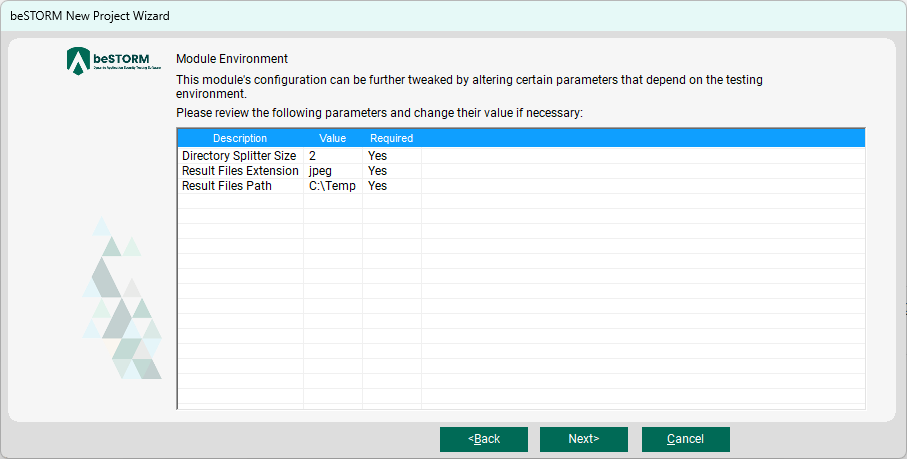
On the Module Environment page, you can choose to split files into more directories, if needed.
NOTE: Adding more directories increases the potential to reveal flaws in the device under test (DUT) but increases the file generation process as well. -
Select Next.
-
On the Extra Configuration page, leave these parameters to their default settings.
-
Select Next.
-
On the Complete beSTORM wizard page, clear the Auto-start beSTORM scan now checkbox.
-
Select Finish to open the beSTORM Client.
-
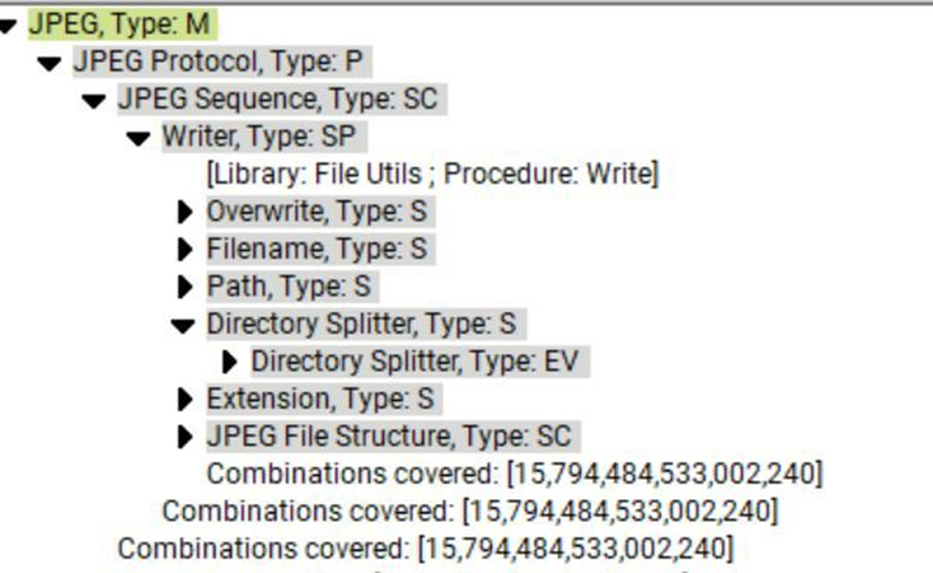
In Module Browser pane, select the down arrows to show how the module is constructed, what will be fuzzed in thee JPEG files (which is sent to the DUT), and how many permutations will be used.
-
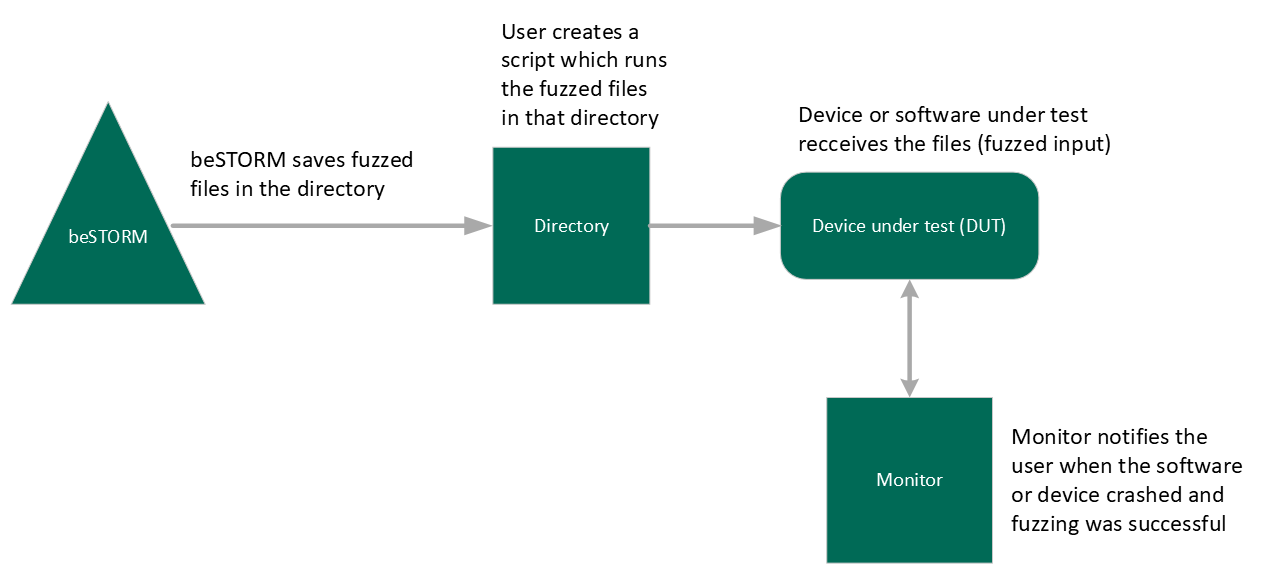
Select Start to begin the file generation process. As beSTORM is working, each subfolder will contain a high amount of malformed JPEG files that will be later used for our script.
-
Once beSTORM is fuzzing, prepare the script and then open the beSTORM Monitor, or run your own debugger to attach it to the application or service while the script is running.