Reports
Cobalt Strike has several report options to help make sense of your data and convey a story to your clients. You may configure the title, description, and hosts displayed in most reports.
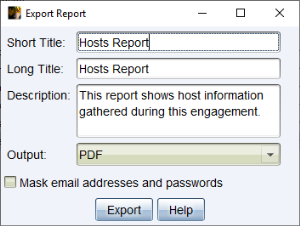
Go to the Reporting menu and choose one of the reports to generate. Cobalt Strike will export your report as an MS Word or PDF document.
figure 77 - Export Report Dialog
Activity Report
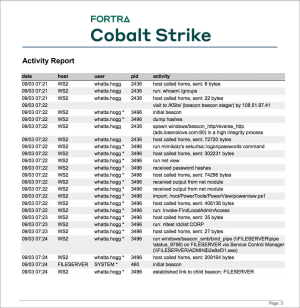
The activity report provides a timeline of red team activities. Each of your post-exploitation activities are documented here.
figure 78 - The Activity Report
Hosts Report
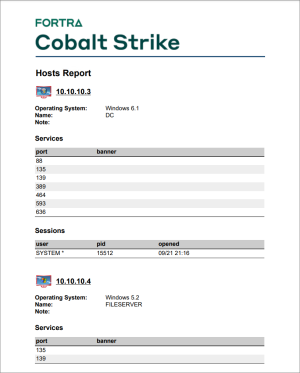
The hosts report summarizes information collected by Cobalt Strike on a host-by-host basis. Services, credentials, and sessions are listed here as well.
figure 79 - The Hosts Report
Indicators of Compromise
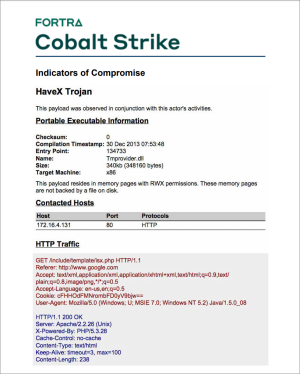
This report resembles an Indicators of Compromise appendix from a threat intelligence report. Content includes a generated analysis of your Malleable C2 profile, which domain you used, and MD5 hashes for files you’ve uploaded.
figure 80 - Indicators of Compromise Report
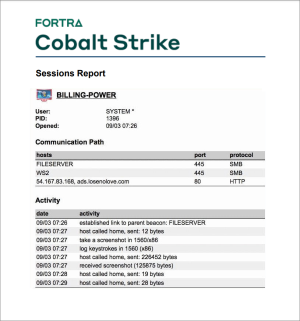
Sessions Report
This report documents indicators and activity on a session-by-session basis. This report includes: the communication path each session used to reach you, MD5 hashes of files put on disk during that session, miscellaneous indicators (e.g., service names), and a timeline of post-exploitation activity. This report is a fantastic tool to help a network defense team understand all of red’s activity and match their sensors to your activity.
figure 81 - The Sessions Report
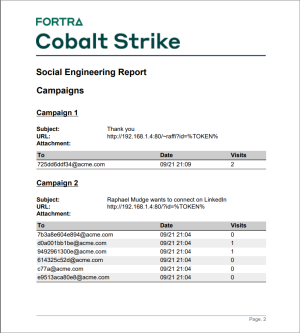
Social Engineering
The social engineering report documents each round of spear phishing emails, who clicked, and what was collected from each user that clicked. This report also shows applications discovered by the system profiler.
figure 82 - The Social Engineering Report
Tactics, Techniques, and Procedures
This report maps your Cobalt Strike actions to tactics within MITRE’s ATT&CK Matrix. The ATT&CK matrix describes each tactic with detection and mitigation strategies. You may learn more about MITRE’s ATT&CK at: https://attack.mitre.org/