Welcome to Cobalt Strike 
Cobalt Strike is a platform for adversary simulations and red team operations. The product is designed to execute targeted attacks and emulate the post-exploitation actions of advanced threat actors. This section describes the attack process supported by Cobalt Strike’s feature set. The rest of this manual discusses these features in detail.
Overview
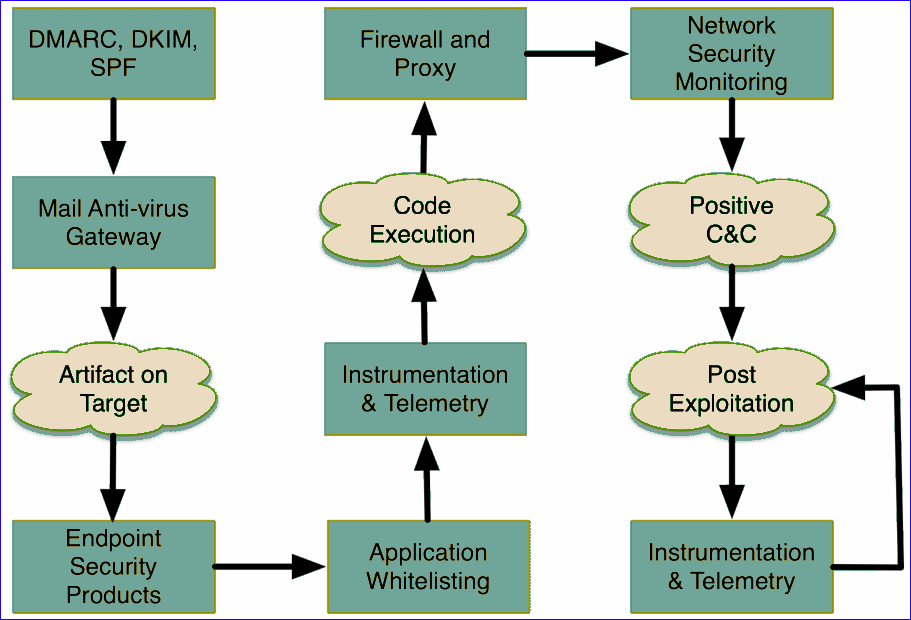
figure 1 - The Offense Problem Set
A thought-out targeted attack begins with reconnaissance. Cobalt Strike’s system profiler is a web application that maps your target’s client-side attack surface. The insights gleaned from reconnaissance will help you understand which options have the best chance of success on your target.
Weaponization is pairing a post-exploitation payload with a document or exploit that will execute it on target. Cobalt Strike has options to turn common documents into weaponized artifacts. Cobalt Strike also has options to export its post-exploitation payload, Beacon, in a variety of formats for pairing with artifacts outside of this toolset.
Use Cobalt Strike’s spear phishing tool to deliver your weaponized document to one or more people in your target’s network. Cobalt Strike’s phishing tool repurposes saved emails into pixel- perfect phishes.
Control your target’s network with Cobalt Strike’s Beacon. This post-exploitation payload uses an asynchronous "low and slow" communication pattern that’s common with advanced threat malware. Beacon will phone home over DNS, HTTP, or HTTPS. Beacon walks through common proxy configurations and calls home to multiple hosts to resist blocking.
Exercise your target’s attack attribution and analysis capability with Beacon’s Malleable Command and Control language. Reprogram Beacon to use network indicators that look like known malware or blend in with existing traffic.
Pivot into the compromised network, discover hosts, and move laterally with Beacon’s helpful automation and peer-to-peer communication over named pipes and TCP sockets. Cobalt Strike is optimized to capture trust relationships and enable lateral movement with captured credentials, password hashes, access tokens, and Kerberos tickets.
Demonstrate meaningful business risk with Cobalt Strike’s user-exploitation tools. Cobalt Strike’s workflows make it easy to deploy keystroke loggers and screenshot capture tools on compromised systems. Use browser pivoting to gain access to websites that your compromised target is logged onto with Internet Explorer. This Cobalt Strike-only technique works with most sites and bypasses two-factor authentication.
Cobalt Strike’s reporting features reconstruct the engagement for your client. Provide the network administrators an activity timeline so they may find attack indicators in their sensors. Cobalt Strike generates high quality reports that you may present to your clients as stand-alone products or use as appendices to your written narrative.
Throughout each of the above steps, you will need to understand the target environment, its defenses, and reason about the best way to meet your objectives with what is available to you. This is evasion. It is not Cobalt Strike’s goal to provide evasion out-of-the-box. Instead, the product provides flexibility, both in its potential configurations and options to execute offense actions, to allow you to adapt the product to your circumstance and objectives.