Session and Target Visualizations
Cobalt Strike has several visualizations each designed to aid a different part of your engagement. You may switch between visualizations through (Pivot Graph, Session Table, Target Table) buttons  on the toolbar or the Cobalt Strike -> Visualization menu.
on the toolbar or the Cobalt Strike -> Visualization menu.
Pivot Graph
Cobalt Strike has the ability to link multiple Beacons into a chain. These linked Beacons receive their commands and send their output through the parent Beacon in their chain. This type of chaining is useful to control which sessions egress a network and to emulate a disciplined actor who restricts their communication paths inside of a network to something plausible. This chaining of Beacons is one of the most powerful features in Cobalt Strike.
Cobalt Strike’s workflows make this chaining very easy. It’s not uncommon for Cobalt Strike operators to chain Beacons four or five levels deep on a regular basis. Without a visual aid it’s very difficult to keep track of and understand these chains. This is where the Pivot Graph comes in.
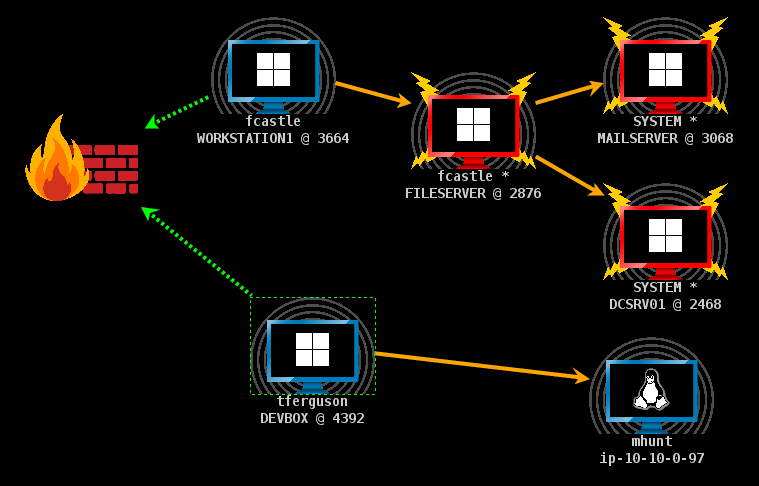
The Pivot Graph shows your Beacon chains in a natural way. Each Beacon session has an icon. As with the sessions table: the icon for each host indicates its operating system. If the icon is red with lightning bolts, the Beacon is running in a process with administrator privileges. A darker icon indicates that the Beacon session was asked to exit and it acknowledged this command.
The firewall icon represents the egress point of your Beacon payload. A dashed green line indicates the use of beaconing HTTP or HTTPS connections to leave the network. A yellow dashed line indicates the use of DNS to leave the network.
figure 12 - Cobalt Strike Graph View
An arrow connecting one Beacon session to another represents a link between two Beacons. Cobalt Strike’s Beacon uses Windows named pipes and TCP sockets to control Beacons in this peer-to-peer fashion. An orange arrow is a named pipe channel. SSH sessions use an orange arrow as well. A blue arrow is a TCP socket channel. A red (named pipe) or purple (TCP) arrow indicates that a Beacon link is broken.
Click a Beacon to select it. You may select multiple Beacons by clicking and dragging a box over the desired hosts. Press Ctrl and Shift and click to select or unselect an individual Beacon.
Right-click a Beacon to bring up a menu with available post-exploitation options.
Several keyboard shortcuts are available in the Pivot Graph.
-
Ctrl+Plus — zoom in
-
Ctrl+Minus — zoom out
-
Ctrl+0 — reset the zoom level
-
Ctrl+A — select all hosts
-
Escape — clear selection
-
Ctrl+C — arrange hosts into a circle
-
Ctrl+S — arrange hosts into a stack
-
Ctrl+H — arrange hosts into a hierarchy.
Right-click the Pivot Graph with no selected Beacons to configure the layout of this graph. This menu also has an Unlinked menu. Select Hide to hide unlinked sessions in the pivot graph. Select Show to show unlinked sessions again.
Sessions Table
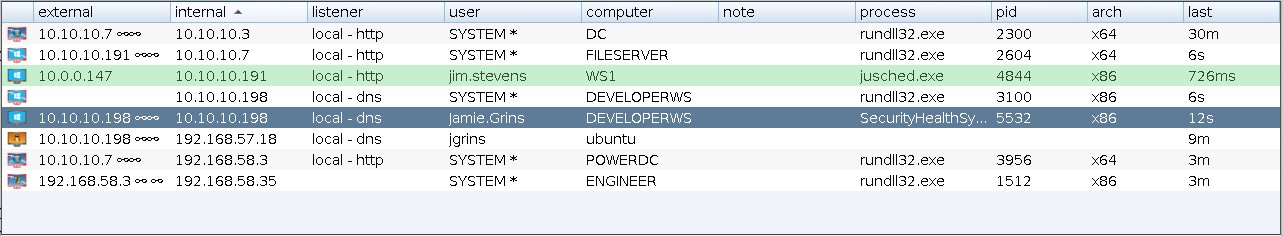
The sessions table shows which Beacons are calling home to this Cobalt Strike instance. Beacon is Cobalt Strike’s payload to emulate advanced threat actors. Here, you will see the external IP address of each Beacon, the internal IP address, the egress listener for that Beacon, when the Beacon last called home, and other information. Next to each row is an icon indicating the operating system of the compromised target. If the icon is red with lightning bolts, the Beacon is running in a process with administrator privileges. A faded icon indicates that the Beacon session was asked to exit and it acknowledged this command.
figure 13 - Cobalt Strike Beacon Management Tool
If you use a DNS Beacon listener, be aware that Cobalt Strike will not know anything about a host until it checks in for the first time. If you see an entry with a last call time and that’s it, you will need to give that Beacon its first task to see more information.
Right-click one or more Beacon’s to see your post-exploitation options.
Targets Table
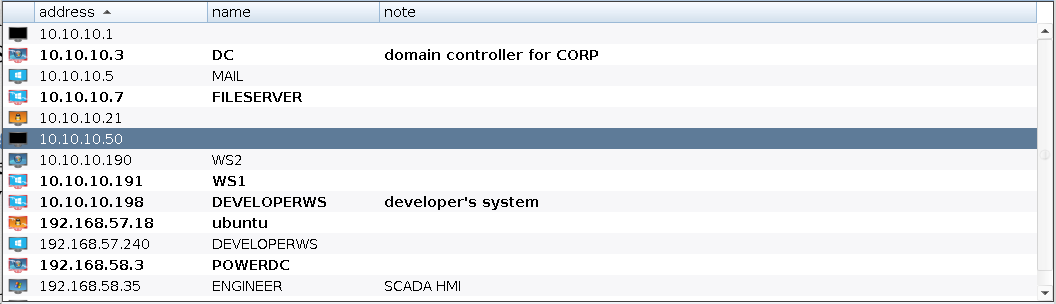
The Targets Table shows the targets in Cobalt Strike’s data model. The targets table displays the IP address of each target, its NetBIOS name, and a note that you or one of your team members assigned to the target. The icon to the left of a target indicates its operating system. A red icon with lightning bolts indicates that the target has a Cobalt Strike Beacon session associated with it.
figure 14 - Cobalt Strike Targets View
Click any of the table headers to sort the hosts. Highlight a row and right-click it to bring up a menu with options for that host. Press Ctrl and Alt and click to select and deselect individual hosts.
The target’s table is a useful for lateral movement and to understand your target’s network.