CVE and Core Impact
The Common Vulnerabilities and Exposures (CVE) is a reference of standardized names for vulnerabilities and other Information Security exposures. The goal of CVE is to standardize the names for all publicly-known vulnerabilities and security exposures.
About CVE Compatibility.
A "CVE-compatible" tool (Web site, database, or service) is one that uses CVE names in such a way that it can cross-link with other repositories that also use CVE names.
Within Core Impact, CVE names are used to uniquely identify the vulnerabilities exploited by each attack module. When the Quick Information Panel displays information about the currently selected attack, it includes an overview of the Properties and several sections including Vulnerabilities, Description, Supported Systems, etc.
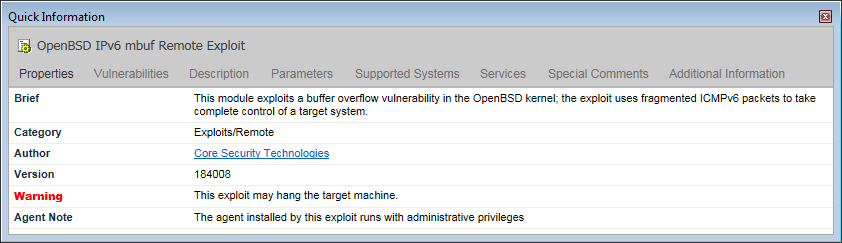
figure 65 - Quick Information Panel
The CVE name on the Vulnerabilities tab is also a link which takes you to the CVE web site for industry-derived information on the vulnerability.
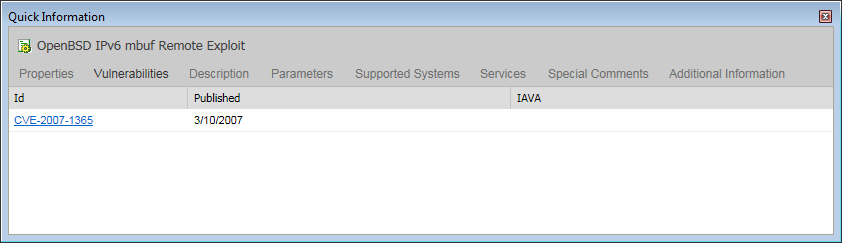
You can also search for attack modules by CVE name. To find all attacks related to a specific CVE name, select the CVE search criteria in the Search box in the Modules Panel and enter the desired name in the text box.
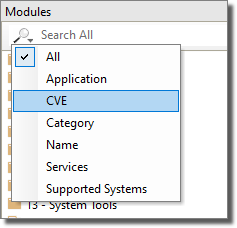
figure 66 - Modules Panel - Searching by CVE Name
See Searching for Modules for more information on how to search for modules using the Search box on the Modules Panel.
For more information regarding CVE, refer to the official CVE web site at http://cve.mitre.org.