Integration
Core Impact can import network information (OS, services, and potential vulnerabilities) from other security products, including Vulnerability Scanners. You can use individual Core Impact modules or the Vulnerability Scanner Validator Test which will quickly step you through importing your scanner data. Core Impact can also integrate with the Metasploit Framework and PowerShell Empire, increasing the overall breadth of your penetration testing program.
Integration with Metasploit
If you use Metasploit as a component of your penetration testing program, you can integrate it with Core Impact. This will allow you to use Core Impact's advanced testing features on systems that are found to be vulnerable to Metasploit exploits.
For details on how to set up Metasploit - Core Impact integration, see How to Integrate with Metasploit.
The Metasploit Framework is provided and maintained by a third party. Core Security does not support the Framework and cannot offer any guarantee as to the safety of the exploits run by the Metasploit Framework's db_autopwn functionality. Use the Metasploit Framework at your own risk.
Once Metasploit is integrated with Core Impact, there are 2 ways in which you can incorporate the functionality of the Metasploit Framework into your testing with Core Impact:
- Run Metasploit with Network Attack and Penetration RPT: As a part of the Network Attack and Penetration, Core Impact will select which exploits from the Metasploit Framework to run. You will see the output in the Module Log pane of your Core Impact Workspace and any successful exploits in the Module Output pane. Any vulnerabilities found by Metasploit will be labeled accordingly in Core Impact's Quick Information pane as well as any reports.
Quick Information with Metasploit exploit
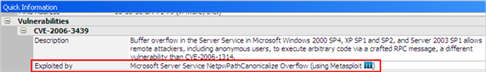 NOTE:
NOTE:This method does not require that you open a Metasploit console.
- Install CORE Impact agent from Metasploit console: With this method, Metasploit users can leverage exploit and discovered host information to add hosts and install agents in a Core Impact Workspace. Subsequently, Core Impact can be used to further explore the host or pivot from the agent to perform extensive penetration tests.
To install a Core Impact agent from a Metasploit console, follow these steps referencing the below image of a sample Metasploit session:
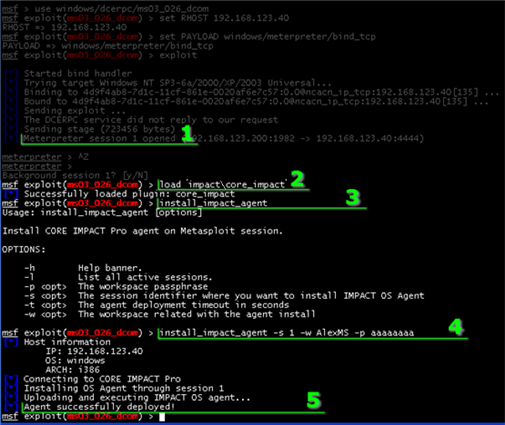
figure 67 - Install agent from Metasploit Console
- In Metasploit, you must first have a meterpreter payload connected to a host.
- Enter the command load 'impact\core_impact'. This will initialize the Core Impact plugin for the current Metasploit session.
- Enter the command install_impact_agent. This is an optional step that simply displays the parameters that should be used with the install_impact_agent command.
- Enter the command install_impact_agent with the associated parameters. In the example below, the meterpreter session (-s) is set to 1, the existing Workspace (-w) is set to AlexMS, and the Workspace's passphrase (-p) is set to aaaaaaaa.
-
The console will display a message when the agent has been deployed in Core Impact. At this point, you can open yourCore Impact Workspace and use the fully functional agent. The Metasploit session is no longer needed and can be closed.
Integration with PowerShell Empire
If you use PowerShell Empire as a component of your penetration testing program, you can integrate it with Core Impact. This will allow you to use Core Impact's advanced testing features in conjunction with PowerShell Empire's post-exploitation capabilities.
Using Core Impact with PowerShell Empire requires that both programs are running and can access one another across the network.
Before integrating your Core Impact instance with a host using PowerShell, you will need to launch the Empire REST API:
- Initiate the Empire console using the
--restoption so that the REST API will be reachable. - You can set a password on the Empire console using the
--passwordoption, but this password will then need to be entered in the Core Impact modules that are subsequently used in the integration. - Launch a listener in the Empire console using the below commands:
listener
set Name StartingListener
Run
Core Impact and PowerShell Empire can work together in 2 scenarios:
Core Impact Agent
If you have exploited a host using Core Impact and an active agent is installed on the host machine, use the following steps to leverage PowerShell Empire:
- In Core Impact, locate and run the module Deploy PowerShell Empire Agent.
- Configure the Module so that it can locate and log into the instance of PowerShell Empire.
- Once the module is running, you can use PowerShell Empire to interface with the target host, through the Core Impact agent.
PowerShell Empire Agent
If you have exploited a host manually and have an active agent installed on the host machine via PowerShell Empire, use the following steps to leverage Core Impact:
- In Core Impact, locate and run the module Install Agent using PowerShell Empire Agent.
- Configure the Module so that it can locate the instance of PowerShell Empire and the existing agent. The Agent Name will be a string of letters and numbers (e.g. VASDGF314524GWWR)
- Once the module runs, a new host will be added in Core Impact showing visibility through the PowerShell Empire host. You can now use Core Impact to interact with the agent.