Rapid Penetration Test (RPT)
Core Impact's Rapid Penetration Tests (RPT) are step-by-step automations of the penetration testing process. Core Impact allows users to perform a RPT on a variety of target types but keep in mind that Core Impact also provides test capabilities for wireless networks as well as network devices such as routers and switches. The following RPTs are available in Core Impact:
Network RPT - Scan your systems (servers, network devices, surveillance cameras etc.) for known exploits and test their vulnerability. Attempt to capture and store identities (usernames/passwords, cookies, SSH keys, etc.) from targets. Core Impact also provides a One-Step Network Risk Assessment and Vulnerability Scanner Validator Test.
Client Side RPT - Simulate social engineering attacks to test the efficacy of your user-level security. The Attack Phase is separated into Attack and Penetration (for exploit-based attacks) and Phishing, for testing the vulnerability of your user community to Phishing attacks. Also provided is a One-Step One-Step Client-side Tests.
Web Applications RPT - Evaluate the security of your web applications and make sure your organization is proactively assessing the OWASP Top 10 security risks. Core Impact also provides a One-Step WebApps Risk Assessment and Remediation Validator Test.
With any of these RPTs, the end goal is to expose the exploitable vulnerabilities in a system by penetrating and analyzing that system. The RPTs sequence through steps that automate common and repetitive tasks typical of a penetration test, such as gathering information, executing attacks, learning about compromised systems, escalating privileges, cleaning up, and generating reports.
Each step defines a high-level task that has been automated with easy-to-use wizards. If you are a new user, this basic automation mode will simplify the use of the product. If you are an expert user, RPT will allow you to execute common tasks more efficiently. Individual module selection is always available to you using the Modules View (see Working With Modules for more information).
You can run each step of the RPT process individually, but running steps in the order outlined by the Panel is highly recommended as some steps might require information obtained in a previous step. For example, Network Attack and Penetration will automatically select attacks based on what is known about the specified targets. Because this information is typically provided by Network Information Gathering, it generally makes sense to gather information before initiating the attack Wizard.
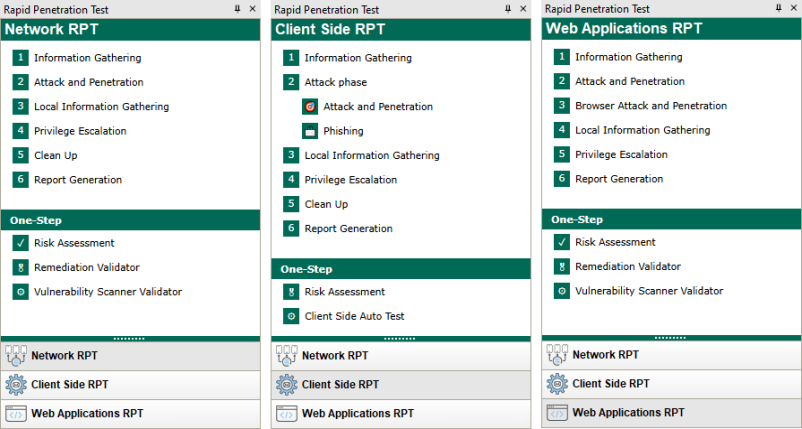
figure 9 - The Network RPT, Client Side RPT and Web Applications RPT Panels
Remember, there are many modules in Core Impact that are not executed by the RPTs but that can be very powerful when used in a comprehensive security testing program.