Privilege Escalation
The Privilege Escalation RPT step executes local privilege escalation attacks on connected agents not running as the super user or the administrator. This macro automatically selects and executes exploits from the Exploits/Local/Privilege Escalation module folder.
After successfully running Privilege Escalation, you may want to run the Local Information Gathering step to obtain more information from the compromised hosts. If an in-depth penetration test is being performed (and depending on the target network's topology), it is possible to change the current source agent and cycle back to the Information Gathering step. Refer to Set as Source for information regarding the source agent. All the initial 4 steps will execute from any Core Impact agent.
Use the following steps to run the Privilege Escalation RPT.
- Ensure that the Client-side RPT is activated.
- Click Privilege Escalation to open the wizard and press Next to start.
-
In the Agent Selection screen, specify which agents will run the Privilege Escalation macro. By default, all currently connected agents will perform this step (All agents will perform a check to see if they are already running SYSTEM or root-level access. If they are, they will not attempt to perform Privilege Escalation.) An agent name will be automatically set if the macro was dropped over a specific agent. Uncheck the All connected agents checkbox if you wish to only target that agent.
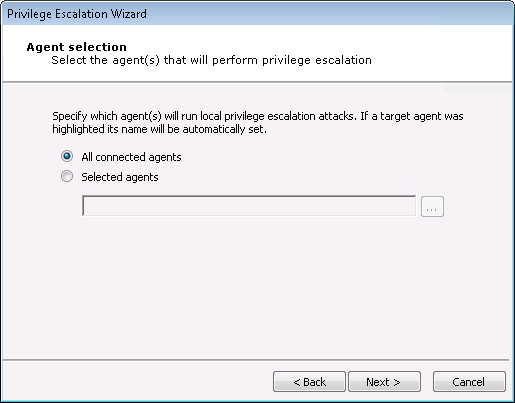
To choose a single agent other than the one displayed, or to select multiple agents on which to escalate privileges, uncheck the All connected agents checkbox and click the ellipsis (
 ) button next to the Only on agent field. Follow the prompts to select your desired agents and press Next to continue.
) button next to the Only on agent field. Follow the prompts to select your desired agents and press Next to continue. -
The Exploit Selection screen displays.
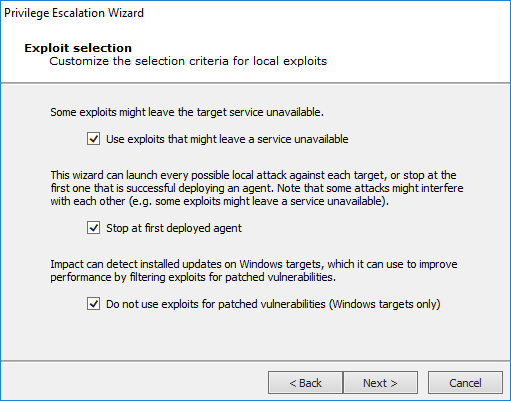
For each target host, this macro selects relevant attacks from the Exploits/Local/Privilege Escalation Module folder based on the target's platform. The default selections on the Exploit selection screen are intended to minimize the risk of exploits leaving services unavailable. For a more aggressive attack strategy, check or uncheck the appropriate checkboxes.
Press Next to continue.
-
The Exploit Configuration screen displays. Select which local modules to run after deploying new agents.
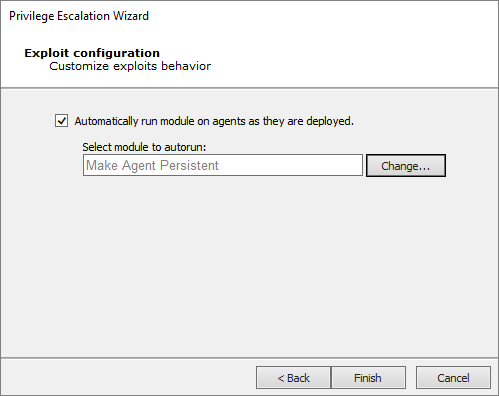
Press Finish. The module will run and information will be displayed on the Module Output and Module Log panels.