Network Device Attack and Penetration
The Network Attack and Penetration RPT can target Network Devices. Unfortunately, Network Devices often suffer from lack of attention. Administrators prioritize network up-time over device security, leaving account usernames and passwords at their default values and not keeping operating system and software sufficiently updated. Core Impact’s attack modules leverage these weaknesses and use various dictionary attacks in order to gain access to the device.
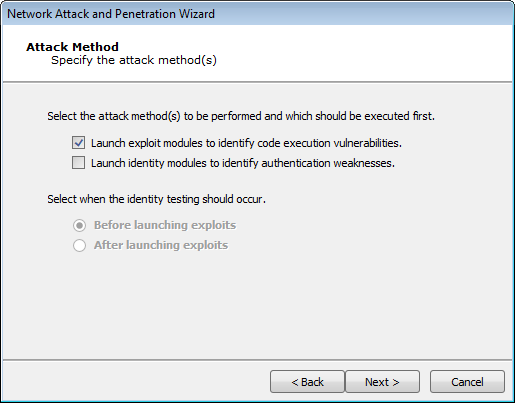
figure 13 - Attack Method
When configuring a Network Attack and Penetration using the RPT, there are 2 attack methods from which you can choose. These will result in different outcomes as they relate to testing Network Devices:
Launch exploit modules... - Core Impact will launch exploits targeted against IOS devices (as if it was another operating system, e.g. Windows). On successful attacks, an IOS Agent is installed.
Launch identity modules... - When selecting the HTTP/SNMP and Telnet on the Attack Selection form, if the target system is a router, Core Impact will install an IOS Agent.
If the Attack and Penetration step succeeds in gaining access to a network device, you will see an IOS Agent deployed under that device in the entity database. This IOS Agent represents the information of how to exploit a network device vulnerability.
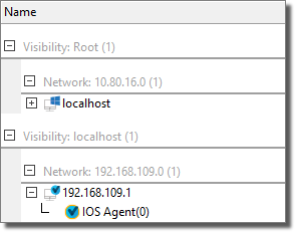
figure 14 - IOS Agent
Once an IOS agent exists in your Network view under a Network Device, you have the ability to perform post-exploit activities on the device.