Testing Network Devices
Network Devices such as routers and switches are of critical importance to the operation and security of a business’ technology environment. Not only do they relay all network traffic but they also allow networks to be connected to one another. If one of these devices is breached by an attacker, the disruption and data loss that might follow could be severe. With command of a switch, for example, an attacker could view and manipulate the data passing through it and even inject their own malicious data, creating potential for more infiltration. Likewise, with control of a router’s configuration, one could gain access to other networks that otherwise would not be detectable. Network Devices are the gateways and dispatchers to the systems you aim to protect, so their security needs to be a top priority as well.
Network Devices tests are begun in Core Impact's Network RPT, which includes options for discovering and attempting to gain access to Network Devices. Post-exploitation steps for Network Devices are performed by launching various Core Impact modules from the Modules View so, if you are not already familiar with how to run modules directly, review the section Working With Modules. Additionally, see RPT Reports for how to report on your Network Device penetration test results.
When you discover Network Devices, they will be represented in the Hosts folder of the Network tab of the Entity view as shown below.
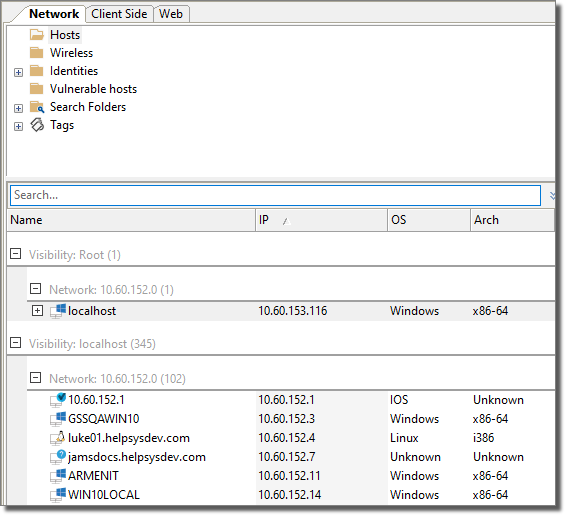
figure 12 - Network Device Entities
The below tests are specifically designed for use on Network Devices networks. The modules are available by navigating to the Modules View and searching for the module name (ensure that the Network entity tab is active).
Network Device Information Gathering
The Network Information Gathering step of Core Impact’s Network Rapid Penetration Test (RPT) will record any systems it locates within your target network, including network devices. If the RPT is able to discern the operating system of a machine and confirm it to be a network device, it will be added to your list of Network Entities with a unique icon to distinguish it from the other systems in the list. Core Impact will attempt to:
- Fingerprint found devices to determine Manufacturer, device model/type and operating system details.
- Determine the inputs on which the device accepts connections or instructions, including but not limited to SNMP, Telnet, HTTP.
You can also use the Network Discovery: Passive CDP module to listen for broadcasts from Cisco devices. This gives you another method to identify the visible devices on your network and take further steps to test their exposure to outside attack.