A3:2021 Injection
Below we document the steps to test the OWASP A3:2021 Injection security risk only. Use this test to:
- Safely identify both traditional and blind SQL injection vulnerabilities
- Dynamically create and inject SQL queries in an attempt to access the database
- Interact with the compromised database
- Detect and exploit OS Command Injection weaknesses in web applications
- Reveal the implications of a breach by taking control of the web server
Please note that you can combine tests and run more than one on a specific target or set of targets.
-
On the Risk Types dialogs of the Wizard, select A3 - Injection and any extra options.

Set any of the three options:
- Look for SQL Injection vulnerabilities
- Look for OS Command Injection Vulnerabilities
- Look for Cross Site Scripting (XSS) Vulnerabilities
-
Click Next until you are past the Risk Types selection. For the following steps ONLY A3 - Injection and its related options are selected.
-
On the SQL Injection tests dialog you select the following page parameters:
- Request parameters
- Request cookies
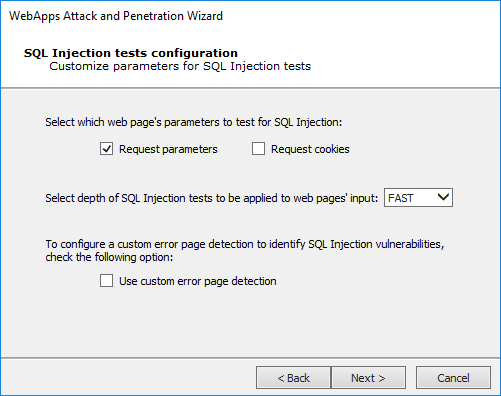
The WebApps Attack and Penetration step can exert varying levels of testing on the web page's parameters. Select the depth of the test using the drop-down menu:
FAST: quickly runs the most common tests
NORMAL: runs the tests that are in the FAST plus some additional tests
FULL: runs all tests
If you know in advance how the target web application's error pages will appear - what text will be in the body or the header - check the Use custom error page detection checkbox. You will further configure this feature in a subsequent step in the Wizard.
- Press Next to continue.
-
On the Custom error page detection configuration dialog you can add one or more rules that Core Impact will check when it receives data from the web application. Each rule can apply to the header of the document or the data content. You then can define whether the header or data does or does not contain certain text strings. For example, if you know that the web application will produce error pages that contain in the page body the sentence "We're Sorry. An unknown error occurred while processing your request. Please try again", then you could create a custom error configuration as shown.
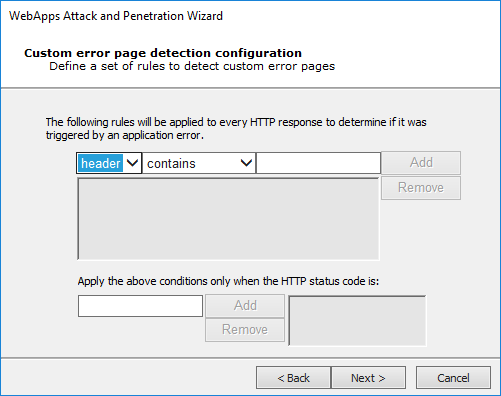
If Core Impact identifies an error page, it will then evaluate whether it (or the conditions that produced the error page) are vulnerable to SQL Injection attacks.
Use the Apply the above conditions when the HTTP status code was: list to indicate that custom error rules should only be applied if Core Impact receives a specific HTTP status code with the page.
- Press Next to continue.
-
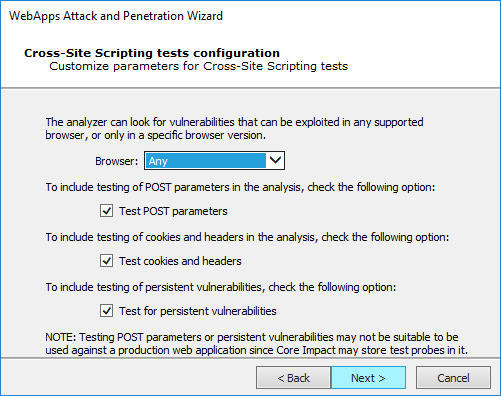
On the Cross Site Scriptig (XSS) dialog select the specific browser that you would like to target, or select Any to target all types.
If you selected Look for Sensitive Information in documents, this dialog displays to configure.
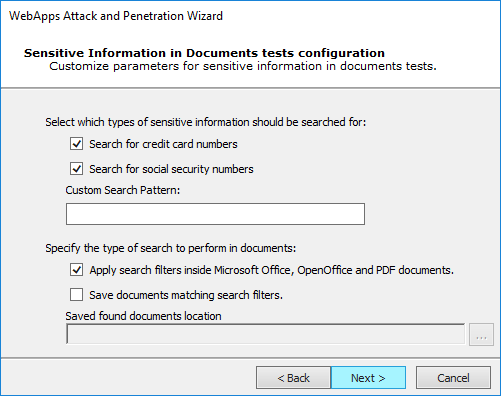
You can instruct Core Impact to Search for credit card numbers or Search for social security numbers in any documents it finds.
Additionally, add a Custom Search Pattern to help Core Impact find specific data - enter an extended regular expression and that would be run across all the HTML pages that the wizard is targeting.
Check the Apply search filters inside Microsoft Office, OpenOffice and PDF Documents option if you want the test to search inside of documents that are linked from the HTML pages.
Check the Save documents matching search filters option if you want Core Impact to save any documents where it locates sensitive data. Then provide a path where the documents should be saved.
Press Next to continue.
-
The final dialog—Session Management—displays.
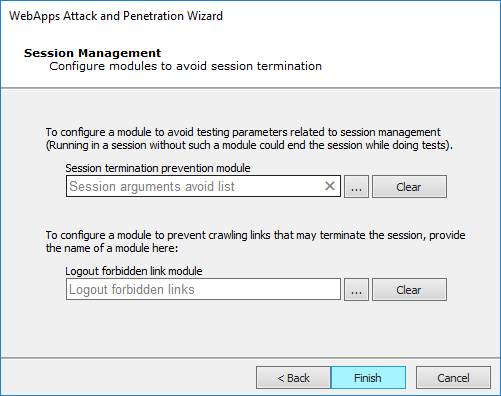
To configure a module to avoid testing pages that could terminate the session, use the ellipsis (
 ) button. By default, the Session arguments avoid list module will be enabled for this purpose. Click the Clear button if you do not want any module to perform this function.
) button. By default, the Session arguments avoid list module will be enabled for this purpose. Click the Clear button if you do not want any module to perform this function. - Click the Finish button to begin the test.
If the WebApps Attack and Penetration is successful, then WebApps Agents will appear under vulnerable pages in the Entity View. See Interacting with WebApps Agents for information about how to leverage the WebApps Agents. Additionally, if a vulnerability is found, it is assigned a Vulnerability ID which will allow Core Impact users to track reported vulnerabilities after testing. The Vulnerability ID will appear in the ''Information'' pane when the vulnerable web page is selected and also in the name of the agent that is deployed for the page.
You can extend Core Impact's functionality by writing your own custom modules. For more information about writing custom modules, please contact Customer Support (see Contact Support).
Return to WebApps Attack and Penetration.