A7:2021 Identification and Authentication Failures
Below we document the steps to test the OWASP A7:2021 Identification and Authentication Failures security risk only. Use this test to Guess usernames and passwords.
Please note that you can combine tests and run more than one on a specific target or set of targets.
- On the Risk Types dialogss of the Wizard, select A7 - Identification and Authentication Failures
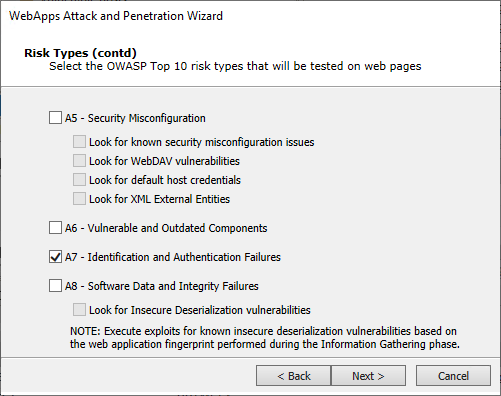
-
Click Next until you are past the Risk Types selection. For the following steps ONLY A7 - Identification and Authentication Failures and its related options are selected.
-
Authentication tests configuration dialog.
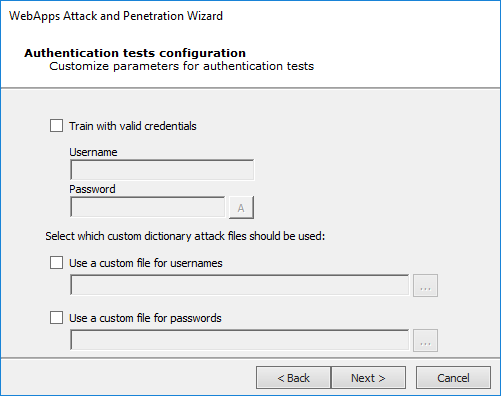
Check the Train with valid credentials box and then enter a Username and Password if you would like the RPT to log into the web application so that it can learn (be trained) how a valid login appears. Alternatively, you can select custom dictionary files from which Core Impact can draw usernames and/or passwords.
Check the Use a custom file for usernames option if you want to provide a file that contains a list of usernames the RPT can use in the test.
Check the Use a custom file for passwords option if you want to provide a file that contains a list of passwords the RPT can use in the test.
-
Press Next to continue.
If you selected Look for Sensitive Information in documents, this dialog displays to configure.
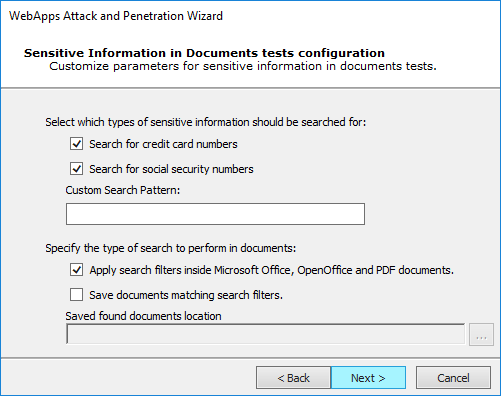
You can instruct Core Impact to Search for credit card numbers or Search for social security numbers in any documents it finds.
Additionally, add a Custom Search Pattern to help Core Impact find specific data - enter an extended regular expression and that would be run across all the HTML pages that the wizard is targeting.
Check the Apply search filters inside Microsoft Office, OpenOffice and PDF Documents option if you want the test to search inside of documents that are linked from the HTML pages.
Check the Save documents matching search filters option if you want Core Impact to save any documents where it locates sensitive data. Then provide a path where the documents should be saved.
Press Next to continue.
-
The final dialog—Session Management—displays.
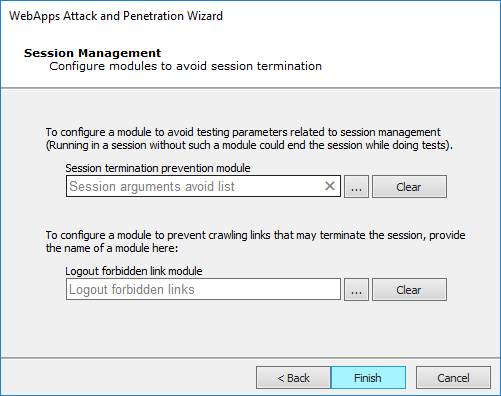
To configure a module to avoid testing pages that could terminate the session, use the ellipsis (
 ) button. By default, the Session arguments avoid list module will be enabled for this purpose. Click the Clear button if you do not want any module to perform this function.
) button. By default, the Session arguments avoid list module will be enabled for this purpose. Click the Clear button if you do not want any module to perform this function. - Click the Finish button to begin the test.
If the WebApps Attack and Penetration is successful, then WebApps Agents will appear under vulnerable pages in the Entity View. See Interacting with WebApps Agents for information about how to leverage the WebApps Agents. Additionally, if a vulnerability is found, it is assigned a Vulnerability ID which will allow Core Impact users to track reported vulnerabilities after testing. The Vulnerability ID will appear in the ''Information'' pane when the vulnerable web page is selected.
Return to WebApps Attack and Penetration.