Authenticated Scanning
An authenticated scan in Fortra VM obtains accurate vulnerability information on covered devices by authenticating to scanned devices to obtain detailed information specific to the OS, software, configuration, and missing security patches.
Authenticated Scan Configuration
Scan Credentials
Accurate security credentials must be provided kept up to date for effective authenticated scans.
These security credentials are found in the Credentials Manager under Settings in the navigation menu. Here you can add new scan credential or modify an existing entry.
For further details to add, edit, or delete scan credentials, see Scanning.
Scan Policy
Once the necessary credentials have been logged in the Credentials Manager, they can be associated to customized scan policies. Scan Policies define for the scanner the terms by which to process the scan through selected scan speed, ports, scan credentials, password auditing, and vulnerabilities to include or exclude.
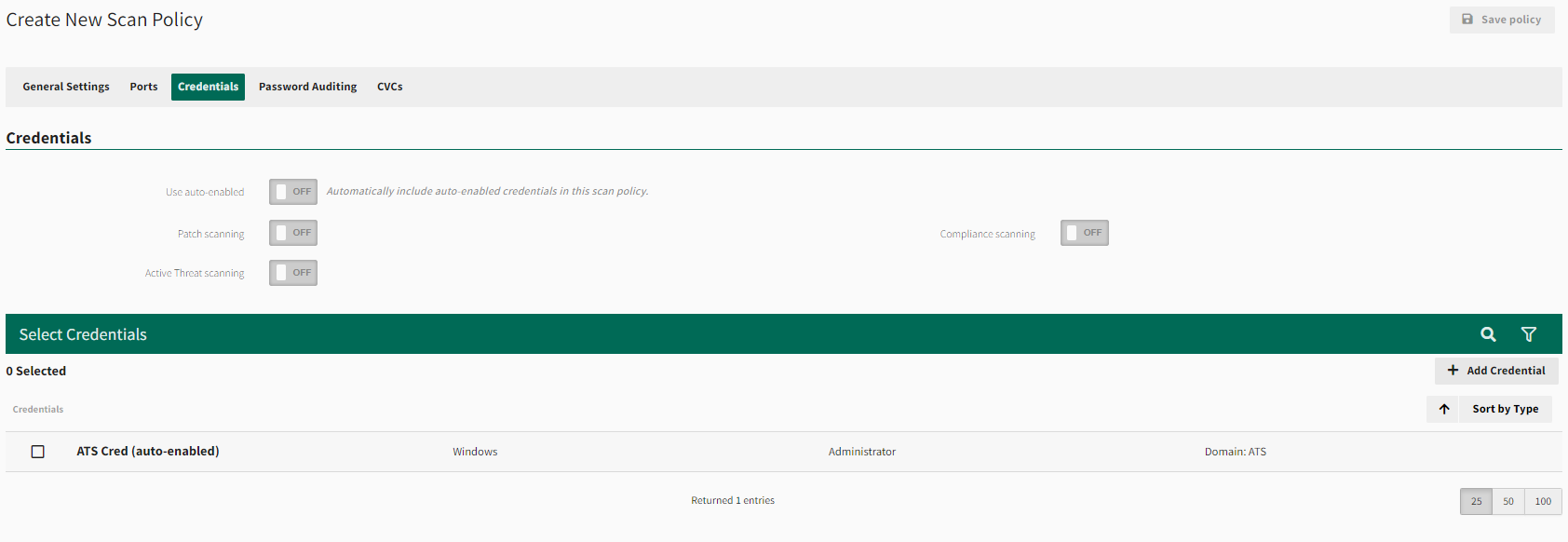
For authenticated scans, ensure the Credentials tab is properly configured when creating or modifying a scan policy. Here you will find options to select toggles to indicate credential needs, and a list of available credentials will appear where you can select with check-marks the credentials associated with this scan policy. If no credentials are available a message will display prompting you to Add Credential, shown below.
For details on creating, editing and deleting scan policies, see Scanning.
Authenticated Scan Results
From the navigation menu locate Scan Activity, under Scans. In Recent Scan Activity, Fortra VM provides icons to indicate the success or failure of authenticated scans. Circled numbers to the right of the scan status bar display the number of assets scanned. Additionally, four dashes are replaced with circled number indicators for authenticated scans. Hover over each of the circled number indicators and Fortra VM will display a call-out describing the type of authenticated scan (OS, DB, CIS, and Threat Scan) and the number of assessed, failed, and unassessed assets for each.
Use the funnel icon to search through all scan activity by filtering for authenticated scan outputs for OS, DB, CIS, and Threat Scans.
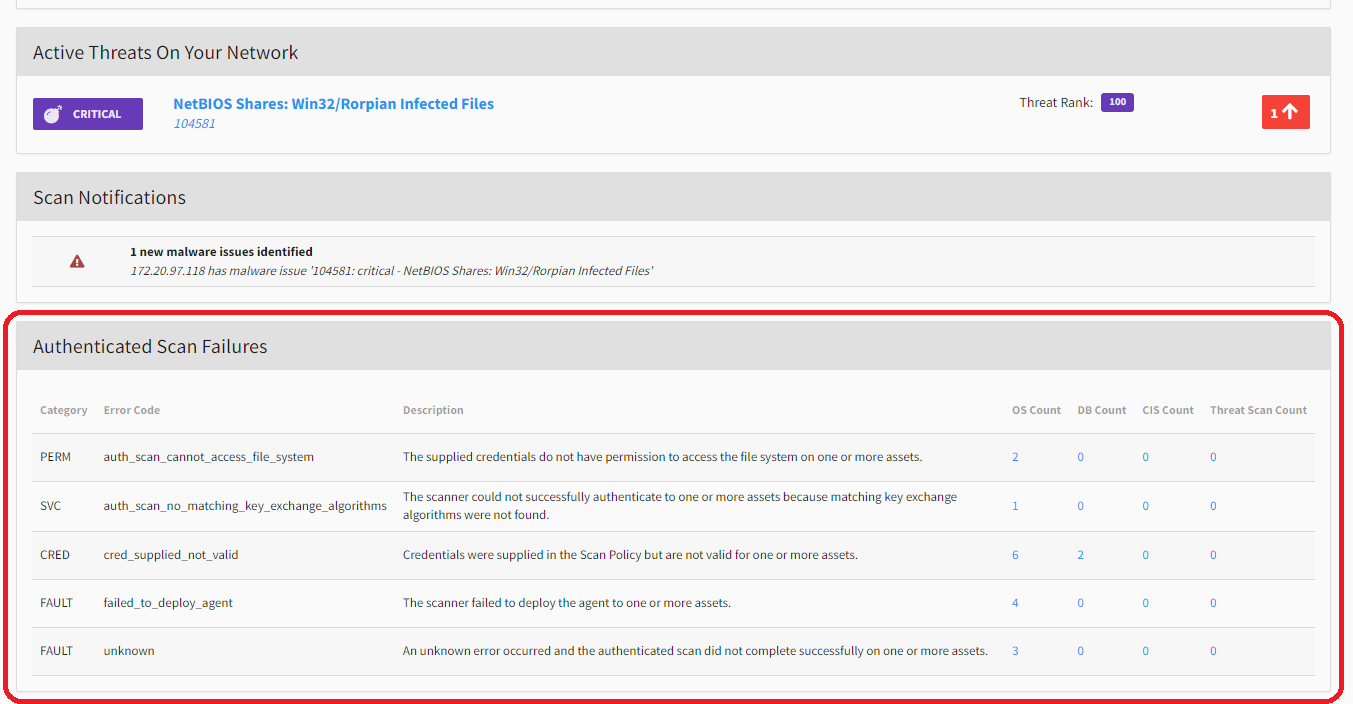
When an authenticated scan is selected, the scan details features an informational box for Authenticated Scan Failures. The error(s) causing scan failure are displayed with descriptions and asset counts for ease of error correction. Additionally, click on the asset counts to drill-down to see the assets for which the authenticated scan failure occurred.
Frequently Asked Questions
Credentials are required for authenticated scanning (a scan policy option). These are predefined by client account users and allow the scanners to perform deeper inspections by accessing system services as permitted by each specific set of credentials. Credentials can be created for scanning Windows- and Linux-based assets or to scan MSSQL, MySQL, Oracle, and PostgreSQL servers.
Running an authenticated scan is as simple as adding credentials to the desired scan policy, turning authenticated scanning on within the scan policy, and then choosing that scan policy to be used by a scan. In general, authentication credentials can be created in the scan policy or in the Credentials Manager (accessed by selecting Scan Settings > Scan Credentials ). All credentials are centrally managed, so no matter where they are added, they only need to be configured once and then can be used many times. Authenticated scans will only be performed by internal scanners. See more: Scanning
Fortra VM supports authenticated scanning of Windows and certain Linux distributions and network devices.
For Windows:
Generally the easiest way for authenticated scans to run properly is to use a Windows account that is part of your domain administrators group in Active Directory (AD). This is because the account must have full administrative access to the asset being scanned. It also means full read/write access to the ADMIN$ and C$ shares. By default, members of the domain administrators group have this level of access. It is recommended you create a unique user in AD that is dedicated only to running authenticated scans. Then, add the user to the domain administrators group. It is not recommended to use an existing domain administrator account since customers may wish to track scanning activity and log in attempts. Additionally, some customers may prefer to disable the scanning account after their scans have completed and only have it enabled when scans are run.
-
The scanner must also be able to connect to TCP port 445 for authenticated scanning of Windows assets.
-
If the host is not connected to AD, you can use WORKGROUP as the domain to configure credentials in Fortra VM. However, port 445,
ADMIN$, andC$shares must remain accessible.
For Linux and network devices:
To authenticate Linux devices joined to Active Directory (AD), the username must be entered in the format of user@domain.com in Fortra VM.
All Linux authenticated scans (SSH Key and SSH Password authentication types) require root user or a user with root equivalent privileges to successfully scan the host. Alternatively, a non-root user with full passwordless sudo privileges will work.
Fortra VM supports scanning recent versions of RedHat Enterprise Linux, Ubuntu Linux, Amazon Linux, CentOS Linux, Oracle Linux, Solaris 10, Palo Alto PAN-OS, Debian Linux, Cisco IOS, Cisco NXOS, Cisco IOS-XE, and Cisco ASA.
In the event that a user has passwordless sudo privileges, use the following steps to ensure the user does not require tty (terminal/shell) to execute sudo commands by way of ssh:
-
Open the /etc/sudoers file.
-
Find the line "Defaults requiretty".
-
Change the line to "Defaults:user !requiretty".
Where "user" is the username for the authenticated scanning.
-
Save and close the file.
SSH auth scanning should now be successful unless there are any other interfering asset configurations.
For Azure AD hosts:
Azure AD based authentication is possible by supplying the domain as "AzureAD" and then typically an email address for the username for the user in Azure AD.
Fortra VM supports SSH keys generated via the OpenSSH ssh-keygen tool.
To generate a new public/private key pair, run ssh-keygen on the command line and enter all required details.
If you choose to create a pass-phrase for your private key, you need to provide that when you create your credentials in Fortra VM.
For public/private keys to work for authentication, your public key must be present on the Linux assets you want to scan using this method.
When supplying your private key to Fortra VM, the only supported format is PEM. Copy and paste the private key contents into the SSH key field when creating the Fortra VM credentials.
For example:
ssh-keygen -m PEM -t rsa -b 2048
Your key contents should look similar to the following sample private key:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,26BA68C433201A2D268698B665980D7F
nQ2+ZIGpGAPtZfNtHq7RQiLfO+lQGst21TptLfUGHDb/EeKuv7a05s/4amNs4fw/
gg0CM9j30A/TZyg2s065f1fTkucQHiPjxNmJf5pflg2AaIupcTJZi9vDUIV7ucEi
EIDdb7lbcKp5QvEfEZWnhXUrxvIBbcT0AP5IQEpkiQh6mWkwHNE5erxzX/T5nph1
T0U5h7c8x9kYZFApKbiTVQskbuojxyQ9qDKJ+KtiKnkhoN2RNDHbksD3294TDACD
gt271s3QJ10/G3qL2so40+gNkOXCsKA8AxbM29WJf42QPSv0tnabJmJIvAFxnKD/
E0+xD/VzMz7B5fOKf7ioAU1QR4q5XR42Hg+zcpboc9Ge4swlTqARujn1cvxfBRSz
XN07lAM9vWBRjJ88QqncoAyyjj/MKRS8zZCrvuypHN855EyJf1pu9wTrTUy6ZbxP
sEQbAHsW4/IeqIH2H6NS82TEsUC4o2zUV9fFj30aSLSevG/+ELbOrJMzffx+fknc
xnwm+syWnFcSuT+XRovGg9HFz0HoQQ6gqa+pllhr7mUAijjHIgAGpUSc1KOsRBR3
o2AAubJnc9l2BNJHJOqQLUcGq4GERWIiw4X4MQTPdYufMsAscsUVbl3S9wUIVc8C
tA8hbaCVJBWoAj9mjVtp/2GD7almwJujnUqSKkzDJ8BUrhrbiOY+KIYzRNSYOauS
WSXH5sB5d2FpOAfxVOTzDAsyatLHfnaeNRA4jF4+P7eX9DPHXiH1ElbNF4J+HLXd
hejrKbvOjstRw3OTx8zfrm76NNxliDTvx2Y4IV5HDl8RjDIq+VbfYYcOCT5Ui1Nk
rHPz5HlbeZfpy7hyBPADaoxt7USzcRHyvhJYtrgvkjS7VL6QhEIEVF8wraRBYCai
Rn3vxTjfpccKRAjEJZmEUCBoPxcMP76p81qrrf4yE9e8q0QRFVwvnqZDCH3EM27l
8E12GF8vdWw2sRFT6ePSpsstflv3wpyx+buGYFLuL8buqXCZY6jLVdeHWCBNoIbE
VYowhq/qxWr5LeYG38PHmSULsDJX8oZTEg0tj1jVhrYOxhx8N9l2V825gbmAYwI1
3YzLPGQKEBM72SjxoGhR+VvZL3uica7XQrpg0PQOJ3coJP7qevWJ/neJJMGuBh9k
ILuVgQVjC/eHUkp+djtyBSx3cIFfqoyYwMiW+QyEut4raR/NBsNsRwQa8Ud6PuBt
ofCMUazO6COdTKFquWU/OsP7w16DYrwB/oUDn8CxdqWKUWUgaivxVYnUyGohTwSs
Gb/sTrv2hrlpBtBRavODfdiw0LT5MALVa5nutacTOFCEUMMfz7HWpsQuMFlWDsxH
TTqjNXsuMoVm2gLrlyDFiRrshTOFELK79dmz2dxv2KdEVSeJMr88bPh2x4AVCi9G
Xi0JzeeBjsFz/ziii/NTE96Euz0QvTn6mdz+OUH0M7vG0hOgTIEad4QDy/mARMq2
vvIcp8yifddzRLzUg+4hnoDhuW6NfMj65j2s6d73KTu5VbM34izxQ5yU5abUe7Yy
PLx+ptEy69kgg0kysAqJP5sI2ZD0+FVFiKSESM2E2sOmnjYvXP60Fh84HLbCF4CG
-----END RSA PRIVATE KEY-----Finally, remember that if you created a passphrase for your private key, you must enter that into the Passphrase field when creating the Fortra VM credentials. If you chose not to create a pass-phrase for the private key, you can leave the Passphrase field blank.
Perform the following steps:
- Log in to your primary domain controller that manages the domain where the assets you want to scan reside.
- Open the Active Directory Users and Computers MMC snap-in.
-
Create a new user (for example, myfortravmscanner) and set a password.
NOTE: To avoid authentication issues, do not use control codes or other potential unicode characters for the password. - Select the newly created user, and then right click on it to open Properties.
- Under Properties, select Member Of. Select the Add option to add the user to the Domain Admins group, and the select OK to save the changes.
- Verify the new account works properly by testing whether or not you can log in to one of the assets to be scanned.
It is possible to run Windows authenticated scans without a Domain Administrator Account. To do so, a regular domain user account must be created and granted local administrator access on every Windows asset that is to be scanned. The local administrators on the asset must have permission to access the ADMIN$ and C$ shares. This approach to Windows authenticated scans is good if you only have a select number of assets you want to run authenticated scans on.
Yes.
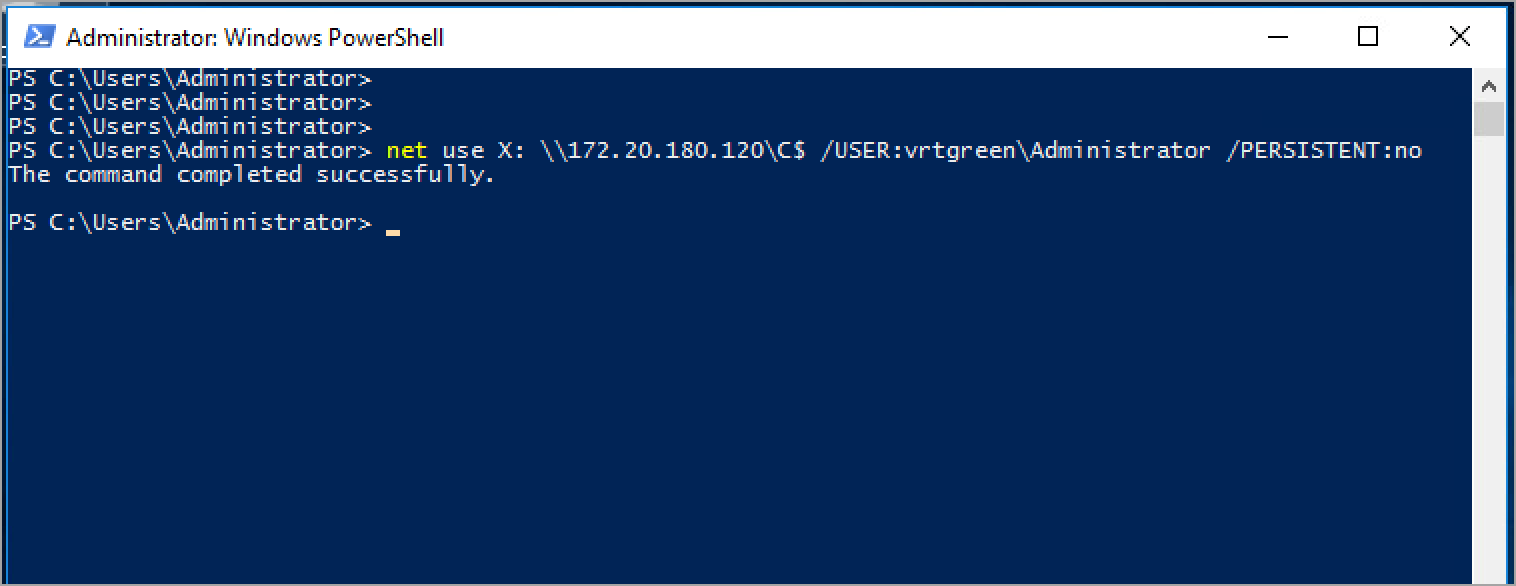
By entering the following command from a Windows machine against a target asset in PowerShell:
net use X: \\ip-address\C$ /USER:mydomain\myusername /PERSISTENT:no
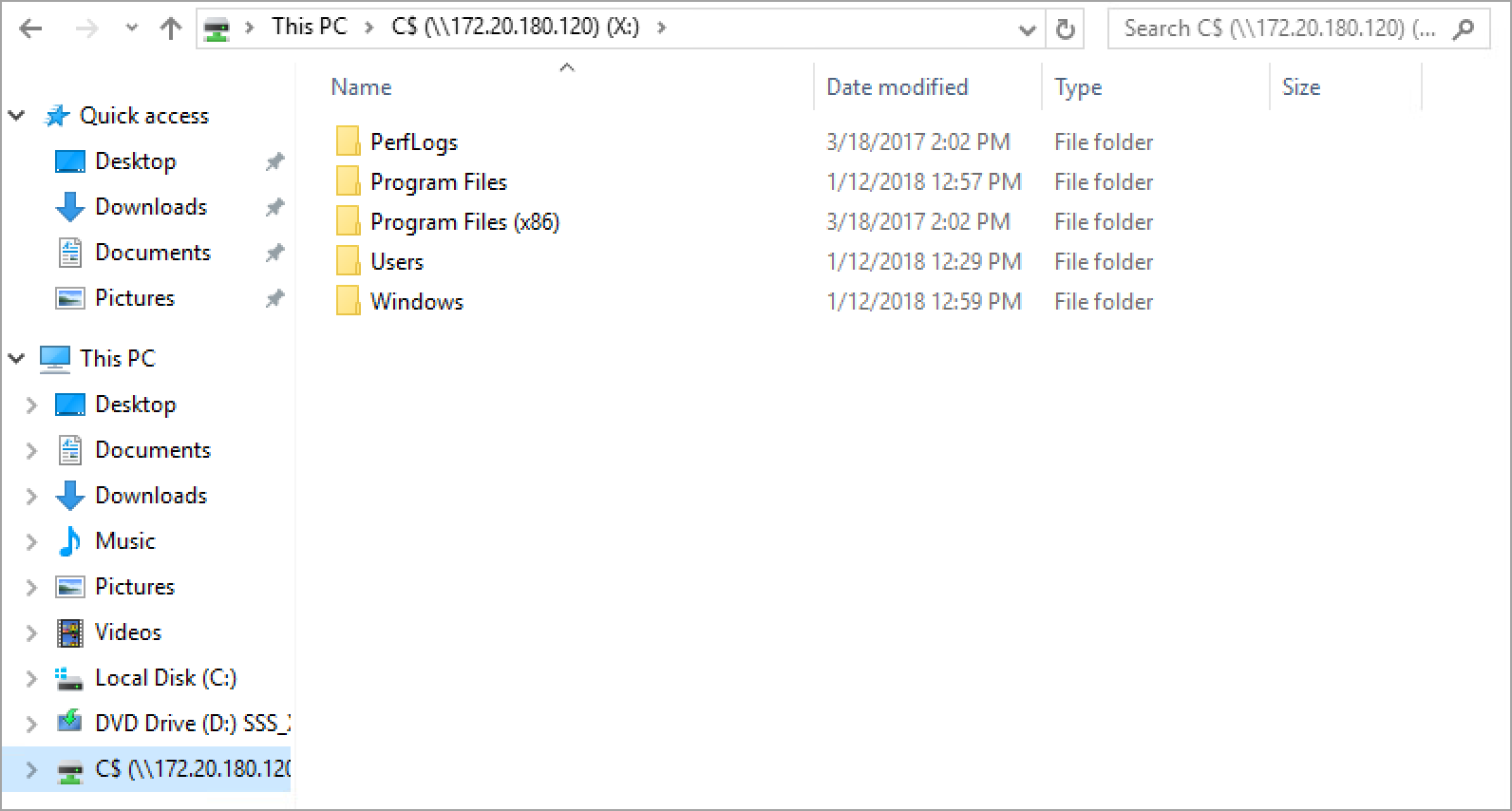
Once the command has been executed successfully, you can verify the remote access to the drive by using Windows Explorer (Microsoft Edge).
If the command succeeds, the credentials provided should be able to scan the asset’s IP address during a Fortra VM vulnerability scan.
Yes.
To verify the credentials on Linux, run the following command:
ssh <username>@<target IP> sudo -n id
Example: ssh user@10.10.0.1 sudo -n id
After running the id command, verify that the results are returned without requiring a sudo password and without any errors. The output should appear as follows, but may vary slightly:
uid=0(root) gid=0(root) groups=0(root)
You can add as many credentials as you need for each domain. When Fortra VM launches your scan, the scanner intelligently determines which domain credentials are required to authenticate to the asset being scanned.
If an invalid password is supplied in Fortra VM for a valid domain account, the account ultimately will be locked out. Make sure the password is correctly entered. If you wish to confirm that your credentials are valid and working properly, you can set up and run an authenticated scan against a single asset in your domain to see if the scanner is able to authenticate successfully.
Fortra VM incorporates a proprietary distributed GPG key pair technology that encrypts user-scanning credentials upon entry with RSA 2,048-bit public-key technology. Once encrypted, credentials can only be decrypted by the corresponding private key of the customer’s scanning appliances (Fortra VM only stores the public key). This ensures any sensitive credential sets are limited in scope to the customer devices they apply to. In summary, Fortra cannot see or alter your credentials, and what you enter into Fortra VM exists only as an encrypted block of data.
Fortra VM utilizes a proprietary dissolving scanning agent for Windows-authenticated scans. The dissolving agent is a small win32 PE file, named fvmscan.exe, that is deployed to the Windows directory and launched via a service created and immediately removed. This is the standard method of remotely executing a program on a Windows asset. The dissolvable agent allows Fortra VM to gather asset-specific details such as Windows patches, installed software, and other environment details. The agent communicates with the scanner via RPC over SMB to avoid having to allow any ports through the asset firewall. All collected details that are reported back to the scanner are encrypted before being transmitted. At the conclusion of the asset scan, the agent automatically removes itself (aka dissolves) from the system. Observing Windows logs relating to service creation and deletion are normal and should be expected during an authenticated scan.
Utilize Fortra VM’s CIS Benchmark Scanning to verify your compliance with industry standard security best practices. For more information, see CIS Benchmark Scanning.