Security GPA
Developed by Fortra, the Fortra VMSecurity GPA provides a simplified assessment of your environment’s internal and external security posture. Like a grade point average in school, the higher your Security GPA, the better your security posture.
Based on the number and severity level of vulnerabilities discovered, the Security GPA reflects even the smallest changes to your environment that other vulnerability management systems often do not. For example, if a domain controller’s security rating improves even just slightly, your Security GPA typically goes up. This helps you quickly identify problem areas and see almost immediate progress as vulnerabilities are resolved.
Other vulnerability management systems also often weigh noncritical devices (such as printers and voice over IP [VoIP] phones) in a way that negatively affects your overall posture, even if those assets are not critical to your business. The Security GPA, meanwhile, understands which systems are important to you and rates those accordingly.
How is It Calculated?
The Security GPA is the weighted average of your asset ratings. By default, Fortra VM weighs an asset’s risk to your environment based on its type (for example, servers, workstations).
When an asset belongs to more than one asset group, Fortra VM uses the group with the most severe risk weight when calculating your Security GPA. This allows you to apply weighted averages to broad types of assets in addition to custom, critically weighted assets groups important to your organization.
Security GPA ratings
| Rating | Description |
|---|---|

|
The weighted average of your asset ratings is 0.00–0.33. |

|
The weighted average of your asset ratings is 0.34–0.67. |

|
The weighted average of your asset ratings is 0.68–1.00. |

|
The weighted average of your asset ratings is 1.01–1.33. |

|
The weighted average of your asset ratings is 1.34–1.67. |

|
The weighted average of your asset ratings is 1.68–2.00. |

|
The weighted average of your asset ratings is 2.01–2.33. |

|
The weighted average of your asset ratings is 2.34–2.67. |

|
The weighted average of your asset ratings is 2.68–3.00. |

|
The weighted average of your asset ratings is 3.01–3.33. |

|
The weighted average of your asset ratings is 3.34–3.67. |

|
The weighted average of your asset ratings is 3.68–4.00. |
Vulnerability severity levels
A vulnerability is a known and unknown defect in an asset’s hardware, software, or configuration. Attackers exploit vulnerabilities to get information from, or gain access to, assets. Fortra VM determines the severity level of a vulnerability based on the effect an attack would have on an asset’s confidentiality, integrity, and availability.
| Severity Level | Description |
|---|---|

|
If exploited, an attacker will gain complete control of the affected asset. Critical-level vulnerabilities are known to have publicly accessible exploits that require little-to-no expert knowledge to use. In some cases, the presence of critical-level vulnerabilities indicates the asset is already compromised. These vulnerabilities must be resolved immediately. |

|
If exploited, an attacker can gain user or administrative access to the affected asset and run commands, access or delete files, and launch attacks against other assets. High-level vulnerabilities often require some expert knowledge to exploit, and publicly accessible exploits may not be available. These vulnerabilities should be resolved as soon as possible. |

|
If exploited, an attacker will gain valuable information to help access the asset. In many cases, medium-level vulnerabilities are the result of improperly configured services, weak or absent security configurations, or unprotected limited access accounts. These vulnerabilities should be addressed reasonably quickly. |

|
If exploited, an attacker can gain information, but not necessarily enough to access the asset. Low-level vulnerabilities can usually be addressed by applying security hardening practices or disabling services. |

|
If exploited, an attacker can gain information, but it should not be enough to access the asset. In many cases, trivial-level vulnerabilities have no possible solution due to operating system limitations and pose a minimal risk to the asset’s security. |

|
Information provided by an asset or service that is not considered a vulnerability. |
Asset Ratings
Fortra VM assigns your asset’s ratings based on the highest-level vulnerabilities discovered on the asset.
Asset ratings uses a compliant-by-default model, which means only vulnerabilities discovered during your scans are factored into an asset’s rating. (Some scan policies, for example, are for information-only reconnaissance checks [for example, host discovery, port scan], in which case Fortra VM would apply an A rating to the assets within the scope of those scans.)
During an individual scan, an asset’s rating is based on the vulnerabilities detected during that scan. Active View, meanwhile, provides a comprehensive rating based on vulnerabilities discovered from all scans on the asset.
See related: Active View - Overview
| Rating | Description |
|---|---|

|
Asset has one or more critical-level vulnerabilities. |

|
Asset has one or more high-level vulnerabilities. |

|
Asset has one or more medium-level vulnerabilities. |

|
Asset has one or more low-level vulnerabilities. |

|
Asset has 0 or more trivial-level vulnerabilities. |
Cloud GPA
Because Fortra VM is a multi-tenant platform; user data is aggregated to give you an anonymous view for comparing your GPA against everyone else on the system.
We know that not all vulnerabilities have the same remediation cycle. With SLA GPA, we introduced a self-defined grace period. SLA GPA works well for organizations that are unable to remediate quickly due to their internal processes, such as complex change control requirements or patch management programs that involve testing before a patched vulnerability is deployed.
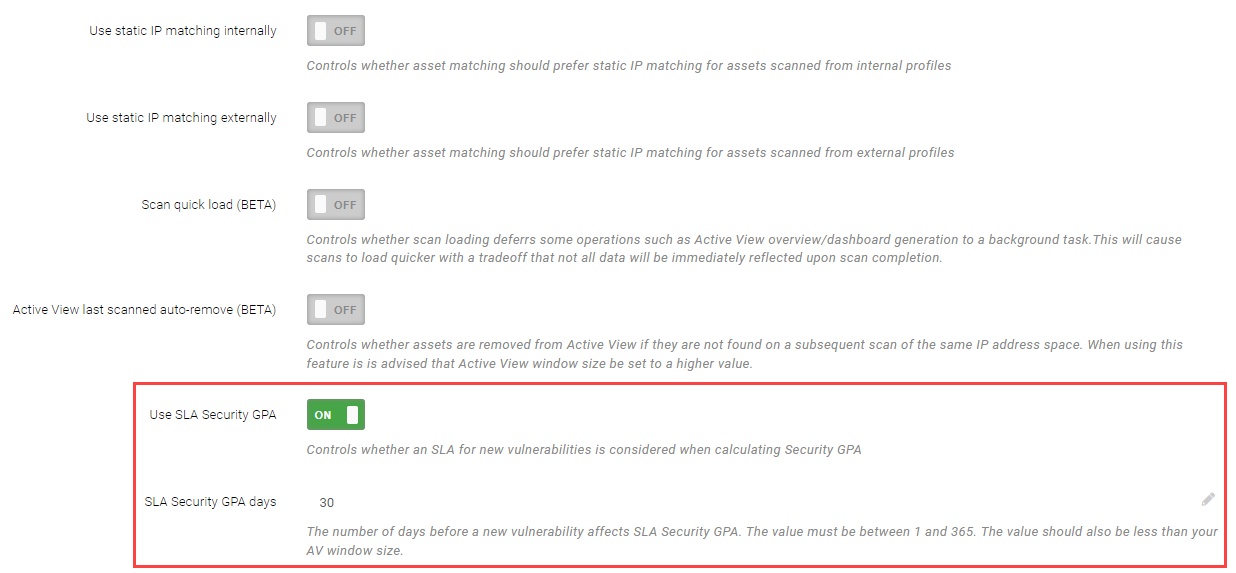
Set the SLA GPA cadence by selecting Scan Settings > Settings, and then under the Matching and Trending header, find the toggle for Use SLA Security GPA. If the toggle is switched to ON, a setting option will display named SLA Security GPA days. Enter a value for the number of days needed before vulnerabilities are attributed to your GPA. With this option engaged, your GPA will better reflect the effectiveness of your organization's policies and remediation practices.
Insight Peer Comparison
An on-demand report that gives you a visual comparison of your security program in contrast to organizations in your same industry as well as by company size. Using Security GPA, you can determine how your security posture aligns with like organizations.