Expiring Passwords at the Site Level
EFT Server's HS-PCI module provides the option to expire passwords.
If you do not activate
the HS-PCI module, this feature is disabled after the 30-day trial
expires.
On HS-PCI-enabled Sites, users are forced to change their passwords
on first use. Each day it also checks whether passwords are <n>
days from expiration, and those passwords are flagged for reminders, if
reminders are enabled. All reminder e-mail messages are sent immediately
after flagging the accounts to be reminded.
You can enable the password reset page while disallowing general access
to HTTP or HTTPS. When a new user logs in to EFT Server via the HTTP or
HTTPS index page, EFT Server redirects the user to the reset page. After
the user creates a new password, they are returned to the index page.
|

|
Password initial reset, expiration, and account management
features only apply to GlobalSCAPE and ODBC authentication Sites. These
options are not available if other authentication types (AD, LDAP, etc.)
are used. Password security features all apply at the Server level, not
to individual accounts.
There is no way to ask FTP users to change their password prior to logging
in. EFT Server allows them to authenticate, but then prevents any further
interaction with their session until they change their password. |
To configure the Site to expire passwords after a specific
number of days
In EFT Administrator, connect
to EFT Server and click the Server
tab.
In the left pane, click the Site that you want to configure.
In
the right pane, click the Site Options
tab.
Next
to Allow users to reset their passwords,
click Advanced. The Reset
Password Settings dialog box appears.
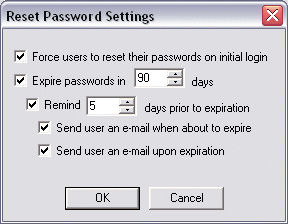
Select
the Expire passwords in <n> days
check box and specify the number of days.
|

|
For HS-PCI-enabled Sites, the number of days is set
by default to 90 days. If you attempt to change it to fewer than 90 days,
or if you clear the check box, a warning message appears. |
Click Apply to
save the changes on EFT Server.
The text of the password expired message, below, is stored
by default in C:\Program Files\GlobalSCAPE\EFT\PasswordResetMsg.html.
%full_name%, The password for account: %username% has expired.
Please change your password at your earliest convenience. Instructions
for changing your password via FTP, SFTP, and HTTP/S are provided below
for your convenience: 1. Please enter the following URL into your browser:
%reset_page% 2. Supply your current password when prompted 3. Enter your
new password and confirm 4. If approved, exit the browser and login as
normal.
The text of the password expiration reminder message, below, is stored
by default in C:\Program Files\GlobalSCAPE\EFT\PasswordResetReminderMsg.html
.
%
full_name%, The password for account: %username% will expire in
%days_left% days. Please change your password at your earliest convenience.
Instructions for changing your password via FTP, SFTP, and HTTP/S are
provided below for your convenience: 1. Please enter the following URL
into your browser: %reset_page% 2. Supply your current password when prompted
3. Enter your new password and confirm 4. If approved, exit the browser
and login as normal.
|

|
You can edit the HTML file for the password messages;
however, be sure not to change the variables. |
When a password is reset,
EFT Server verifies the new password against complexity criteria and password history, if those features are
enabled. Users are not allowed to proceed with their session until a password
is created and accepted by the system. If the password is not accepted
by the system:
- In HTTPS and SFTP, the authentication request will
be denied.
- In FTP, no further FTP commands will be accepted
until a new password is provided that meets complexity and
password history requirements,
if those features are enabled.
For HS-PCI-Enabled
Sites:
PCI DSS requirement 8.5.3 states
that you should set first-time passwords to a unique value for each user
and force users to change their password immediately after the first use.
PCI DSS requirement 8.5.9 states
that users should change their passwords at least every 90 days.
PCI DSS requirement 8.5.8 states
that you should generate unique passwords for each user. These requirements
apply to both end users and administrators.
PCI DSS requirement 8.5.10 states
that you should generate strong passwords. Manual entry of passwords is
disallowed in the Create New User and
Change Password dialog boxes;
users and administrators are forced to generate
complex passwords by clicking Generate,
to avoid the possibility of reusing the same password.
If a Site
is running in PCI Compliance mode, the warnings appear in the following
situations:
![]()
