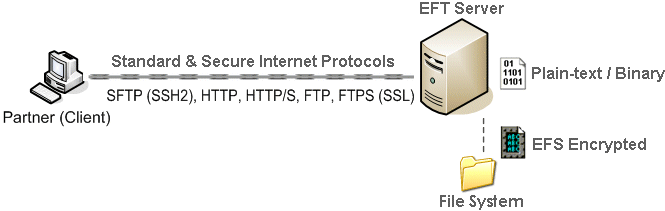
Files stored on the disk in EFT Server's Virtual File System can be transparently encrypted during read/write. Data is encrypted as it is written to disk, and decrypted prior to transmission.

|
|
If you turn on this feature, it is recommended that you
set up appropriate back-up measures to protect your data. If you need
to recover a private key (The server's private key decrypts the client's session. The private
key has a .key extension and is part of the public-private key pair.)
to decrypt data, and that key is lost, you will not be able to recover
the data that the key protects. Streaming repository encryption leverages
Microsoft's EFS. If you need more information on setting up appropriate
back-up procedures, see Best
Practices for Configuration and Validation. |
The PCI DSS (Multifaceted security standard that includes requirements for security management, policies, procedures, network architecture, software design, and other critical protective measures.) requires that if disk encryption is used (rather than file- or column-level database encryption), logical access must be managed independently of native operating system access control mechanisms (for example, by not using local system or Active Directory accounts). Decryption keys must not be tied to user accounts. That does not mean EFS Encryption cannot be used at all, but rather that it cannot be used as the sole mechanism for repository encryption. For this reason, EFT Server will only warn, rather than fail, during an audit.
To enable streaming repository encryption
In EFT Administrator, connect to EFT Server and click the VFS tab.
In the left pane, right-click the parent folder you want to configure, then click Encrypt Contents.
Click OK.