Many organizations lack the in-house expertise or resources to implement, ensure, and enforce compliance throughout their organization, or need mechanisms to quickly bring them into compliance and maintain that compliance with minimal overhead.
The HS-PCI module facilitates compliance with the PCI DSS 1.1 specification for new and existing customers. The PCI DSS Requirements section provides an overview of each requirement and describes how the HS-PCI module helps comply with the requirement.
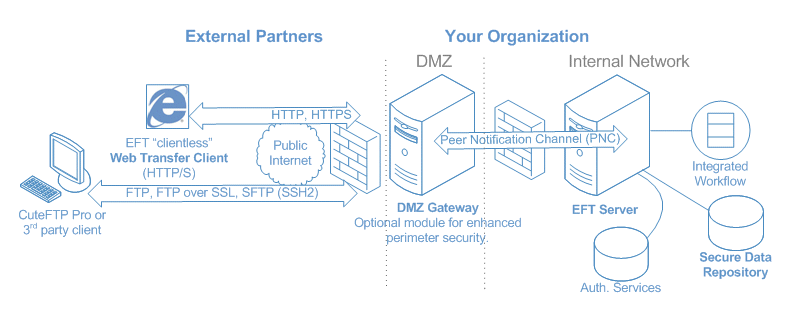
Protecting cardholder data is a major aspect of complying with the PCI DSS. The HS-PCI Module, in concert with DMZ Gateway server, helps organizations comply with data storage requirements, including not storing data in the DMZ, using repository encryption, and securely sanitizing deleted data so that it cannot be reconstituted.

The HS-PCI module protects data in transit by enforcing the use of secure protocols, strong ciphers and encryption keys, and maintaining password policies that strictly follow PCI DSS guidelines.
EFT Server lets you "fine tune" user access to help you comply with PCI DSS requirement 7 (Restrict access to cardholder data by business need-to-know) and 8 (Assign a unique ID to each person with computer access).
You can choose from multiple data sources including Active Directory, NTLM (NT LAN Manager; A challenge/response form of authentication that was the default network authentication protocol in Windows NT 4.0.)-, LDAP (Lightweight Directory Access Protocol; an application protocol for querying and modifying directory services running over TCP/IP.)-, or ODBC (Open Database Connectivity; a standard database access method used to access any data from any application, regardless of which database management system (DBMS) is handling the data.)-compatible database as a source for user authentication, or you can use EFT Server's built-in authentication manager to isolate EFT Server users from your domain. EFT Server's Auditing and Reporting Module (ARM) captures all EFT Server activity in a fully relational database; however, the auditing database does not store cardholder data.
Rather than commit changes immediately, the HS-PCI module warns you upon changing one or more settings that may cause EFT Server to fall out of compliance with the PCI DSS. EFT Server gives you the opportunity to undo your changes, or continue with the change and provide justification or description of any compensating controls in place.
Related settings are audited and reported on as a group (e.g., all of the SSL-related settings, or all user settings). For example, suppose on Monday you disable the account lockout settings for a user and specified your reason for allowing this non-compliant setting. Then on Wednesday, you change a complex password setting. The warning message displays both of these settings, as well as others for which you previously had provided justification for leaving as is. Before EFT Server commits the change, you must choose to either allow the change and specify a reason, or discard the changes for each of the non-compliant settings. (That is, the allow or discard flag is separate, but they are audited and reported on as a group.) This functionality is designed to remind you of the non-compliant settings and provide you the opportunity to bring them into compliance.
EFT Server’s HS-PCI module enforces, monitors, reports, or warns when any of the following occur:
Administrator IP address filter not set (PCI DSS 1.3.1, 1.4.1)
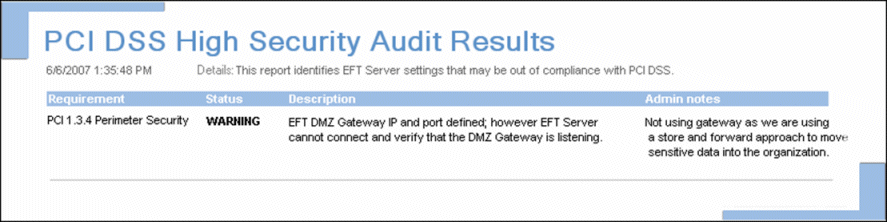
Data stored in the DMZ (no DMZ Gateway present) (PCI DSS 1.3.4)
Check for vendor default ports, passwords in use (PCI DSS 2.1)
Unsecure protocols in use (PCI DSS 2.2.2)
Disk quota not set (PCI DSS 2.2.3)
Secure remote administration not set (PCI DSS 2.3)
Ability to remove old data automatically (PCI DSS 3.1)
Encrypting File System (EFS) in use (PCI DSS 3.4.1)
Weak keys in use (PCI DSS 3.6.1)
Weak SSL versions and ciphers in use (PCI DSS 4.1)
DoS and flood settings too low (PCI DSS 6.5.9)
Initial password reset (PCI DSS 8.5.3)
Removal of inactive accounts (PCI DSS 8.5.5)
Ability to remove or disable inactive accounts (PCI DSS 8.5.5)
Disallow shared passwords (PCI DSS 8.5.8)
Disallow anonymous account types (PCI DSS 8.5.8)
Forced password reset on initial login (PCI DSS 8.5.9)
Password length, expiration, and complexity (PCI DSS 8.5.10,11)
Disable ability to reuse prior passwords (PCI DSS 8.5.12)
Invalid login temporary lockout (PCI DSS 8.15.13,14 )
Data wiping (sanitization) (PCI DSS 9.10.2)
Audit server configuration changes to database (PCI DSS 10.2.2)
Audit initialization of auditing and reporting system (PCI DSS 10.2.6)
Automatic daily PCI DSS compliance reports (PCI DSS 10.6)
From the PCI DSS Security Auditing Procedures document:
Compensating controls may be considered for most PCI DSS requirements when an entity cannot meet a technical specification of a requirement, but has sufficiently mitigated the associated risk.
When EFT Server warns you of a non-compliant setting, if you do not choose a setting that satisfies the PCI DSS requirement, you must specify the compensating controls (hardware, software, or policy) you are using. The information that you provide will appear in the Compliance report, which you can provide to Qualified Security Assessors (QSAs) or Approved Scanning Vendors (ASVs), individuals who are certified by the PCI Security Standards Council as being qualified to validate compliance to the PCI DSS standards.
PCI DSS compliance is an ongoing process, not a "set-it-and-forget-it" project. Periodic self-assessment is an important part of identifying non-compliance and identifying areas that need improvement, and can help save costs if an assessor is required for validation of PCI DSS compliance.
The PCI DSS requires that you track and monitor all access to network resources and cardholder data (requirement 10) and regularly test security systems and processes (requirement 11).
EFT Server's HS-PCI module, in conjunction with EFT Server’s Auditing and Reporting module (ARM) helps you maintain compliance by identifying areas that are out of compliance and e-mailing you a daily compliance report that includes all successes, warnings, failures, and compensating controls, based on multiple evaluation criteria.
You can also run the compliance report "on the fly" in EFT Administrator.
Creating an HS-PCI-Enabled Site