![]()
RADIUS and SecurID cannot run together on the same Site and are not available for Active Directory-authenticated Sites. EFT Server does not support password reset and aging policies for RADIUS or RSA-enabled Sites.
(Available in EFT Server Enterprise) Remote Authentication Dial In User Service (RADIUS) is a networking client/server protocol that runs in the application layer, using UDP as transport, and provides centralized Authentication, Authorization, and Accounting (AAA) management for computers to connect to and use a network service. EFT Server Enterprise, the server has been extended for RADIUS support for RSA SecurID® two-factor authentication to send and receive RADIUS packets to/from a RADIUS server for user authentication. RADIUS authentication can be added to GlobalSCAPE, LDAP, and ODBC authenticated Sites in EFT Server Enterprise's administration interface. The RADIUS settings allow you to configure EFT Server Enterprise as a Network Access Server (NAS).
|
|
RADIUS and SecurID cannot run together on the same Site and are not available for Active Directory-authenticated Sites. EFT Server does not support password reset and aging policies for RADIUS or RSA-enabled Sites. |
The user or device sends a request to EFT Server Enterprise to gain access to a particular network resource, then EFT Server Enterprise sends a RADIUS Access Request message to the RADIUS server, requesting authorization to grant access via the RADIUS protocol. The request may contain username, password, security certificate, network address, and IP/Port used to connect to EFT Server Enterprise. RADIUS servers vary, but most can look up client information in text files, LDAP servers, or databases. The RADIUS server can respond with an Access Reject, Access Challenge, or Access Accept. If the RADIUS server responds with an Access Challenge, additional information is requested from the user or device, such as a secondary password.
The diagram below provides a general overview of EFT Server Enterprise configured in a network with RADIUS.
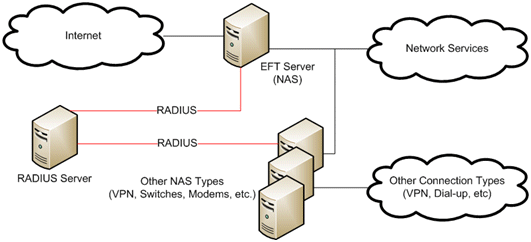
You configure RADIUS in EFT Server Enterprise's administration interface. EFT Server Enterprise's Authentication Manager, Settings Templates, User Settings, New Site wizard, and New User Wizard each allow RADIUS configuration.
In GlobalSCAPE, LDAP, and ODBC-authenticated Sites, the RADIUS Authenticated Settings dialog box, accessed from the New Site wizard and/or the Site's General tab allows you to enable RADIUS or RSA SecurID authentication and to configure the RADIUS/RSA server's IP address, port, NAS Identifier, shared secret, connection retries, and timeout. On the Settings Template and user account General tabs, and in the New User wizard, a simple enable check box is provided for those instances where you might want the Site to have RADIUS enabled, but want to disable it for a Settings Template or specific user.
The RADIUS Authentication Settings dialog box is available from each GlobalSCAPE, LDAP, or ODBC-authenticated Site. The dialog box allows you to enable and configure the connection to the RADIUS server.
Enable RADIUS authentication—The check box is disabled by default.
RADIUS Server—Specifies the name of the RADIUS Server (host name or IP address).
RADIUS Server Port—Specifies the port the RADIUS Server is bound to. The default port is 1812.
NAS Identifier—Specifies EFT Server’s NAS identifier for the RADIUS Server.
Shared secret—Specifies the shared secret used to encrypt and sign packets between EFT Server and the RADIUS Server.
Connection Retries—Specifies the number of times a RADIUS packet will be submitted to the server before giving up. The packet is resubmitted if there is no response from the server. (RADIUS runs over UDP, so packets may be dropped or ignored by the server). The default is 3 retries.
Timeout—Specifies how long to wait for a server response, in seconds. The default is 3 seconds.
The RSA SecurID Authentication Settings dialog box is available from each GlobalSCAPE, LDAP, or ODBC-authenticated Site. The dialog box allows you to specify the location of the RSA Server configuration file.
Click the folder icon to specify the location of the RSA Server configuration file (sdconf.rec), then click OK.
|
|
RSA SecurID uses a “sdconf.rec” file to configure itself as an authentication agent. Upon initial connection to the SecurID server (the first authentication attempt), a "shared secret” is established between (the Authentication Agent (EFT Server) and the RSA SecurID server. EFT Server saves this secret in the same path as the Site's “sdconf.rec” file. If you clear the node secret in RSA SecurID, you will need to clear the secret on EFT Server, or it will be unable to establish a new one with the server. While the service is stopped, delete the “sdstatus.12” and “securid” files that EFT Server created. When you restart the service, a new secret is established. |
EFT Server Enterprise supports RADIUS and RSA SecurID authentication for FTP, FTPS, SFTP, HTTP and HTTPS.
AS2 does not support interactive authentication.
EFT Server does not perform inline checking for PCI DSS compliance for various password controls. In PCI DSS reports, a Status value labeled "Compensating Control" and the following Compensating Control text appears: "Compensating Control: User authentication and password controls for %WHO% are being managed by a remote system, such as RSA SecurID®. (The %WHO% variable contains the name of the Site, Settings Template, or user account.)
EFT Server can be configured to communicate with RSA Authentication Manager via native SecurID protocol or RADIUS protocol.
|
Feature |
Supported? |
|
RSA SecurID Authentication via Native RSA SecurID Protocol |
Yes |
|
RSA SecurID Authentication via RADIUS Protocol |
Yes |
|
On-Demand Authentication via Native SecurID Protocol |
Yes |
|
On-Demand Authentication via RADIUS Protocol |
Yes |
|
On-Demand Authentication via API |
No |
|
RSA Authentication Manager Replica Support |
Yes |
|
Secondary RADIUS Server Support |
No |
|
RSA SecurID Software Token Automation |
No |
|
RSA SecurID SD800 Token Automation |
No |
|
RSA SecurID Protection of Administrative Interface |
No |
For details of configuring RADIUS on a new Site, refer to Defining Connections (Sites).
For details of enabling or disabling RADIUS for a Settings Template, refer to Enabling RADIUS for a Settings Template.
For details of enabling or disabling RADIUS for user/client, refer to Enabling or Disabling RADIUS for a User Account.
For details of COM API methods for RADIUS, refer to Creating a User (CreateUser and CreateUserEx).