Support for Foreign Groups
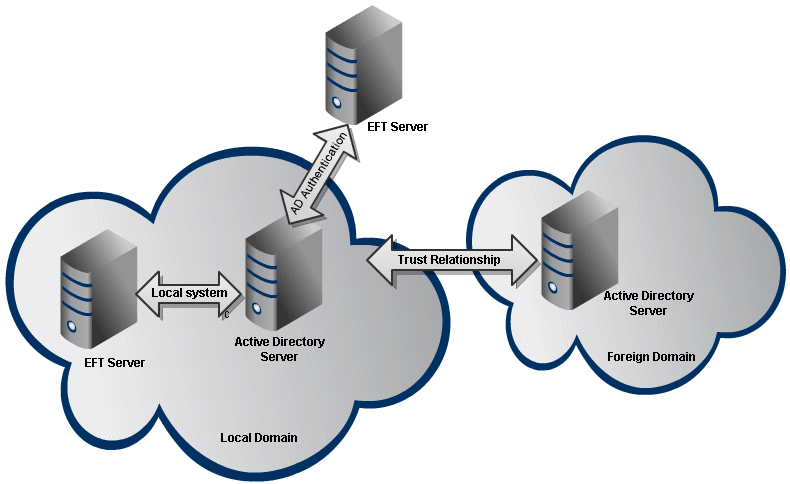
EFT Server allows you to specify only one domain and one group. However, that group can contain groups and users from foreign domains, as long as a trust relationship exists between the domains. This allows users from remote domains to authenticate to EFT Server. So, as long as a trust relationship exists between the domains, EFT Server can authenticate users from remote domains. The domain in which EFT Server resides will need to have a group that contains the foreign domain users.
The main point is that EFT Server simply talks to one AD/forest/controller. If that AD/forest/controller is properly configured to get information from the other domain/forest, then EFT Server will authenticate those users. This also applies to the Secure Ad Hoc Transfer (SAT) authentication module
when AD authentication is used.
|

|
When your forest contains domain trees with many child domains and you observe noticeable user authentication delays between the child domains, you can optimize the user authentication process between the child domains by creating shortcut trusts to mid-level domains in the domain tree hierarchy. For more information, refer to When to create a shortcut trust on Microsoft's Web site. For details of controlling access to shared resources across domains, refer to the Microsoft TechNet article, Accessing resources across domains.
|
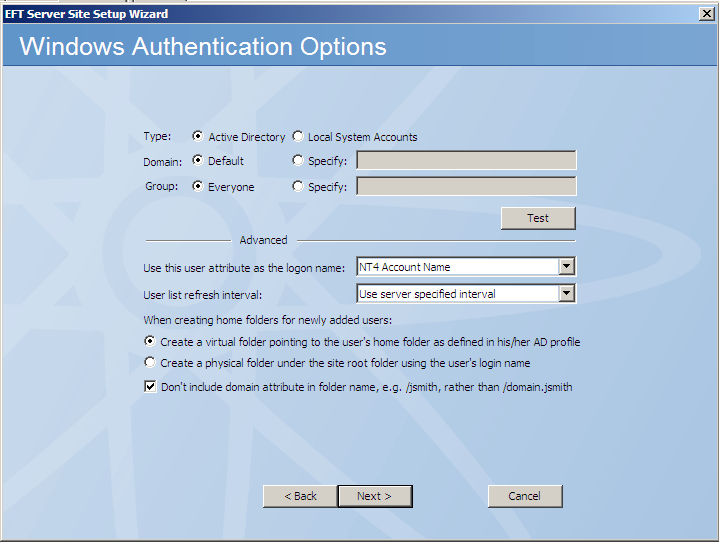
In the Windows Authentication page of the Site Setup wizard, you can specify any combination Domain and Group names, as long as the EFT Server service is running under an account that has rights to list users in that Domain and/or Group.
-
In the Domain area, click Default if you want to use the authentication database on the computer's current domain or click Specify and provide the domain name that contains the authentication database.
-
In the Group area, click Everyone to allow access to every user in the domain's database, or click Specify and type the AD group name for users that will have access to EFT Server to allow access to only a specific AD Group.
-
If the Group is in the home domain, it can be both local and global.
-
To specify a foreign group, use "Domain\group" notation. In this case it must be *global* in that domain (this is a limitation of AD).
-
The group can contain users from both local and trusted domains. You can use any kind of logon names (e.g., domain\user, user@domain).
-
AD has restrictions that do not allow nested groups to be global.
-
If you use a home group, it must be local, otherwise you won’t be able to add anything foreign to it.
-
If you use a foreign group, it must be global or you won’t be able to log in.
-
If you want to nest foreign groups in your home group, they must be local in their domains.
Login Requirements for Active Directory and Windows Local Account Permissions
![]()

