EFT Server's HS module provides a data sanitation/data wiping option. If you do not activate the HS module, this feature is disabled after the 30-day trial expires.
You can configure EFT Server to securely delete or purge a file by writing over the initial data using encrypted and/or pseudorandom data. A menu of purging methods is available; available options depend on the library used.
The 3-pass DoD method is based on to DoD 5220.22-M (aka NISPOM), Chapter 8, Parts E, C and E (again) of the Clearing and Sanitization Matrix. This method:
Overwrites all addressable locations with a character, its complement, then a random character;
Overwrites all addressable locations with a single character;
And again, overwrites all addressable locations with a character, its complement, then a random character.
|
|
*.pgp files are automatically excluded from the wipe process. When wipe is enabled, ANY delete operation also includes the wipe (sanitization) process. |
You can specify which files EFT Server is to purge, including client-initiated delete commands, source files after successful OpenPGP encrypt operation, source file after move command across partition/drive, and others.
To specify a delete method
In the Administrator, connect to EFT Server and click the Server tab.
In the left pane, click the Site that you want to configure.
In the right pane, click the Security tab.
In the Data Security area, next to Secure data removal, click Configure. The Data Sanitation dialog box appears.
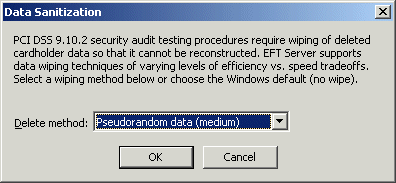
In the Delete method box, click the list to specify one of the following methods:
Windows standard (fastest)
Pseudorandom data (medium)
3 pass DoD 5220.22-m (slow)
Click OK to close the dialog box.
Click Apply to save the changes on EFT Server.
The following message appears when the purging mechanism is changed to anything other than the Windows standard delete method:
"Sanitizing deleted disk sectors is a CPU- and disk-intensive operation and can be quite time consuming. Run performance monitors before and after making this change to determine whether hardware upgrades are necessary to maintain prior levels of performance."
(These links are outside of GlobalSCAPE's domain and could change.)
Data remanence: http://en.wikipedia.org/wiki/Data_remanence,
specifically the section titled "Standard Patterns for Purging":
http://en.wikipedia.org/wiki/Data_remanence#Standard_patterns_for_purging
US DoD 5220.22-M Standard, defined in the US National
Industrial Security Program Operating Manual of the US Department of Defense
(January
1995; chapter 8, section 3, 8-306. Maintenance): http://www.dtic.mil/whs/directives/corres/html/522022m.htm
"Secure Deletion of Data from Magnetic and Solid-State Memory": http://www.usenix.org/publications/library/proceedings/sec96/full_papers/gutmann/