Enable and Configure the Send Portal
Workspaces is an enterprise ad hoc file transfer solution that allows employees to quickly and securely send large files from within the Web Transfer client or in Microsoft Outlook. Workspaces for Outlook allows organizations to address broad scale, risky file sharing practices while providing an easy-to-use interface for end users that requires little to no training from IT staff. Users benefit from an enhanced email experience with advance sending features, such as the ability to receive file pick up receipts. Recipients pickup their files in their web browser via a secure link. Administrators have the ability to manage user transactions behind the scenes, including the ability to set secure link expiration overrides and set policies for the automatic handling of exceedingly large file attachments.
-
To use Workspaces for Outlook, the EFT administrator must enable Workspaces and install and enable the EFT Outlook Add-In on end-users' computers, as described below.
-
When you send a file in the Web Transfer Client, a WorkspacesSendMessage folder is created under the sending user's home folder in the Virtual File System (VFS). Subfolders in the WorkspacesSendMessage folder are named for the Subject line of the message.
To enable Workspaces for sending files
-
In the administration interface, connect to EFT and click the Server tab.
-
On the Server tab, click the Site you want to configure.
-
In the right pane, click the Web tab.
-
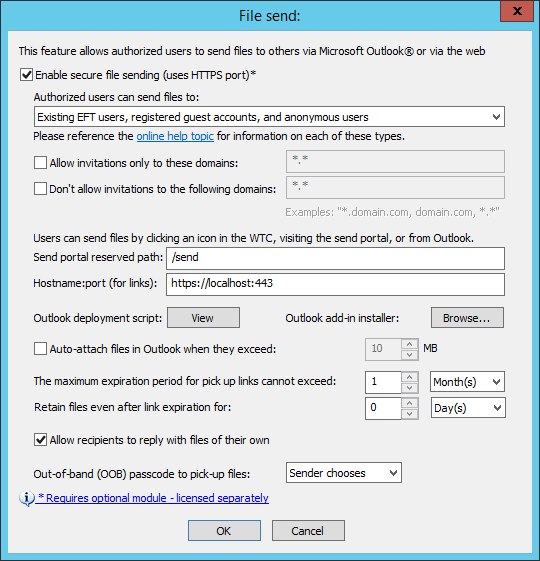
Next to Send Portal, click Configure. The File send dialog box appears.
-
Select the Enable secure file sending check box. This requires the HTTPS port to be configured and available.
-
Under Authorizedusers can send files to, select one of the following options:
-
Existing EFT users only (most restrictive) - Allows EFT users to send files via Workspaces for Outlook only to other users with an EFT account
-
Existing EFT user and registered guest accounts - Allows EFT users to send files via Workspaces for Outlook to other EFT user accounts and registered guest accounts
-
Existing EFT users, registered guest accounts, and anonymous users - Allows EFT users to send files via Workspaces for Outlook to other EFT user accounts, registered guest accounts, and non-EFT user accounts. Non-EFT user accounts do not require credentials, making it easy for the recipient to pick up files, but makes the system less secure. To reduce this risk, the sender can make the pickup link "single use."
-
In the Send portal reserved path box, specify the path for the Send portal. The default is /send.
-
In the Hostname:port box, specify the URL for file pick up. By default, this box will contain the same IP as the Domain box on the Site > Connections tab, but you can change it to an external-facing hostname, if needed (and if so configured in your network). Links that are sent for Workspaces invitations and file sharing will have this URL.
-
To require the use of Outlook for large files, select the Auto-attach files in Outlook when they exceed check box, and then specify a size.
-
Specify the maximum expiration period for pickup links. The default is 1 month.
-
Specify the length of time to Retain files after link expiration. The default is 0 days.
-
This value indicates the length of time between Workspace expiration and file removal, and cannot exceed maximum expiration period, above. On expiration, a "Workspace expired" Event is triggered and the Workspace becomes invisible to the administrator, owner, and participants, but the directory and files remain alive. At the end of the retention period, a "Workspace removed" Event is triggered, the Workspace information is wiped from EFT configuration, and the directory is physically removed from the file system. For example, if a transactional (guest user) Workspace is created to expire in 10 days and retain file for 10 days, if the Workspace expired on October 1, it will then be removed from disk on October 11.
-
Select the Allow recipients to reply with files of their own check box to allow people that you send file to reply with files of their own.> Then you must enable the Request file page to specify the Reply path.
-
Next to Out-of-band (OoB) passcode to pick up files, specify whether a recipient requires a passcode to pick up files. Click the drop-down list and then click Required (sender must require a passcode), Not required (sender does not have to require a passcode), or Sender chooses (whether to require a passcode). (The sender's authentication options appear in the Options dialog in Workspaces.)
-
Click OK, then click Apply on the Web tab.
Transactional Workspaces folders in the VFS that are shared with unregistered users will have an exclamation point on the anonymous-access folder.
To deploy the EFT Outlook add-in on end-users' computers
-
Submit a support ticket to request the EFT Outlook Add-In deployment script, then follow the procedure below.
-
Copy and paste the script into the tool you are using to deploy the Outlook Add-In across your organization.
-
Click OK or press ENTER to close the Outlook Add-in Deployment Script box.
-
Edit the script to match your environment (i.e., the EFTHOST IP address and port, username, password).
-
EFT supports Manual authentication, which is really Basic authentication, so you have to explicitly provide the user's EFT username and password (that is, the username and password that this Add-In user uses to log in to EFT--not the admin credentials). EFT also supports Integrated Windows Authentication (IWA) where you don’t have to explicitly provide a username and password if you are logged into Windows with your domain account.
-
Edit the Add-In installer command-line arguments depending on the authentication type you want:
For manual authentication, do the following (EFTUSERNAME and EFTPASSWORD values have to be substituted with the actual Add-in user’s EFT username and password):
msiexec /lv installation.log /qn /i EFTOutlookAddinInstaller.msi EFTHOST=https://WIN-KST875BEBNP EFTPORT=443 EFTAUTHTYPE=MANUAL EFTUSERNAME=username EFTPASSWORD=test123! INSTALLLOCATION="%userprofile%\AppData\Roaming\GlobalSCAPE\EFT Outlook Add-in" FILESTORELOCATION="%userprofile%\AppData\Local\GlobalSCAPE\EFT Outlook Add-in"
For Integrated Windows authentication, do the following (EFTUSERNAME and EFTPASSWORD don’t need to be supplied):
msiexec /lv installation.log /qn /i EFTOutlookAddinInstaller.msi EFTHOST=https://WIN-KST875BEBNP EFTPORT=443 EFTAUTHTYPE=IWA INSTALLLOCATION="%userprofile%\AppData\Roaming\GlobalSCAPE\EFT Outlook Add-in" FILESTORELOCATION="%userprofile%\AppData\Local\GlobalSCAPE\EFT Outlook Add-in"