FIPS Mode Event Messages
EFT displays FIPS-related messages when switching to/from FIPS modes, starting/restarting EFT or Site, making administration interface connections, or managing certificates. EFT presents messages in the administration interface and in the Windows Event Log and allows you to correct the error. That is:
-
A FIPS initialization error at Server startup does not stop the EFT service. Instead, the service is started and listening for administrator connections, but the Sites are stopped so that you can connect, get diagnostics, disable FIPS mode, and so on.
-
An administrator SSL certificate failure at Server startup does not stop the EFT service immediately. Instead, EFT starts, but does not accept SSL administrative connections. The administrator is able to login locally, get diagnostics, replace the certificate, and so on.
-
An administrator SSL certificate failure after SSL FIPS mode switching does not stop the EFT service. Instead, EFT continues working, but does not accept SSL administrative connections. The administrator can connect to replace the certificate, and so on.
FIPS Mode Messages in the Administration Interface
EFT displays the following FIPS-related messages in the administration interface.
<SITENAME> will be started with the following protocols: FIPS-certified protocols: <FIPSPROTOCOLS> Non-FIPS protocols: <NONFIPS> To ensure FIPS-certified operation, please enable only FIPS-certified protocols.
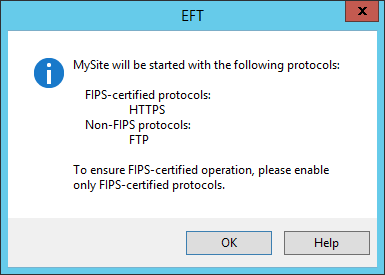
When EFT is in SSL or SSH FIPS mode, this message reports which Site protocols are FIPS-secured and which are not each time the administrator explicitly starts the Site (for example, clicks Go or the Start button on the General tab of the Site).
The EFT is stopped: FIPS mode initialization error. All sites and protocols are disabled.
This warning message appears upon new administration connections if FIPS fails to initialize. FIPS can fail to initialize because EFT could not load the FIPS library or the library self-test failed. When this occurs, EFT is stopped and all Sites and protocols are disabled.
An error occurred while attempting to start EFT. FIPS mode initialization error; all sites and protocols have been disabled.
This message appears in the administration interface during Server start or restart when FIPS fails to initialize. FIPS can fail to initialize because EFT could not load the FIPS library or the library self-test failed. When this occurs, EFT is stopped and all Sites and protocols are disabled.
An error occurred while attempting to start Site ‘<SITE_NAME>. The SSL certificate provided for Site ‘<SITE_NAME>’ has an improper key length. FIPS 140-2 mode requires keys between 1024 and 4096 bits (inclusive). Please choose a different certificate, or generate a new one that has at least 1024 but no more than 4096 bits in the public key.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
An error occurred while attempting to start Site ‘<SITE_NAME>’. Could not load SSL certificate.
This message appears during Site start/restart if a Site uses SSL and its certificate does not meet FIPS requirements (for example, FIPS mode gets turned on and old certificate/key does not pass the FIPS test). The Site is stopped.
An error occurred while attempting to start Site ‘<SITE_NAME>. The SFTP key provided has an improper key length. FIPS 140-2 mode requires keys between 1024 and 4096 bits (inclusive). Please choose a different key, or generate a new one that has at least 1024 but no more than 4096 bits in the public key.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
An error occurred while attempting to start Site ‘<SITE_NAME>’. Could not load SFTP certificate.
This message appears during Site start/restart if a Site uses SFTP and its key does not meet FIPS requirements (for example, FIPS mode gets turned on and old certificate/key does not pass the FIPS test). The Site is stopped.
The Site <SITE_NAME> is not started: [SSL certificate | SFTP key] is too weak and does not meet FIPS 140-2 requirements. Clients will not be able to connect to the Site.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
The Site <SITE_NAME> is not started: could not load [SSL certificate | SFTP key]. Clients will not be able to connect to the Site.
This warning message appears during new administration interface connections if a Site uses SSL and its certificate does not meet FIPS requirements or uses SFTP and its key does not meet FIPS requirements (for example, FIPS mode gets turned on and old certificate/key does not pass the FIPS test). The Site is stopped.
EFT SSL certificate for remote administration is not an approved size (must be at least 1024 but no more than 4096 bits). Administrators will not be able to connect to EFT remotely.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
EFT SSL certificate for remote administration is broken. Administrators will not be able to connect to EFT remotely.
This warning message is used in to notify all connected administration interfaces if the SSL certificate for remote administration does not meet FIPS requirements. Remote administration connections via SSL are not accepted.
EFT SSL certificate for remote administration is too weak and does not meet FIPS 140-2 requirements. Administrators will not be able to connect to EFT remotely.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
EFT SSL certificate for remote administration is broken. Administrators will not be able to connect to EFT remotely.
This warning message is used during new administration interface connections if the SSL certificate for remote administration does not meet FIPS requirements. Remote administration connections via SSL are not accepted.
EFT [SSL | SSH] subsystem has entered FIPS mode. All new connections over [SSL | SSH] will use EFT’s FIPS cryptographic libraries.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
EFT [SSL | SSH] subsystem has exited FIPS mode. All new connections over [SSL | SSH] will use EFT’s standard (non-FIPS) cryptographic libraries.
These informational messages appear in the administration interface to notify all connected administration interfaces when an administrator explicitly switches SSL or SSH FIPS mode or FIPS mode is disabled due to trial expiration.
FIPS Mode Events in the Event Log
EFT displays the following FIPS-related events in the Windows Event Log.
Globalscape EFT - FIPS [SSL|SSH] mode initialization error; all sites and protocols are disabled.
This error message appears in the Event Log upon the EFT service start or restart if FIPS fails to initialize. FIPS can fail to initialize because EFT could not load the FIPS library or the library self-test failed. When this occurs, EFT service is stopped and all Sites and protocols are disabled.
Globalscape EFT - FIPS mode initialization error for site "<SITE_NAME>": the specified [SFTP key|SSL certificate key] is not an approved size (must be at least 1024 but no more than 4096 bits). The site has not been started.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
Globalscape EFT - FIPS mode initialization error for site "<SITE_NAME>": the specified [SFTP key|SSL certificate] is broken. The site has not been started.
This message appears during Site start/restart if a Site uses SSL and its certificate does not meet FIPS requirements or uses SFTP and its key does not meet FIPS requirements (for example, FIPS mode gets turned on and old certificate/key does not pass the FIPS test). The Site is stopped.
EFT SSL certificate for remote administration is not an approved size (must be at least 1024 but no more than 4096 bits). Administrators will not be able to connect to EFT remotely.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
EFT SSL certificate for remote administration is broken. Administrators will not be able to connect to EFT remotely.
This warning message appears in the Event Log if the SSL certificate for remote administration does not meet FIPS requirements. Remote administration connections via SSL are not accepted.
EFT [SSL | SSH] subsystem has entered FIPS mode. All new connections over [SSL | SSH] will use EFT’s FIPS cryptographic libraries.
Or, if other certificate error (forbidden algorithms, inconsistent private key, or invalid private key password):
EFT [SSL | SSH] subsystem has exited FIPS mode. All new connections over [SSL | SSH] will use EFT’s standard (non-FIPS) cryptographic libraries.
This informational message appears in the Event Log when an administrator explicitly switches SSL or SSH FIPS mode or FIPS mode is disabled due to trial expiration.
Globalscape EFT - FIPS [SSL|SSH] mode initialized successfully; operating in compliance with FIPS 140-2.
This informational message appears in the Event Log every time the EFT service starts or restarts to report its successful FIPS mode initialization.