Introduction to SAML (Web SSO) Authentication
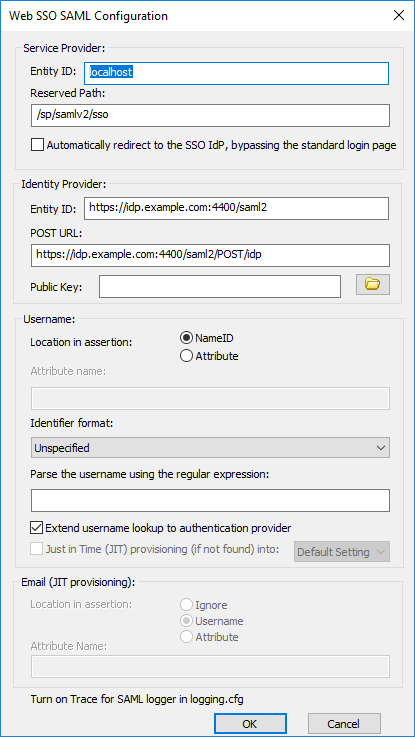
(Available in the Premium Tier and configured by Support) The SAML SSO feature in EFT will look up accounts to match the user-id configuration, and if found, it will associate the IdP-authenticated users with said pre-provisioned accounts. EFT can also optionally perform what’s called Just In Time (JIT) provisioning, where it can create an account in a pre-designated Settings Template, for authenticated users, if they do not already exist in EFT. When a positive mapping of identify assertions to existing user accounts cannot be made, Web SSO authentication will fail or revert to normal authentication and request login credentials. (See Web SSO Error Handling).
In the Web SSO SAML Configuration dialog box, you can specify to use the Email Attribute Name in JIT or LDAP after an IDP- or SP-initiated login to create an account in EFT.
-
SAML 2.0 Service Provider-initiated Web Single Sign-on with POST bindings is currently the only profile supported on EFT. EFT uses the OpenSAML library SAML 2.0. EFT does not support SAML 1.0 or 1.1.
-
EFT Login Security options do not apply to SSO failed logins. Login security controls, such as password complexity and failed logins, are within the responsibility of the Identity Provider (IdP) and are not controlled by EFT. (Refer to Banning an IP Address that Uses an Invalid Account and Disabling or Locking out an Account after Invalid Password Use for details of those options.)