Enable Multifactor Authentication
Multifactor authentication is the process of verifying the identity of a user in which the user is granted access only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something the user, and only the user, knows), possession (something the user, and only the user, has), and inherence (something the user, and only the user, is).
Two-factor authentication (2FA), a subset of multi-factor authentication, is a method of confirming users' identities by using a combination of different factors: 1) something they know, 2) something they have, or 3) something they are. A common example of 2FA is withdrawing money from an ATM: only the correct combination of a bank card (something the user possesses) and a PIN (something the user knows) allows the transaction to be carried out.
EFT offers multifactor authentication (MFA) for recipients in the Pickup portal, with which a time-based one-time passcode (OTP) is delivered automatically to the recipient's email address or via text message. When attempting authentication, the account is locked out for 5 minutes after 5 failed attempts in a 5-minute period. If the first attempt fails, a user can repeat registration and get a new verification code after 5 minutes have passed since the previous registration attempt.
Refer to Enable and Configure the Send Portal for MFA settings in Workspaces.
How does MFA work in EFT?
-
When logging in to the WTC, if the Require additional factor for HTTPS auth check box is selected and configured (shown below), the WTC prompts for a passcode, and informs the recipient to check their email or text messages.
-
EFT generates a OTP and sends it in an email or text message to the recipient. (The user account details must be include their mobile phone number to use SMS; otherwise the email address is used. Therefore, for ad hoc interactions, you should specify email delivery of the OTP.)
-
The recipient checks email/text, and copies the passcode to the clipboard (or clicks the link).
-
The recipient pastes the passcode (or follows link) in the WTC.
-
If the passcode is verified, the WTC allows access.
To enable and configure MFA
For SMS to work, you must first define an SMS profile on the Site > Connections tab. To enable MFA in Workspaces, refer to Enable and Configure Folder Sharing (Workspaces).
-
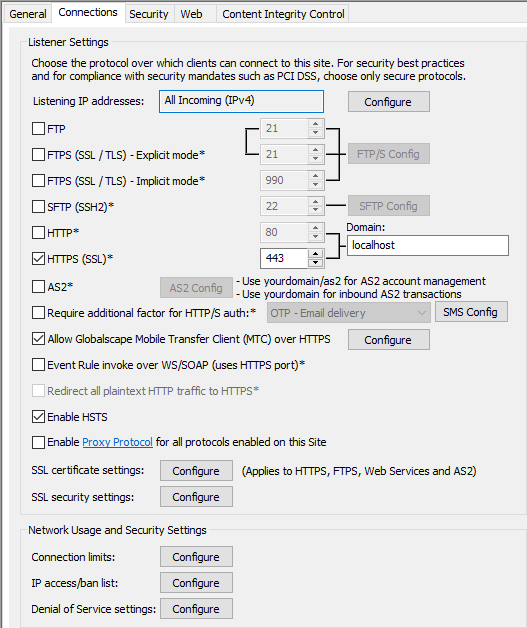
On the Site > Connections tab, enable and configure HTTPS, if not already done. (The MFA settings are inherited from the Site level, but you can enable or disable it on the Settings Template level also. You cannot enable/disable MFA at the user level.)
-
Select the Require additional factor for HTTPS auth check box. EFT does a quick scan of all users under that Site or Template, and if one or more users is found without an email address or mobile phone number defined, a prompt is displayed.
-
Click the OTP drop-down list. In the OTP list, select the method of delivery:
-
OTP - Email delivery - EFT does not verify whether SMTP server configuration is completed correctly
-
OTP - SMS delivery - If no mobile number is available for the user, SMS delivery will fail.
-
OTP - Try SMS then Email - EFT first looks for mobile number in the user details. If no mobile number is defined, the email address is used.
-
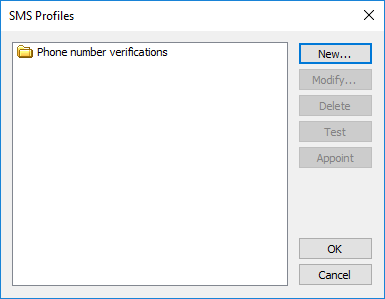
To configure the Twilio for your SMS provider, use the settings provided when you set up your Twilio account. Click SMS Configure. If you chose SMS, the SMS Profiles dialog box appears:
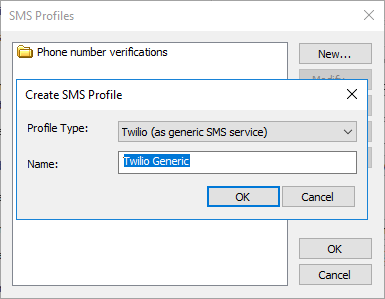
- New - Opens the Create SMS Profile dialog box:
-
Click New to create a new SMS profile (as a generic SMS or with a custom verification code).
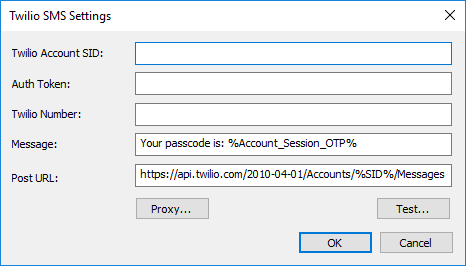
- Modify - Opens the Twilio SMS Settings dialog box for a selected profile
-
Provide the Twilio Account SID copied from your Twilio account.
-
Provide the Auth Token copied from your Twilio account.
-
Provide the Twilio Number copied from your Twilio account. You must include the country code and the + PLUS SIGN (that is, in the USA, +1) in front of the number.
-
Provide the Message that will be sent in the SMS, but keep the variable %Account_Session_OTP%. This variable is used by EFT to send the OTP. Do not edit anything between the percent symbols.
-
Provide the Post URL copied from your Twilio account.
-
Configure a Proxy, if needed. Refer to Defining a Proxy for details.
-
Click Test to verify the connection.
-
If the test is successful, click OK, then click Apply to save the configuration.
- Delete - Deletes a selected profile
- Test - Allows you to send a test SMS message using the selected profile
- Appoint - Assigns the selected profile to the Site.
-
On the Server > General Tab, edit the Authentication OTP message, if needed.
Important notes to consider
Multifactor activation is only applicable where account registration is required, and thus is not applicable to:
-
Reply portal (you cannot reply unless you first pickup, which does require registration)
-
Anonymous interactions (no account is registered)
EFT skips 2FA for following user agents:
-
Anonymous ad hoc transfers (Send passcode via other means.)
-
Protocols other than HTTP/S
-
GlobalSCAPE-EFTApplet
-
JFileUpload
-
MSFT File Transfer Tool
-
EFT-Mobile-Client
-
Desktop Transfer Client
-
EFT-Outlook-Addin
-
Load Balancer Agent
-
ELB-HealthChecker/
-
EFT Remote Agent
-
When certain user-agents are defined.