Internal Domain Settings
The Internal Domain Settings dialog box on the DMZ Gateway tab, is used to configure separate external and internal domain access. See Specifying External and Internal Domains and Allow LDAP Authentication through DMZ for more information about how to do that. Below are some diagrams to visually describe how the two check boxes, Allow LDAP authentication to EFT through DMZ Gateway and Make LDAP authentication exclusive for internal connections, interact to determine external and internal user access.
|
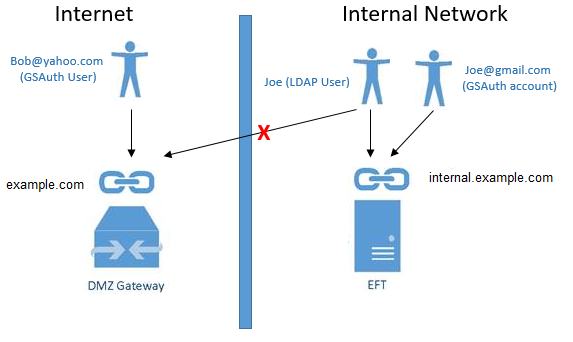
1) When neither box is selected, EFT and DMZ Gateway are in a "split domain" configuration:
|
|
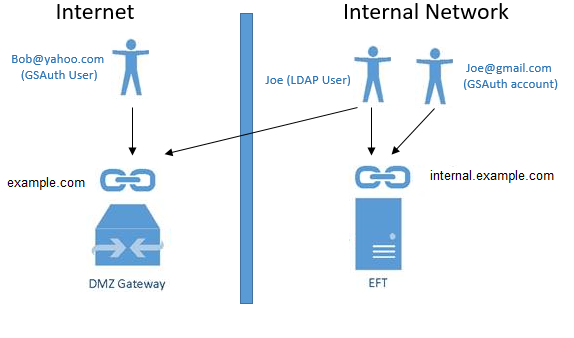
2) When the Allow LDAP authentication to EFT through DMZ Gateway check is selected (but not the Make LDAP authentication exclusive for internal connections check box):
|
|
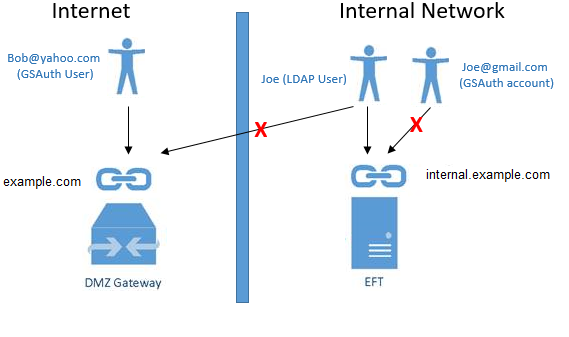
3) When the Make LDAP authentication exclusive for internal connections check box is selected:
|
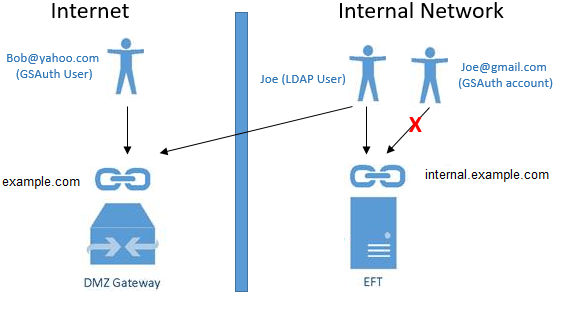
4) When both the Allow LDAP authentication to EFT through
DMZ Gateway check box and the Make
LDAP authentication exclusive for internal connections
check box are selected:
 |