Allow LDAP Authentication to EFT through DMZ Gateway
Suppose an EFT administrator wants to create an environment in which users in their internal network (as specified by their LDAP server) can access the server to do whatever they want; however, they do NOT want those employees to visit the server from outside their own offices. They also have Workspaces participants that are outside the company, and they need to distinguish INTERNAL access from EXTERNAL access. Described below is a way to set a host name for their DMZ Gateway (internet facing) entry to EFT, and anything flowing into EFT from that path will be considered EXTERNAL. Allowing LDAP authentication to EFT through DMZ Gateway is only for directly signing into WTC (not clicking Workspace in a notification email).
(See also Specifying External and Internal Domains and Internal Domain Settings dialog box in Site configuration.)
Hyperlinks in Workspaces notification emails are composed based upon recipient domain:
-
External Users will be directed towards the domain address on the site-connections tab
-
Internal Users will be directed towards the address on the internal domain button of the DMZ Gateway
The external domain is specified on the Site's Connections tab:
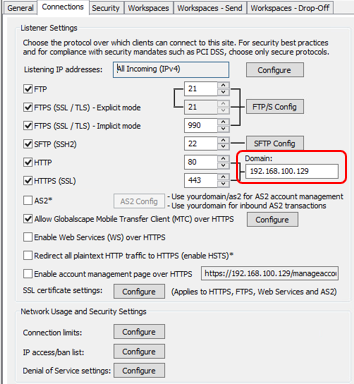
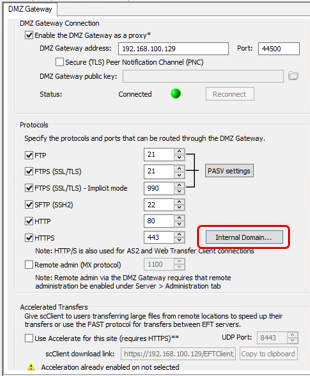
An Internal Domain is specified on the DMZ Gateway tab:
Hyperlinks in notification emails are composed based upon recipient domain
-
In the DMZ Gateway tab Internal Domain settings, the internal email domain list, similar to email domain list in Workspaces Drop-Off tab, is, by default, empty. Empty means no email domain matching is performed and links are not altered.
-
In the DMZ Gateway tab Internal Domain settings, the internal host name is, by default empty. Empty means that no domain matching is performed and links are not altered.
-
If EFT sends an email where the email domain (after the "@" symbol) matches one of the specified "internal domains" values, any URLs formed by EFT and pointing to EFT in the email should be constructed using the internal host name (e.g., mft2go.internal.com).
-
If no internal host name was specified, then EFT will use the default host name.
-
If EFT sends an email where the email domain (after the "@" symbol) matches NONE of the specified "internal domains" values, any URLs formed by EFT and pointing to EFT in the email should be constructed using the default host name specified in the DMZ Gateway tab.
To specify the internal domain on an LDAP site
-
In the EFT administration interface, click the Server tab, then click the Gateway node.
-
On the DMZ Gateway tab, next to the HTTPS port box, click Internal Domain. The Internal Domain Settings dialog box appears.
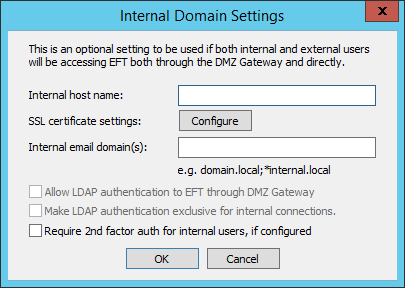
Only invitation emails sent to these domains will include this alternate link address. All others will point to the default links.
-
In the Internal host name box, specify the URL through which internal users should log in to EFT.
-
In the Internal email domain(s) box, specify one or more SMTP domains used by internal users, separated by semicolons.
-
(optional) To allow internal LDAP accounts to authenticate to EFT through DMZ Gateway, select the Allow LDAP authentication to EFT through DMZ Gateway check box. (Cleared by default.)
-
(optional) To allow LDAP authentication available only for internal accounts, select the Make LDAP authentication exclusive for internal connections check box. (Cleared by default.)
-
(optional) To enable two-factor authentication for internal domain users, select the Require 2nd factor auth for internal users check box. (Cleared by default.)
-
Click OK.
To specify a custom LDAP attribute to populate user's email at Site and Settings Template level
-
On the LDAP Site's General tab, click Configure. The LDAP Authentication Options dialog box appears.
-
Click Advanced. The LDAP Authentication Advanced Options dialog box appears.
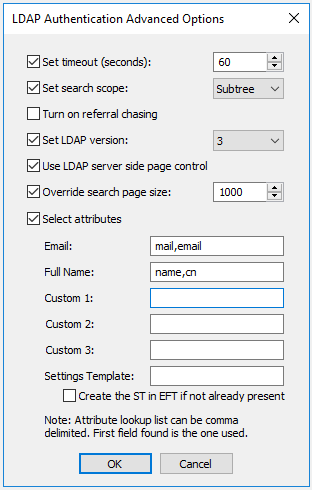
Custom Attributes:
-
Multiple attributes can be added to each custom field, but only the first attribute will be used; All other attributes will be ignored
-
An attribute field on the LDAP server can contain multiple attributes if you want multiple attributes added to a single custom field (example: address)
If a user account has been removed from EFT due to inactivity, the user can still log in to Workspaces. The account will be added back to EFT after they log in.
-