Remote Administration
You can remotely administer EFT from any computer on which the administration interface is installed (with network access). If you are using SSL, you must create and/or assign an SSL certificate to use for connections. When you connect from a remote administration interface, an SSL Certificate dialog box appears in which you must accept the certificate to continue. If you reject the certificate, the User Connect Failed Event is triggered with the Event Reason of "Client SSL Certificate was rejected."
If you are not installing the administrative interface and plan to use the COM API for remote administration, refer to Remotely Administering EFT Using the COM API in the COM API reference.
Refer to FAQs About Remote Administration for several facts and caveats to consider regarding remote administration.
Refer to Remote Administration via DMZ Gateway if you intend to allow EFT administration through DMZ Gateway.
Remote administration is not allowed after the trial expires if you do not activate the software.
If you are using SQL Express as your database, you may not be able to generate a report remotely, unless the connecting account is a trusted SQL Server connection (e.g., if SQL Server and the remote computer are in the same domain, or if SQL Server is configured to allow "mixed authentication").
What you can't do remotely:
-
File browse operations are disabled. However, you can type a path that is relevant to the EFT computer (not the remote interface). For example, when you create a Command or a Monitor Folder Event Rule remotely, you can't click the folder icon and browse to the path of the file that you want to execute or the folder that you want to monitor on the EFT computer, but you can type the path. (No verification is done on the path that you type.)
-
SSL and SSH certificates cannot be created or managed remotely.
Before you can connect from the remote administration interface, you must:
-
Configure the Server. You must do this locally, on EFT computer.
-
Configure remote administration, as described below.
If you have configured remote administration, but are unable to connect, one or more of the following could be preventing the connection:
-
The IP address of the computer on which you are attempting to connect to EFT is listed in the Remote Administration Ban IP list.
-
Your SSL certificate is expired or invalid.
-
The Allow remote administration check box has been cleared.
-
The remote administration port value has changed.
-
EFT’s IP address has changed since the last login.
-
The firewall settings of the computer on which EFT is installed are blocking the connection.
-
There is a version mismatch between your administration interface and the EFT service that you are trying to administer.
-
The account with which you are attempting the remote connection does not have access permission to EFT.
-
Network errors
The following topics describe:
To configure EFT for remote administration
-
Launch the administration interface on EFT computer and connect to EFT you want to configure for remote administration. (You cannot setup remote administration remotely.)
-
In the right pane, click the Administration tab.
-
In the Server administrator listening IP box, specify the IP address that is allowed to connect remotely. You can select a specific IP address that is defined on the computer on which EFT is installed or All Incoming IP addresses. (For command-line login, the EFT administrator listening IP address must be set to a specific IP address, not All Incoming.)
-
For remote administration through DMZ Gateway, be sure to use the IP address of DMZ Gateway, not EFT.
-
-
In the Port box, specify the port on which EFT listens for connections. The default port is 1100. For security, you should use a different port other than the default.
-
Select the Allow remote administration check box. A warning message appears advising you to connect over SSL for more secure administration.
-
Click Yes to set up secure administration or No to administer the server over a clear (not secure) connection.
-
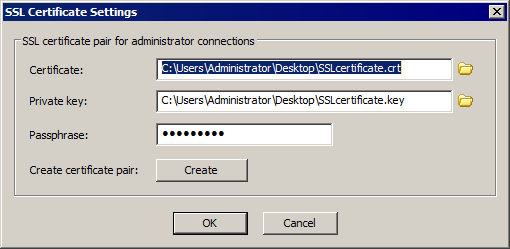
To require SSL for remote connections, click the Require SSL for remote administration check box, and then click Configure. The SSL Certificate Settings dialog box appears.
-
Do one of the following:
-
To create a certificate, click Create and follow the prompts in the wizard. (Refer to Creating Certificates for details, if necessary.)
-
To use an existing certificate:
-
In the Certificate box, type the path to the .crt file or click the folder icon
 to find
and select it.
to find
and select it. -
In the Private key box, type the path to the .key file or click the folder icon
 to find
and select it.
to find
and select it. -
In the Passphrase box, type the passphrase for the certificate pair.
-
-
Click OK to close the dialog box.
-
Click Apply to save the changes on EFT.
-
Close the administration interface. Make sure that the EFT service is still running, then configure the remote administration interface using the procedure below.
If you attempt to allow remote administration on a high security-enabled Site, a message appears to warn you that this setting violates PCI DSS, and allows you to continue with reason or disable the feature.
To configure the remote administration interface
-
Launch the administration interface on the remote computer.
-
Click the Server tab.
-
Specify EFT Group to which you want to add the remote server.
-
On the File menu, click Add New Server. The Login wizard New Administrator Connection page appears.
-
Click Aremote computer.
-
In the Label box, type the name of EFT to which you want to connect. You can call it anything you want; it has nothing to do with EFT's computer name.
-
In the Host address box, type the IP address of EFT computer.
-
In the Port box, type the port number used by EFT.
-
Click Next. The EFT Administrator Login page appears.
-
Click A remote computer, then click its name (the label you gave EFT in step 6) in the box.
-
In the EFT Server administrator credentials area, provide your Username and Password, and then click Connect.
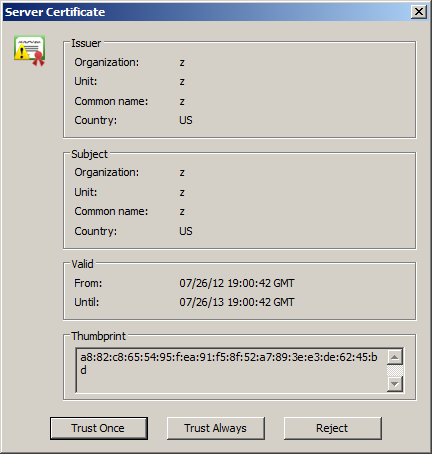
If SSL is required for remote administration, a Server Certificate dialog box appears.
-
Accept or reject the SSL certificate from the remote EFT by clicking Trust Once (just for this session), Trust Always (for this and future connections, provided the SSL certificate does not change), or Reject (do not accept the certificate and do not connect to the server). (To undo a trust-always certificate, delete the appropriate trusted certificate file(s), stored in the %AppData% directory as Cert_for_<ip>.crt.)
-
If connection was successful, the remote Server appears in the tree.
-
If connection was not successful, verify the IP address and port on which EFT listens for connections, and ensure that SSL is properly configured on EFT, if used.
-
Remote Administration FAQ
EFT allows you to administer it remotely from any computer with network access. You can administer EFT with the administration interface (AI) or using the COM API. Below are several facts and caveats to consider regarding remote administration.
-
If you are remotely connected to EFT via DMZ Gateway and make a change to the EFT<->DMZ Gateway settings, including disconnecting EFT from DMZ Gateway, the active session will not be affected. If/when you attempt to reconnect to EFT via DMZ Gateway, you will experience the effects of any changes.
-
File browse operations are disabled. However, you can type a path that is relevant to the EFT computer (not the remote interface). For example, when you create a Command or a Monitor Folder Event Rule remotely, you can't click the folder icon and browse to the path of the file that you want to execute or the folder that you want to monitor on the EFT computer, but you can type the path. (No verification is done on the path that you type.) You are able to browse for a Settings Template folder, because you are browsing the VFS, not the physical folders.
-
SSL and SSH certificates cannot be created or managed remotely. You are prohibited from creating certificates for EFT while remotely administering EFT because this action can create a security breach. Any certificates you create remain on the computer on which you created them, unless you take steps to deliver and associate these files with another computer. When you remotely connect to EFT Server, you will be prompted to Trust or Reject the server certificate.
-
OpenPGP keys cannot be created or managed remotely.
-
You do not need a separate license for each installation of the administration interface.
-
When you install the AI remotely, SSL.DLL and SFTPCOMInterface.DLL are installed in C:\Program Files (x86)\Common Files\Globalscape\SFTPCOMInterface on the remote computer.
-
Organizations complying with the PCI DSS are required to use SSL for remote administration. If you attempt to allow remote administration on a high security-enabled Site without SSL, a message warns you that this setting violates PCI DSS, and allows you to continue with reason or disable the feature.
-
When the trial period has expired, all remote connections are disallowed.
-
You cannot activate the server or modules through a remote installation of the administration interface.
-
You cannot configure remote administration remotely.
-
You must configure the local connection before you can configure a remote connection.
-
When you are upgrading, remember to upgrade any remote installations of the administration interface to the same version.
-
For remote Active Directory connections, the connecting account must have access to the computer on which EFT is installed.
-
You can select AD accounts when performing remote administration as long as the administration interface and EFT are in the same domain or working across trusted domains.
-
You can login using the EFT computer's local administrator credentials from a command line or a Windows shortcut, using the EFT listening IP address and port.
-
You should restrict remote administration to one or more known static IP addresses.
-
By default, all IP addresses are granted remote access to EFT. EFT allows you to grant access to only one specific IP address or a range of IP addresses, or deny access to one specific address or a range of addresses.
-
For command-line login, the EFT listening IP address must be set to a specific IP address, not All Incoming. Remote administration must be configured and EFT must be in the same domain as the computer from which you are attempting to log in.
-
Before attempting to connect to a remote EFT, first be sure that the remote EFT service is running, and that it allows remote administration.
-
If you are logged in to EFT remotely, your username and password are passed to the Windows System Services on the computer running EFT. The account that you log on with must have administrative rights to make any changes to the Globalscape EFT service running on that computer.
-
If you are using SQL Express as your database, you may not be able to generate a report remotely, unless the connecting account is a trusted SQL Server connection (e.g., if SQL Server and the remote computer are in the same domain, or if SQL Server is configured to allow "mixed authentication.")
-
When objects are created, added, removed, modified, enabled, disabled, started, or stopped remotely, the action is logged to the database and reported in the Administrator Actions Log. (Administrator actions logging requires the ASM and ARM.)
-
The EFT variable for remote EFT connections is %CONNECTION.REMOTE_IP%.
-
If you are unable to connect to a remote server, verify that the remote server is configured to allow remote administration, and that you have provided the correct IP address, port, and login information.