Configuring SFTP for a Site
(Requires the SFTP module in EFT SMB/Express) When you enable SFTP for a Site, you must configure the SFTP settings. You can then configure SFTP options for a Settings Template and/or user account.
See also SFTP FIPS.
To configure SFTP for a Site
-
Before you can enable and configure SFTP on the Site, you must create or import an SFTP key defined on the Site.
-
In the administration interface, connect to EFT and click the Server tab.
-
On the Server tab, click the Site you want to configure.
-
In the right pane, select the Connections tab.
-
Select the SFTP (SSH2) check box, then specify the port, if different from the default shown.
-
Click SFTP Config. The SFTP Settings dialog box appears.
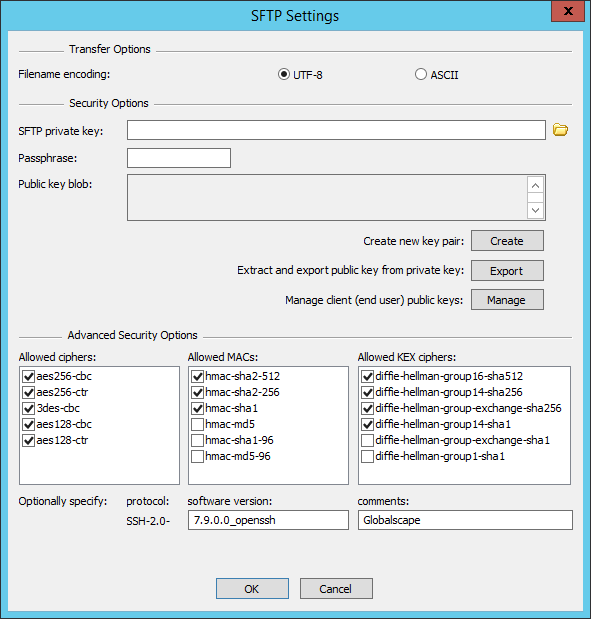
-
In the Encoding area, click UTF-8 or Auto-detect.
-
UTF-8—For Unicode-only transfers
-
Auto-detect—Detects whether to proceed in ASCII mode or can switch to UTF-8 mode for the transmission and receipt of path names and other strings communicated between client and server.
-
-
The key that you created when you defined the Site (if you enabled SFTP and created keys) appears in the SFTP Settings dialog box. If you did not enable SFTP when you created the Site, the dialog box is empty.
-
Do one of the following:
-
To create a key pair, click Create. The SSH2 Key Pair Generation Wizard appears. Refer to Creating an SSH Key Pair for instructions, if necessary.
-
To specify an existing key pair, click the folder icon
 then
browse for and select a key pair (.pvk)
file.
then
browse for and select a key pair (.pvk)
file. -
Click Export to extract and export the public key (.pub). A Save As dialog box appears in which you can specify a name and location for the .pub file.
-
Click Manage to view, import, rename, and/or delete keys.
-
-
Specify the SFTP private key path, public key path, public key blob, allowed ciphers, allowed MACs, and SFTP identification string, as necessary.
-
Click OK to close the dialog box.
-
Click Apply to save the changes on EFT.
For the KEX ciphers, there a few configuration changes to note:
-
On a new installation, diffie-hellman-group-exchange-sha256 and diffie-hellman-group14-sha1 should be enabled.
-
-
diffie-hellman-group14-sha1 should be left enabled for compatibility in accordance with the most recent SSH RFC draft recommendations (dated March 27th, 2017):
"diffie-hellman-group14-sha1 method SHOULD- be retained for compatibility with older Secure Shell implementations. It is intended that this key exchange method be phased out as soon as possible" https://tools.ietf.org/html/draft-ietf-curdle-ssh-kex-sha2-07
-
-
On upgrade, existing selected KEX methods should persist.
-
The existing registry override to disable/enable diffie-hellman-group1-sha1 (https://kb.globalscape.com/KnowledgebaseArticle11266.aspx) should become inactive in place of the administration interface selections