Creating a Site
In EFT, a Site is how you connect to EFT. This topic describes how to create the connection, including IP address, port, and so on.
- The Site Setup wizard appears automatically after you complete the Server Setup wizard; otherwise, do one of the following:
- In the administration interface, click Configuration >Create New Site.
- Right-click anywhere in EFT's tree, then click Create New Site.
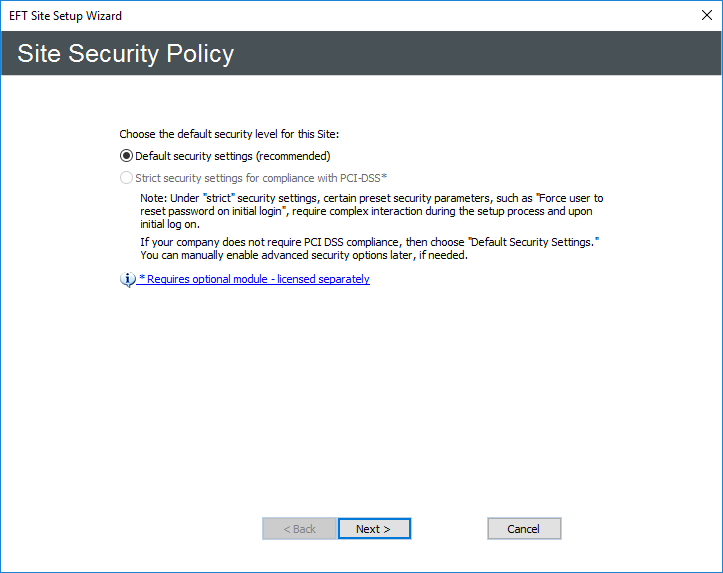
- You are asked to choose the default security level for the Site. If PCI DSS compliance is not a requirement, you can use the default security settings and then manually configure advanced security options individually, as needed. Do one of the following:
-
To create a Site that complies with PCI DSS, refer to Creating a strict security-enabled Site.
-
To create a standard Site, click Default security settings.
- Click Next. The Site Label and Listening IP page appears.
- In the Site label box, type a distinguishing name for the Site. MySite appears by default, but you can change this to anything you want.
- Next to the Listening IPs box, click Configure. The Listening IP Settings dialog box appears.
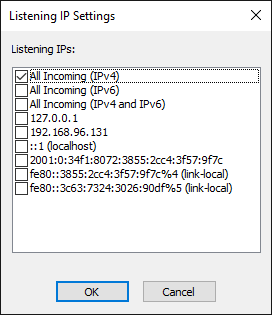
- The dialog box displays the IP addresses that are available on the computer, in addition to All Incoming (IPv4) and All Incoming (IPv6).
- You cannot type in an address.
- IPv6 is not enabled by default for security reasons; IPv4 is enabled by default.
- The "All" options are exclusive. That is, you can't select All Incoming (IPv4) and then one or more specific IP addresses. However, you can select multiple individual addresses if none of the "All" options are selected.
- "Link local" appears next to certain IPv6 addresses. Routers do not forward packets with link-local addresses. In IPv6, link-local addresses are always assigned, automatically or by configuration, and are required for the internal functioning of various protocol components. IPv6 requires operating systems to assign link-local addresses to network interfaces even when routable addresses are also assigned. A link-local unicast address has the prefix fe80::/10 in standard IPv6 CIDR notation.
- Select one or more check boxes for the IP addresses on which the Site is to listen for connections, and then click OK. The selected addresses appear in the Listening IPs box.
- You can copy the addresses in the Listening IPs box: Right-click in the box, click Select All, then right-click again and click Copy or use CTRL+V. (Unicode-related items on the right-click menu are a Windows feature and do not apply to EFT.)
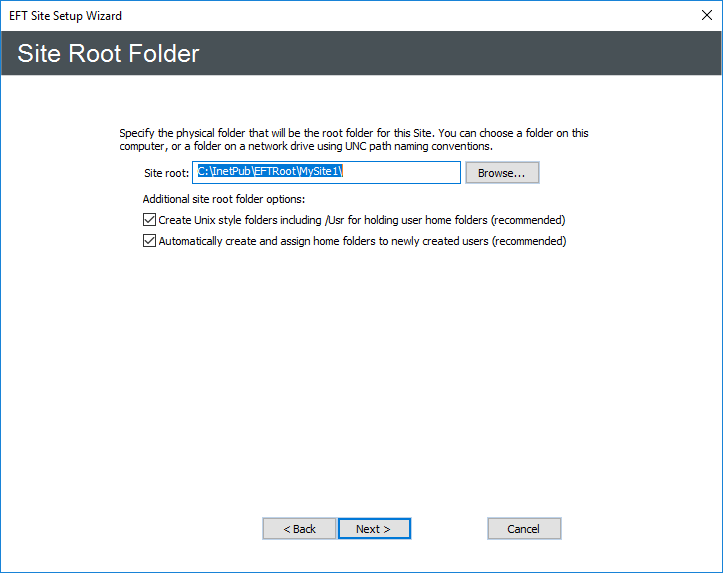
- Click Next. The Site Root Folder page appears.
- In the Site root box, click Browse to specify the root folder or keep the default displayed in the box. If you type a folder name that does not exist, it will be created.
- In the Additional site root folder options area, select the check boxes as needed:
- Select the Automatically create UNIX-style subfolders check box to create Usr, Pub, Bin, and Incoming folders with appropriate permissions under the Site's root folder. This is only necessary if you are trying to mimic a typical default *nix EFT setup. It is selected by default.
- Select the Automatically create and assign home folders to newly created users check box to automatically create a user folder under \Site Root\Usr\ when a new user is added. The folder name is the same as the username. For example, username jbite would have the folder C:\InetPub\EFTRoot\MySite\Usr\jbite.
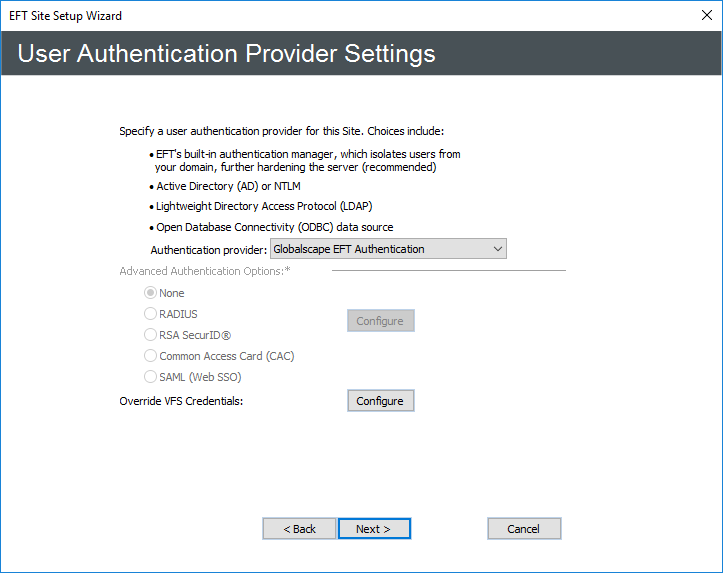
- Click Next. The User Authentication Provider page appears.
- Under Advanced Authentication Options, configure one of the following options (Requires AAMM):
- None - If you are not using RADIUS, RSA, or Common Access Card (CAC), or SAML (WebSSO)
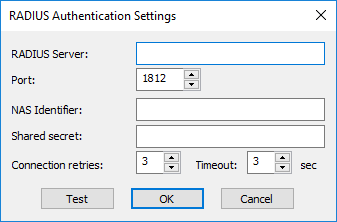
- RADIUS - If EFT is connecting to a server using RADIUS, click Configure. The applicable Settings dialog box appears:
- In the RADIUS Server box, provide the name of the RADIUS Server (host name or IP address).
- In the RADIUS Server Port box, provide the port the RADIUS Server is bound to. The default port is 1812.
- In the NAS Identifier box, provide EFT’s NAS identifier for the RADIUS Server.
- In the Shared secret box, provide the shared secret used to encrypt and sign packets between EFT and the RADIUS Server.
- In the Connection Retries box, specify the number of times a RADIUS packet will be submitted to the server before giving up. The packet is resubmitted if there is no response from the server. (RADIUS runs over UDP, so packets may be dropped or ignored by the server). The default is 3 retries.
- In the Timeout box, specify how long to wait for a server response, in seconds. The default is 3 seconds.
-
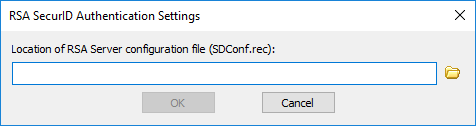
RSA SecurID - If EFT is connecting to a server using RADIUS, click Configure. The RSA SecurID Authentication Settings dialog box appears.
-
Click the folder icon to specify the location of the RSA Server configuration file (SDConf.rec), and then click OK.
-
Common Access Card (CAC) - If this Site is using CAC authentication, no further configuration of EFT is required. (Available only on LDAP Sites)
-
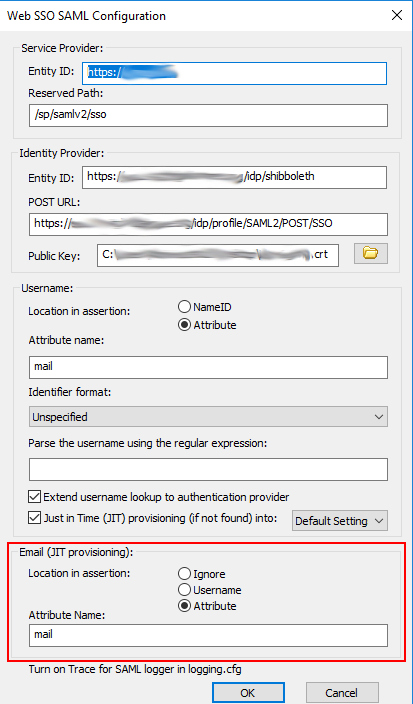
SAML (WEb SSO) - If this Site is using SAML (WebSSO), click Configure and provide the details needed to configure SAML, then click OK.
-
Service Provider:
-
Entity ID - The default is the host name value specified for the EFT Site being configured, e.g., MySite. Any string value can be provided, up 255 characters, including UTF-8 encoded characters.
-
Reserved Path - The base address followed by the SSO path, e.g., [hostaddress]/sp/samlv2/sso.
-
Identity Provider:
-
Entity ID - The Identity Provider's host name
-
POST URL - The Identity Provider's POST URL or endpoint that EFT should bind to.
-
Public Key - Certificate path to be used for verifying the server's identity
-
Username:
-
Location in assertion - Specify whether the username is stored as NameID or Attribute.
-
Attribute name - If Attribute is specified for location, provide the Attribute name.
-
Identifier format - Select the list box and click the format identifier from the list:
-
Turn on "Trace" for SAMLSSO logger in logging.cfg
-
In the Authentication provider list, specify the type of user authentication this Site is to use. (Click a link below to skip to that section.)
-
Globalscape EFT Authentication - Does not rely on outside sources for user information. All information in the authentication database is protected from the operating system, contained within EFT, and can only be modified through the administration interface.
-
Windows Active Directory (AD) Authentication - Connects to an AD server for user information.
-
LDAP Authentication - Connects to an LDAP server for user information.
-
ODBC Authentication - Connects to an ODBC database for user information.
-
Verify that Globalscape EFT Authentication is specified, and then The EFT Server Authentication page appears.
-
The default path to store the user database appears in the box. If you want to store the user database in a different location, type the path in the box or click the folder icon to find and select or create a folder.
-
Click Next. The Perimeter Network Security page appears.
-
EFT is installed by default under the "local system" account, which cannot log in to AD. EFT must be running under an account that has permission to access the domain controller (that is, create a domain account for EFT). Each Site can connect to only one domain. To connect to multiple domains, you must create multiple AD Sites.
-
In the Authentication type list, click Windows Active Directory Authentication.
-
Click Next. A prompt appears to remind you that you need to specify a different "Log on as" user for EFT.
-
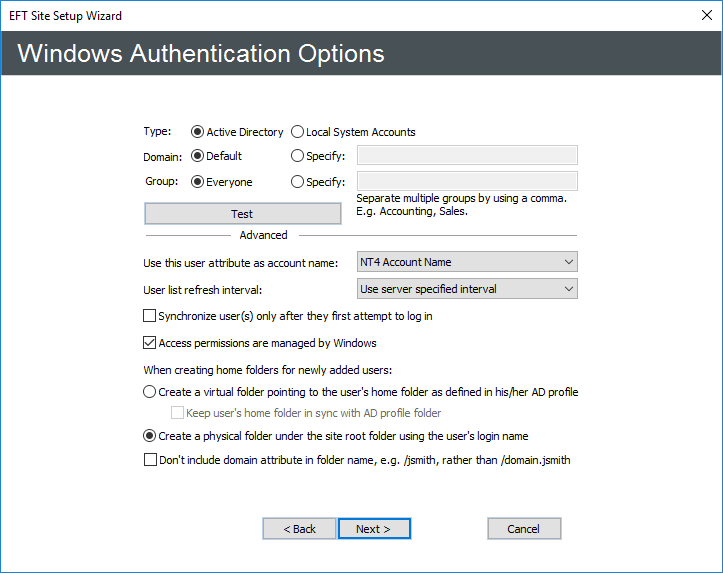
Click OK. The Windows Authentication Options page appears.
-
In the Type area, click Active Directory or NTLM/Local System Accounts to match the authentication method used on EFT's domain. Authentication is done with Microsoft's LogonUser() function in Windows. The operating system then determines which method to use for authentication, such as Kerberos, NTLM2, etc.
-
Active Directory - EFT queries the domain controller for the list of users and groups.
-
NTLM Authentication/Local System Accounts - EFT queries the local system to get the list of users and groups.
-
In the Domain area, do one of the following:
-
Click Default if you want to use the authentication database on the computer's current domain.
-
Click Specify, then in the box, provide the domain name that contains the authentication database.
-
In the Group area, do one of the following:
-
To allow access to every user in the domain's database, click Everyone.
-
To allow access to only a specific AD Group, click Specify, then in the box, type the AD group name for users that will have access to EFT.
-
To verify your settings, click Test.
-
To close the Test dialog box, press ESC.
-
In the Use this user attribute as the logon name box, click the list to specify the attribute to use (only available when AD authentication is selected):
-
NT 4 Account Name - Username
-
Display Name - (DN) When a new user is created in Active Directory, the Full name field is always generated in FirstName LastName format. This field sets the Display Name field on creation, and you end up with a FirstName LastName formatted global address list.
-
User Principal Name - (UPN) For example, your_user_name@mycompany.com
-
Common Name - (CN) fully qualified domain name, computer name (netbios), localhost
-
In the User list refresh interval box, click the list to select how often you want EFT to check the authentication database for new users (server specified, never, or from 5 minutes to 1 day).
-
To use AD to authenticate users both in the portal and in the Outlook Add-In using EFT permissions for folder access, select the Access permissions are managed by Windows check box. This property is read-only after the Site is created.
-
The VFS subtree in EFT is manageable and works similarly to non-AD-authenticated Sites.
-
The Groups node works similarly to non-AD-authenticated Sites.
-
When the user account log in to the Site (via HTTP/FTP/etc.), EFT uses the credentials (username+password or IWA) to authenticate the client against AD/NTLM, then discards the impersonation token, and all further file/folder operations are done on behalf of EFT's system account, similarly to non-AD-authenticated Sites.
-
Access permission is defined by EFT in VFS.
-
Create a virtual folder and Keep user's home folder check boxes are grayed out in the Site wizard and the Site General tab. These measures prevent clients from getting their EFT home folder mapped to their AD home folder, which most likely does not have access permissions for EFT's system account.
-
EFT does not show the standard "The service may not have adequate permissions depending on your AD configurations" prompt when the administrator starts editing Site authentication manager settings.
-
The authentication manager property is exposed via COM (ICIADAuthManagerSettings interface):
-
Under When creating home folders for newly created users, do one of the following:
-
If you click Create a physical folder, and if NT4 Account Name was selected as logon attribute, you can choose to not include the domain in the folder name by selecting the Don't include domain attribute in folder name, e.g., /jsmith, rather than /domain.jsmith check box.
-
If you click Create a virtual folder, the virtual folder will point to the user's home folder as defined in his/her AD profile. (This option is disabled if Automatically create and assign home folders to newly created users is disabled.)
-
To keep the users' home folders updated based on the AD profile folder for the user, select the Keep user's home folder in sync with AD profile folder check box. Selecting this check box allows AD users that are configured with a home folder in AD to successfully create and share a Workspace.
-
Skip to configuring Perimeter Network Security.
-
If you are using Common Access Card (CAC) authentication, click Common Access Card (CAC) authentication. (The Configure button applies only to RADIUS and RSA.)
-
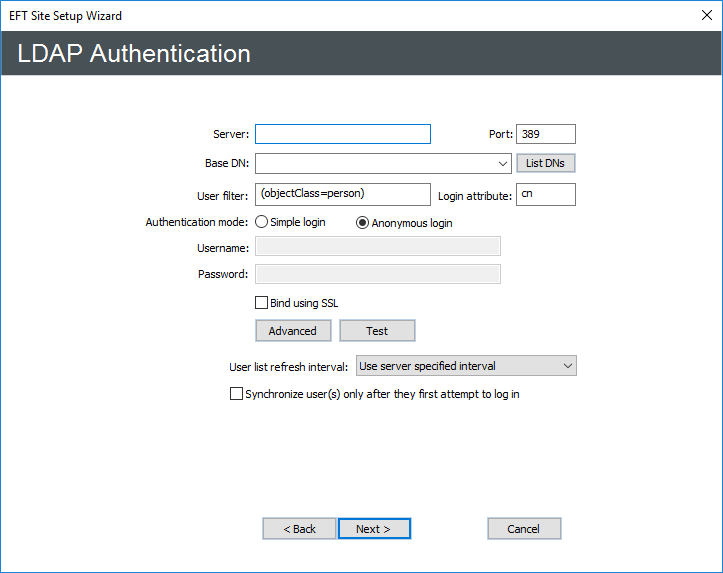
In the Authentication type list, click LDAP Authentication, then click Next. The LDAP Authentication page appears.
-
In the Server box, type the Server name or IP address.
-
In the Port box, keep the default port 389 or specify a different port used by your LDAP server.
-
In the Base DN box, type the base domain name for the LDAP user database, in the format option=value (e.g.: dc=forest,dc=tree,dc=branch), or click List DNs to complete the box automatically or select from a list.
-
In the User Filter box, type the search filter information. Refer to Advanced LDAP Filtering for a detailed explanation of LDAP filtering.
-
In the Login Attribute box, type a comma-separated list of attributes to retrieve. Add userprincipalname to the LDAP query so that the userprincipalname is used for the account name in queries. For example, type:
userprincipalname,mail,email,name,cn
-
In the Authentication mode area, click one of the following binding methods to define how the client is authenticated:
-
Simple requires a username and password. If Active Directory is acting as the LDAP provider, then providing credentials the DOMAIN\username style is sufficient. The credentials provided are typically those of the service account, and the user does not need to have any elevated privileges on the AD domain, only a Domain User. Otherwise, the username must follow the syntax for the LDAP server that includes the Common Name and the Domain Components of your LDAP server’s distinguished name. For example, the username might be the following:
-
If you want to encrypt LDAP communications, select the Bind Using SSL check box.
-
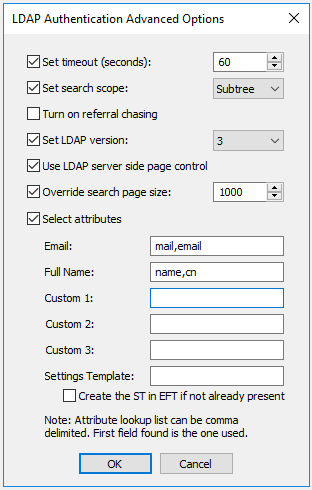
Click Advanced. The LDAP Authentication Advanced Options dialog box appears.
-
Specify advanced options based on your requirements:
-
Set timeout - Specify the connection/query timeout (in seconds). This option coupled with paging can help you avoid timeouts when querying against large directories.
-
Set search scope - This specifies the depth of the level to search for under BaseDN.
-
BASE - Only the requested object specified in BaseDN is searched.
-
OneLevel - All of the objects just below this object are searched.
-
Subtree - Searches for all the objects within the specified BaseDN object recursively.
-
Turn on referral chasing - If you have referral chasing on, the query returns information for objects that exist in the LDAP structure, but do not actually exist on EFT to which you are connected. The query displays bookmarks to entries that exist elsewhere in the network that EFT knows about.
-
Set LDAP Version - LDAP 2 is widely supported and adds anonymous binding and some filtering. LDAP 3 extends the features of LDAP 2 by adding paging (server side) and more complex filtering.
-
Use LDAP server-side page control - Asks EFT to limit result sets (or pages) to 1000 at a time or the value specified under Override search page size, if checked. If Use server page control is not selected, client-side paging is used to mitigate timeouts when retrieving large directory listings.
-
Override search page size - Overrides the default page size (1000) for client or server-side page limits. Making the value too large can cause timeouts. Setting the page size too small reduces the overall efficiency.
-
Select attributes - Select the Select attributes check box, then specify the LDAP attributes that you want to use, such as cn (common name), streetAddress, mail (email address), employeeID, employeeType, etc.
-
Multiple attributes can be added to each custom field, but only the first attribute found will be used; All other attributes will be ignored.
-
An attribute field on the LDAP server can contain multiple attributes if you want multiple attributes added to a single custom field, such as for the address.
-
Refer to Map LDAP Account Attributes to EFT User Account Details for more information about LDAP account attributes.
-
Click OK to close the LDAP Authentication Advanced Options dialog box.
-
To test your settings, click Test. The Authentication Manager Test Results appear. For details of the LDAP test, refer to Testing LDAP Authentication Settings.
-
Click the X in the upper right corner to close the dialog box.
-
Specify the path at which EFT will store additional user settings, if different from the default shown in the wizard.
-
In the User list refresh interval box, specify the frequency at which EFT's user list should be refreshed. By default, the Server is configured to not refresh automatically.
-
Skip to configuring Perimeter Network Security.
-
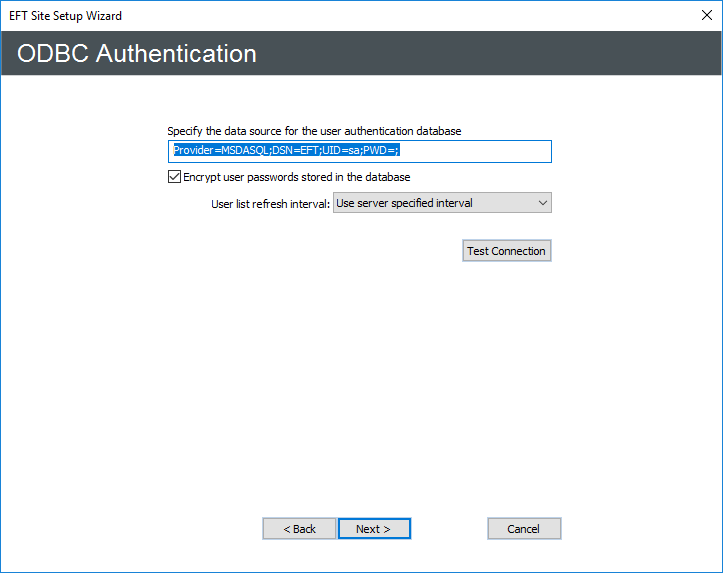
Click Next. The ODBC Authentication page appears.
-
In the Specify the data source box, type a connection string for the ODBC database. Refer to Using a DSN-Less Connection with ODBC Authentication for details of creating the connection string, if necessary.
-
Select the Encrypt user passwords check box to encrypt passwords stored in the database. When this check box is selected, when you create user accounts within EFT, the ODBC database is populated with the username and a SHA-256 hash of the account password. Alternatively, you can set a value in the registry to use MD5 encrypted passwords instead.
-
In the User list refresh interval list, click the list to specify how often you want EFT to check the database for new users.
-
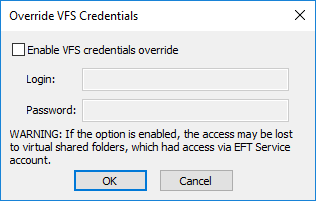
If you will be using EFT with Azure Data-Lake Storage, next to Override VFS Credentials, click Configure. (You configure it later if you don't have the credentials available.) The Override VFS Credentials dialog box appears.
-
Select the Enable VFS credentials override check box. The Login and Password boxes become enabled.
-
Provide the credentials for your Azure Data-Lake supported container and the security key (password), then click OK.
-
Specify whether to connect the Site to DMZ Gateway.
-
If you choose to connect to DMZ Gateway, specify its IP address and port, and then click Test Connection. If the DMZ Gateway is properly configured, the test is successful. If the test is not successful, click I'm not using the DMZ Gateway - or I'll configure it later.
-
If you have not yet installed or configured DMZ Gateway Server, click I'm not using the DMZ Gateway - or I'll configure it later.
-
Click Next. The Connection Protocols page appears.
-
Select one or more check boxes for the protocol(s) that this Site will use to connect to EFT and specify the port number for each protocol. The default ports appear in the boxes.
-
Specify the SSL certificate to use for this Site. Click SSL certs. The SSL Certificate Options page appears.
-
To create a certificate, click Create certificate and follow the prompts in the wizard. (Refer to Creating Certificates for details, if necessary.)
-
To use an existing certificate:
-
In the Certificate box, type the path to the .crt file or click the folder icon to find and select it.
-
In the Private key box, type the path to the .key file or click the folder icon to find and select it.
-
In the Certificate passphrase and Confirm passphrase boxes, type and confirm the passphrase for the certificate pair.
-
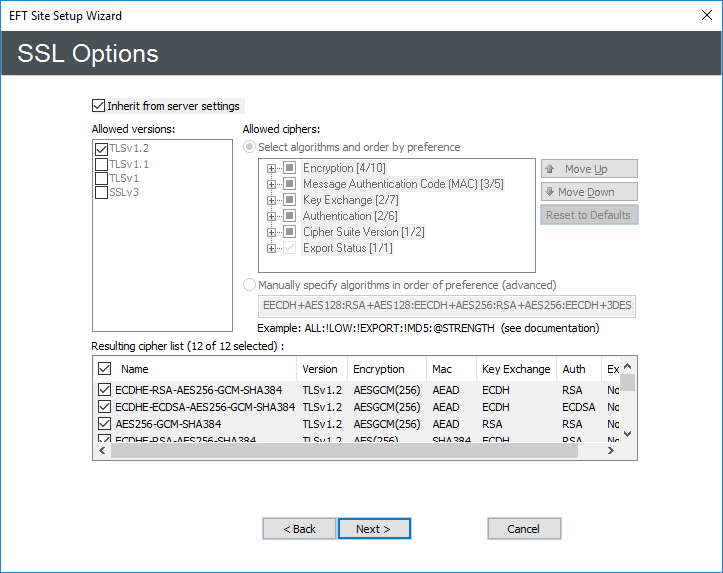
If you are using SSL, click SSL options:
-
(In v8.0.5 and later) Select the Inherit from server settings check box if you want the Site to use the same configuration, or clear the check box to select different options.
-
TSLv1.2 is the only version selected by default in v8.0.5. Select other versions and/or ciphers as needed.
-
Click Next to return to the Protocols page.
-
(If you are using SFTP) Click SFTP keys to configure an SFTP key pair. The SFTP Keys wizard appears.
-
Do one of the following:
-
Click the folder to browse for a key, then enter the passphrase.
-
Click Create to create a new key. The Create SSK2 Public/Private Keypair wizard appears.
-
Specify a name, location, format, and bit length of the key pair, and then click Next.
-
Specify and confirm the passphrase to encrypt the private key, and then click Next.
-
Specify whether to use this key as the default host key and whether to copy the public key to the SSH key manager, and then click Finish.
-
After the key is generated, click Finish.
-
You are returned to the Site Setup wizard Protocols page. Click SFTP Security. The SFTP Options page appears.
-
(In v8.0.5 and later) Select the Inherit options from server settings to use the same configuration as the server, or clear the check box to select different options.
-
Select the algorithms and ciphers as needed, then click Next.
-
If you chose AS2, click Configure. The AS2 Setup Wizard appears. Click Next.
-
Specify Your AS2 identifier. There is no standard for the AS2 Identifier. You can use your name, your company's name, or some other unique name. EFT validates the AS2 identifier to determine whether it is unique (not used by another partner on this EFT). If you type an ID that is not unique, the field resets to blank. Click Next.
-
Specify the AS2 Certificate public path key, Certificate private key path, and Certificate private key passphrase, populated by default with the SSL certificate paths (if present) for EFT SSL communications. Click the folder icons to specify a certificate pair or click the blue create link to open the SSL certificate wizard to create a new certificate pair. (You can use the same SSL certificate that you are using for the Site.) Click Next.
-
Click Finish.
-
Click Next. The Site Setup Completed page appears.
-
If you specified Globalscape authentication, you are offered the option of running the user creation wizard or quitting the Site Setup wizard and creating users later. Click an option, then click Finish.
-
If you chose Run New User Creation wizard, the User Creation wizard Welcome page appears. Continue to Creating User Accounts for the procedure.
The EFT Site Setup Wizard appears.
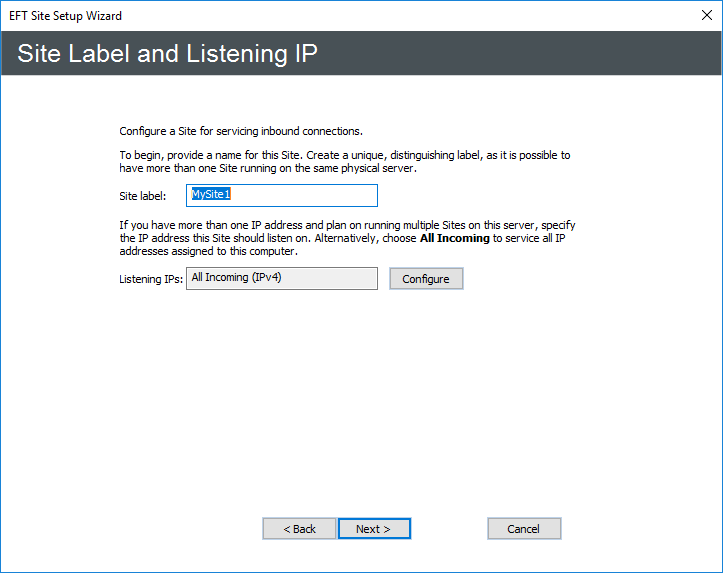
The Site name cannot have a period at the end of the name or use any characters that are not allowed in Windows file naming. The Site label is also used in the Virtual File System (for example, C:\Inetpub\EFTRoot\MySite\Usr) and in logs and reports.
On an AD-authenticated Site, if Automatically create and assign home folders to newly created users is enabled, EFT creates a virtual folder under the Site's physical root that points to the user's home folders assigned in AD. If Automatically create and assign home folders to newly created users is disabled, the functions for creating virtual or physical folders for AD users are disabled.
 M
M
For Globalscape EFT Authentication
For Windows Active Directory Authentication
If EFT is installed in HA mode, you cannot use Local System Accounts.
For information about support for foreign groups, refer to Support for Foreign Groups.
Regardless of the logon name chosen, EFT will accept the provided logon name type, whether UPN, NT4 account name, common name, or display name, and if a match exists, the user will be authenticated and the chosen logon name type will be displayed in the administration interface.
|
Logon name type |
Allowed login form |
|---|---|
|
NT4 Account Name (NT4) |
NT4/UPN |
|
Display Name (DN) |
DN/NT4/UPN |
|
User Principal Name (UPN) |
UPN/NT4 |
|
Common Name (CN) |
CN/NT4/UPN |
If this check box is NOT selected (disabled/turned off):
HRESULT UseWindowsAccessPermissions([out, retval] VARIANT_BOOL* pVal); HRESULT UseWindowsAccessPermissions([in] VARIANT_BOOL newVal);
cn=Manager,dc=forest,dc=tree,dc=branch
The LDAP bind password is encrypted in the FTP.cfg file.
If Microsoft’s Active Directory is the LDAP provider, Certificate Services must be enabled on the domain before domain controllers will be able to receive encrypted LDAP connections.
If you are connecting to a SUN Directory LDAP server, turn off page control.
This setting is disabled on HA nodes; the user list must be synchronized on all nodes at the same time.
You change the refresh interval later in the Authentication Options dialog box.
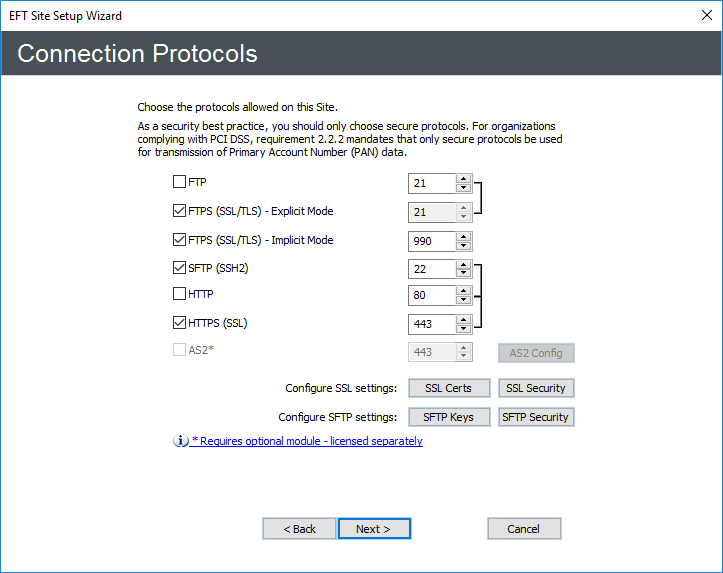
By default, the FTP server in Microsoft IIS binds to port 21 on all IP addresses. If you want to run both the IIS FTP server and EFT, you need to disable socket pooling for the IIS FTP server.
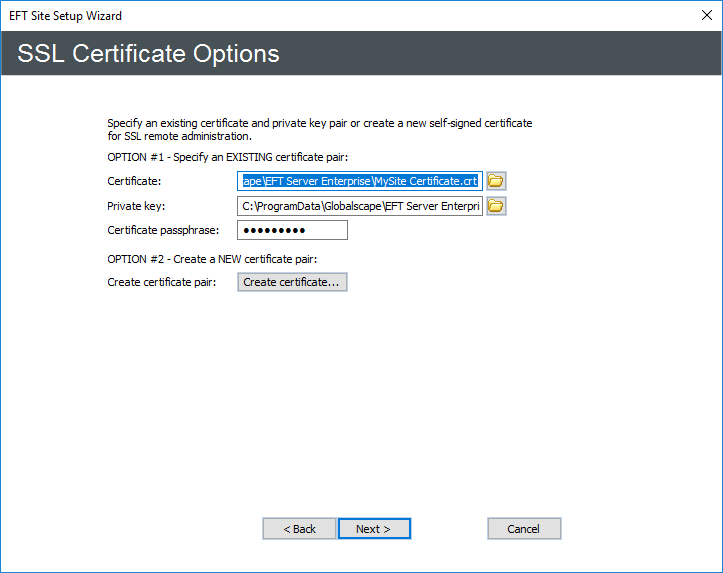
If you do not enable SSL, you will not be able to connect to EFT from a remote administration interface. Refer to SSL Certificate-Based Login, Creating Certificates and Importing a Certificate into the Trusted Certificate Database for information regarding certificates.
-- or --
You can run the Site Setup wizard again at any time to create additional Sites.
You can view and modify individual Site settings in the administration interface.