Changing and Testing LDAP Authentication Options
(Available in EFT Enterprise)
The LDAP Authentication Options dialog box is used to edit and test EFT's connection to the LDAP server after you have configured LDAP Authentication.
To edit or test LDAP authentication settings
-
In the administration interface, connect to EFT and click the Server tab.
-
On the Server tab, click the LDAP Site that you want to configure.
-
In the right pane, click the General tab.
-
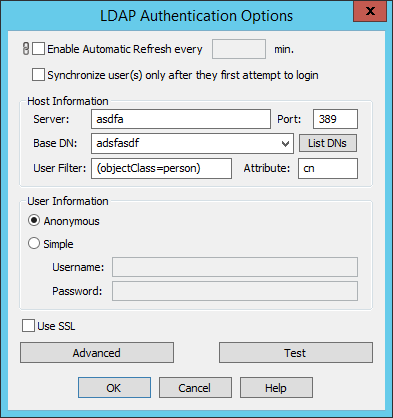
Next to the User auth manager box, click Configure. The LDAP Authentication Options dialog box appears.
-
To specify that the user list is to be updated automatically, select the Enable Automatic Refresh every check box, then specify how often you want EFT to check the authentication database for new users. Clear the check box if you do not want the Site's user list to refresh automatically. (This setting is inherited from the Server's General Settings on the Server's General tab. Never refresh user list automatically is specified by default.)
-
Select the Synchronize users only after they first attempt to log in check box to specify whether to load the whole LDAP user database into EFT at once or to pull users one-by-one after successful logins.
-
In the Server box, type the Server name or IP address.
-
In the Port box, keep the default port 389 or specify a different port.
-
LDAPS communication occurs over port TCP 636.
-
LDAPS communication to a global catalog server occurs over TCP 3269.
-
When connecting to ports 636 or 3269, SSL/TLS is negotiated before any LDAP traffic is exchanged.
-
LDAP over SSL must be enabled to effectively change your password via WTC.
-
In the Base DN box, type the base domain name for the LDAP user database, in the format option=value (e.g.: dc=forest,dc=tree,dc=branch), or click List DNs to complete the box automatically or select from a list.
-
In the User Filter box, type the search filter information. Refer to Advanced LDAP Filtering for a detailed explanation of LDAP filtering. For example:
-
In the Attribute box, type a comma-separated list of attributes to retrieve. For example, type:
-
In the User Information area, click one of the following binding methods to define how the client is authenticated:
-
Simple requires a username and password. Note that the username must follow the syntax for the LDAP server that includes the Common Name and the Domain Components of your LDAP server’s distinguished name. For example, the username might be the following:
-
If you are using SSL, select the Use SSL check box.
-
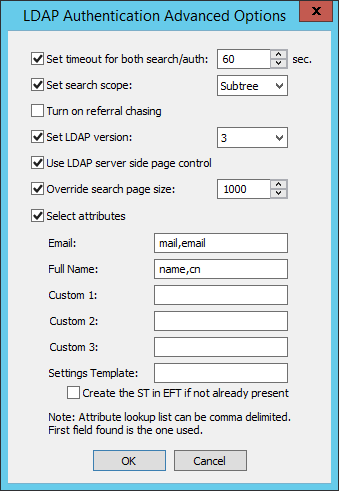
To change the advanced options (SSL, timeout, scope, etc.), click Advanced and specify advanced options based on your requirements.
-
Set timeout for both search/auth - Specify the connection/query and authentication timeout (in seconds). This option coupled with paging can help you avoid timeouts when querying against large directories. The default is 60 seconds.
-
Set search scope - This specifies the depth of the level to search for under BaseDN.
-
BASE - Only the requested object specified in BaseDN is searched.
-
OneLevel - All of the objects just below this object are searched.
-
Subtree - Searches for all the objects within the specified BaseDN object recursively.
-
Turn on referral chasing - If you have referral chasing on, the query returns information for objects that exist in the LDAP structure, but do not actually exist on EFT to which you are connected. The query displays bookmarks to entries that exist elsewhere in the network that EFT knows about.
-
Set LDAP Version - LDAP 2 is widely supported and adds anonymous binding and some filtering. LDAP 3 extends the features of LDAP 2 by adding paging (server side) and more complex filtering.
-
Use LDAP server-side page control - Asks EFT to limit result sets (or pages) to 1000 at a time or the value specified under Override search page size, if checked. If Use server page control is not selected, client-side paging is used to mitigate timeouts when retrieving large directory listings.
-
Override search page size - Overrides the default page size (1000) for client or server-side page limits. Making the value too large can cause timeouts. Setting the page size too small reduces the overall efficiency.
-
Select attributes - Returns only the specified attributes for the user objects found as part of the search query. Specifying only necessary attributes will greatly increase the efficiency of your query (since the filtering occurs on EFT side). Add userprincipalname to the LDAP query so that the userprincipalname is used for the account name in queries.
-
For details of specifying Custom attributes, refer to Allow LDAP Authentication through DMZ.
-
Settings Template - Provide the Settings Template name for these users; select the Create ST in EFT if not already present check box.
-
To test your settings, click Test. The query returns information about your LDAP connection.
-
To close the dialog box, click the X in the upper right corner or press ESC.
-
Click OK to close the LDAP Authentication Options dialog box.
-
Click Apply to save the changes on EFT.
The user list is not refreshed automatically when a Site is stopped for Server startup; user database synchronization timer; or administrator changes related to the user database. You can manually refresh the user database by clicking View > Refresh User Database on the main menu.
(&(memberof=CN=eft users,cn=Users,dc=demo,dc=vm)(objectclass=person))
(&(memberof=CN=eft users,cn=Users,dc=forest,dc=tree)(objectclass=person))
userPrincipalName,mail,email,name,cn
(Add userprincipalname to the attributes so that the userprincipalname is used for the account name in queries.)
cn=Manager,dc=forest,dc=tree,dc=branch
For details of creating complex LDAP filters, refer to Advanced LDAP Filtering.
You need to have a certificate that includes Server Authentication on the LDAP server you are connecting to. If you install Certificate Services on the domain on which EFT is installed, you can request the certificate on the LDAP server. For more information, refer to the Microsoft Support article "How to enable LDAP over SSL with a third-party certification authority."
If you are connecting to a SUN Directory LDAP server, turn off page control. See more information at Using Sun Directory LDAP Server.