Creating an SSH Key Pair
(Requires the SFTP module) In the administration interface, you can define an SSH key pair for EFT and connecting clients. A wizard walks you through each step to create and store the key pair files.
For the KEX ciphers, there a few configuration changes to note:
-
On a new installation, diffie-hellman-group-exchange-sha256 and diffie-hellman-group14-sha1 should be enabled.
-
diffie-hellman-group14-sha1 should be left enabled for compatibility in accordance with the most recent SSH RFC draft recommendations (dated March 27th, 2017):
"diffie-hellman-group14-sha1 method SHOULD- be retained for compatibility with older Secure Shell implementations. It is intended that this key exchange method be phased out as soon as possible" https://tools.ietf.org/html/draft-ietf-curdle-ssh-kex-sha2-07 -
On upgrade, existing selected KEX methods should persist.
-
An advanced property to disable/enable diffie-hellman-group1-sha1 (https://kb.globalscape.com/KnowledgebaseArticle11266.aspx) should become inactive in place of the administration interface selections.
To create a key pair
-
On the main menu, click Tools >Create SSH2 Key.
The Create SSH2 Public/Private Keypair wizard appears.
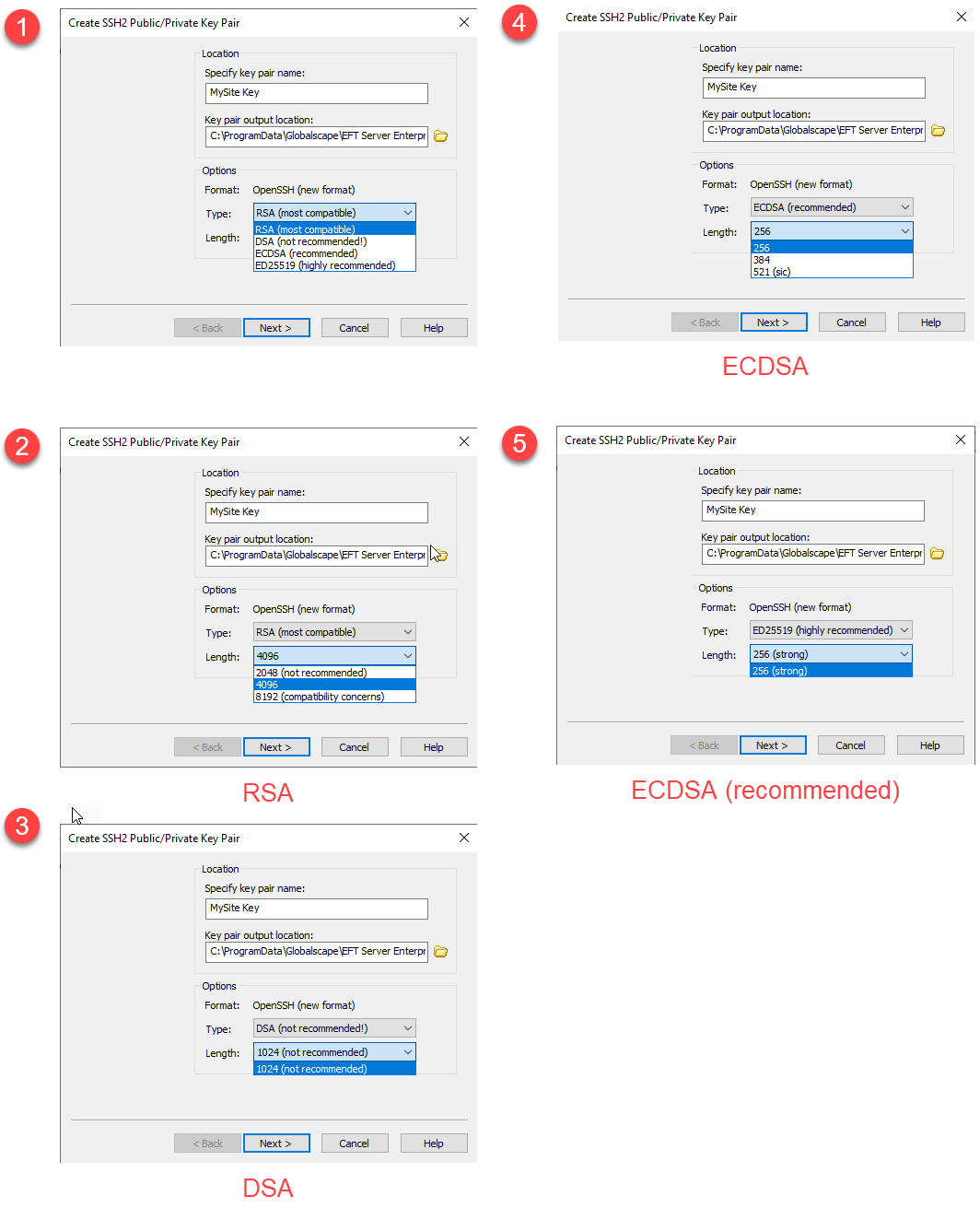
-
Specify a name for the key pair. The default is "New SSH Key," but you can name it anything. (You are prompted to specify a different name if a key with the same name exists.)
-
Specify a location in which to store the key pair.
-
In the Options area:
-
Select the length.
-
Select the type (algorithm):
You can choose the algorithm and bit length when creating new keys.
Algorithm
Length
RSA (most compatible)
2048 (not recommended)
4096
8192 (compatibility concerns)
DSA (not recommended!)
1024 (not recommended)
ECDSA (recommended)
256
384
521 (sic)
Ed25519 (highly recommended)
256 (strong)
RSA 4096 are the defaults for new installations. See https://www.ssh.com/ssh/keygen/ for more information. Key algorithms with a single choice show that length value appears dimmed, as those cannot be edited.
-
-
Click Next. The password page of the wizard appears.

-
Provide and confirm the passphrase used to encrypt the private key. The passphrase cannot contain more than 256 characters, cannot contain only spaces and periods, and cannot contain the following characters:
/ (forward slash)
\ (back slash)
[ (left bracket)
] (right bracket)
; (semicolon)
: (colon)
| (pipe)
= (equal sign)
, (comma)
+ (PLUS sign)
? (question mark)
< (left angle bracket)
> (right angle bracket)
{ (left curly brace)
} (right curly brace
-
Click Next.
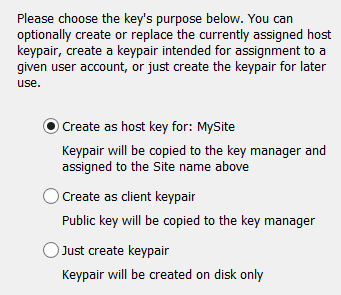
-
Choose the key's purpose:
-
If you want to use this key to authenticate EFT for inbound transactions, click Create as host key for: <Site Name>.
The keypair is copied to the SSH Key Manager and assigned to the Site on which you create the key. -
If you want EFT to import the public part of the key into the SSH key manager, click Create as client keypair.
The private key for client is stored on client's side. EFT doesn't store it. It is the administrator's responsibility to securely send this private key to a user, so the user can use it with SFTP clients (for example, CuteFTP®). -
If you only want to create a keypair on disk, click Just create keypair.
-
Click Finish. If you used the default location to store the key pair, the files are is saved in C:\ProgramData\Globalscape\EFT Server\.
Copying the public key to the key manager is unnecessary unless you created this key pair for your partner. For security best practices, your partners should create their own key pairs, then give you a copy of their public key, which you would then import into the SSH key manager.
PowerShell Example
Refer to the COM API help for details of using the CreatSSHKeyPair method.
In PowerShell, use the following example:
$privateKeyFile = New-Object Object $publickKeyFile = New-Object Object #define VariantWrapper for variables to be passed as VARIANT $wrappedPublic = New-Object Runtime.InteropServices.VariantWrapper($publickKeyFile) $wrappedPrivate = New-Object Runtime.InteropServices.VariantWrapper($privateKeyFile) #pass a [ref]VariantWrapper to .COM method $site.CreateSSHKeyPair($ssha_rsa_type+$keyBits, "siteSSHKeyPass", [ref]$wrappedPublic, [ref]$wrappedPrivate)
Available MACs
The following are a list of available MACs
-
hmac-sha2-512-etm@openssh.com (enabled by default/secure) Added in v8.0.4
-
hmac-sha2-512 (enabled by default/secure)
-
hmac-sha2-256-etm@openssh.com (enabled by default/secure) Added in v8.0.4
-
hmac-sha2-256 (enabled by default/secure)
-
hmac-sha1-etm@openssh.com (enabled by default/secure) Added in v8.0.4
-
hmac-sha1 (enabled by default/secure)
-
umac-64-etm@openssh.com (enabled by default) Added in v8.0.4
-
umac-64@openssh.com (enabled by default)
-
hmac-md5 (disabled by default/less secure) In v8.0.2, this MAC was changed to disabled
-
hmac-sha1-96 (disabled by default/less secure) In v8.0.2, this MAC was changed to disabled
-
hmac-md5-96 (disabled by default/less secure) In v8.0.2, this MAC was changed to disabled
The MACs below can be enabled/disabled by changing their Advanced Properties in the AdvancedProperties.json
|
Advanced Property |
Description |
|---|---|
|
SFTP2_HMAC_SHA2_512_ETM_AT_OPENSSH_COM |
Type: bool Default Value: true Description: Setting to true enables the hmac-sha2-512-etm@openssh.com algorithm. Can be disabled for outbound client connections via Advanced Property SFTP2_HMAC_SHA2_512_ETM_AT_OPENSSH_COM to false |
|
SFTP2_SHA2_512 |
Type: bool Default Value: true Description: Setting to true enables the SHA2_512 MAC algorithm. hmac-sha2-512 can be disabled for outbound client connections via Advanced Property SFTP2_SHA2_512 to false |
|
SFTP2_HMAC_SHA2_256_ETM_AT_OPENSSH_COM |
Type: bool Default Value: true Description: Setting to true enables the hmac-sha2-256-etm@openssh.com algorithm hmac-sha2-256-etm@openssh.com can be disabled for outbound client connections via Advanced Property SFTP2_HMAC_SHA2_256_ETM_AT_OPENSSH_COM to false |
|
SFTP2_SHA2_256 |
Type: bool Default Value: true Description: Setting to true enables the SHA2_256 MAC algorithm. hmac-sha2-256 can be disabled for outbound client connections via Advanced Property SFTP2_SHA2_256 to false |
|
SFTP2_HMAC_SHA1_ETM_AT_OPENSSH_COM |
Type: bool Default Value: true Description: Setting to true enables the hmac-sha1-etm@openssh.com algorithm. hmac-sha1-etm@openssh.com can be disabled for outbound client connections via Advanced Property SFTP2_HMAC_SHA1_ETM_AT_OPENSSH_COM to false |
|
SFTP2_SHA1 |
Type: bool Default Value: true Description: Setting to true enables the SHA1 MAC algorithm. hmac-sha1 can be disabled for outbound client connections via Advanced Property SFTP2_SHA1 to false |
|
SFTP2_UMAC_64_ETM_AT_OPENSSH_COM |
Type: bool Default Value: true Description: Setting to true enables the umac-64-etm@openssh.com algorithm. umac-64-etm@openssh.com can be disabled for outbound client connections via Advanced Property SFTP2_UMAC_64_ETM_AT_OPENSSH_COM to false |
|
SFTP2_UMAC_64_AT_OPENSSH_COM
|
Type: bool Default Value: true Description: Setting to true enables the umac-64@openssh.com algorithm. umac-64@openssh.com can be disabled for outbound client connections via Advanced Property SFTP2_UMAC_64_AT_OPENSSH_COM to false |
|
SFTP2_MD5 |
Type: bool Default Value: false Description: Setting to true enables the MD5 MAC algorithm. hmac-md5 can be ENABLED for outbound client connections via Advanced Property SFTP2_MD5 to true |
|
SFTP2_SHA1_96 |
Type: bool Default Value: false Description: Setting to true enables the SHA1_96 MAC algorithm. hmac-sha1-96 can be ENABLED for outbound client connections via SFTP2_SHA1_96 to true |
|
SFTP2_MD5_96 |
Type: bool Default Value: false Description: Setting to true enables the MD5_96 MAC algorithm. hmac-md5-96 can be ENABLED for outbound client connections via Advanced Property SFTP2_MD5_96 to true |
Related Topics