Introduction to DMZ Gateway®
DMZ Gateway® is designed to reside in the demilitarized zone and provide secure communication with a server behind intranet firewalls without requiring any inbound firewall holes between the internal network and the DMZ, and with no sensitive data stored in the DMZ, even temporarily. DMZ Gateway supports connections to EFT using Profiles. Depending on the license purchased, you can have up to 15 Profiles (unique IP address:port connections).
How Does It Work?
-
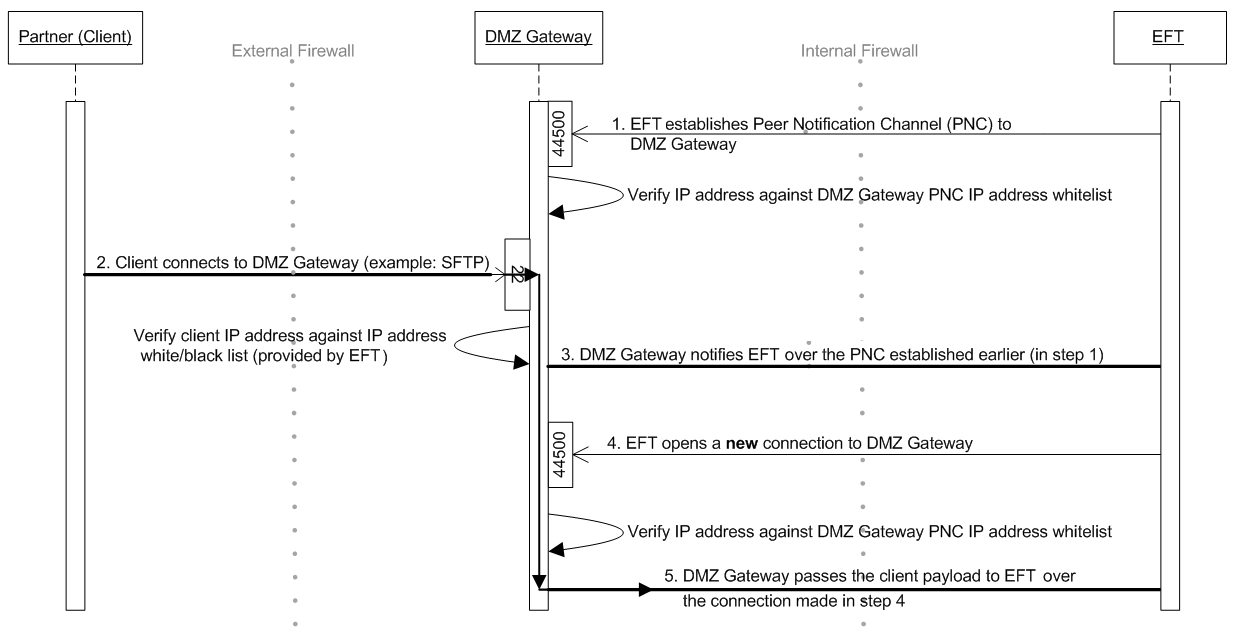
When the EFT service is started, it will establish (and maintain) an outbound connection to the DMZ Gateway. This proprietary, non-encrypted connection is called the Peer Notification Channel (PNC). EFT and DMZ Gateway use the PNC to setup subsequent communications between EFT and incoming client connections.
-
When a client (web browser, FTP client, etc.) connects to DMZ Gateway on a pre-approved port (21, 22, 80 443, etc.), DMZ Gateway will cross reference the client’s IP with the IP access list (provided by EFT over the PNC) before proceeding any further.
-
If the IP is accepted, DMZ Gateway will notify EFT over the PNC of the new client connection, providing data such as the client’s IP address and the port to which they are connected.
-
EFT will subsequently create a new outbound connection to the DMZ Gateway to the same port that is being used by the PNC for associating with the client connection made in step 2.
-
DMZ Gateway will then proceed to read the inbound payload data from the client and send the payload data to EFT for processing. DMZ Gateway will also read any outbound data communication from EFT and send it to the client.
The graphic below describes the flow in EFT: