Common Access Card Authentication
Common Access Card (CAC) Authentication is available for LDAP Sites with SSL (HTTPS or FTPS) enabled. (Requires Advanced Authentication Modes module.)
CAC and Certificates
When CAC is enabled on an LDAP Site, clients are required to provide a certificate when connecting. Once the user’s certificate is validated, EFT uses the Principal Name (UPN) or RFC822 Name taken from the Subject Alternative Name (SAN) field of the Signature Certificate to search for the user in LDAP and allow or deny access based on the information found. The certificate provisioned via the web browser must have an Electronic Data Interchange Personal Identifier (EDI/PI). If the EDI/PI is not found or otherwise cannot be validated, the connection is denied. If the EDI/PI is found, EFT maps the corresponding fields in LDAP using the appropriate LDAP query string. If the user is found in LDAP, if a certificate is assigned to that user, and if the certificate exactly matches the one provided by the client, the user is allowed access.
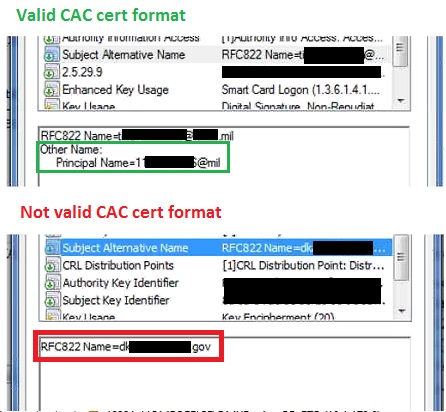
The certificate lookup process looks like this:
-
EFT looks for UPN or RFC822 Name entry in SAN field of certificate (that is, the OID)
-
EFT performs an LDAP lookup using the LDAP Auth Manager specifications, searching against the user login attribute for the value found in the entry of SAN.
-
This lookup returns 0 or more "userCertificate" properties of the matched object, if found.
-
For each returned userCertificate, EFT does a cryptographically strong comparison of the LDAP-provided certificate and the one supplied by the CAC.
CAC and WTC
-
The account management page is not available when CAC is enabled. There is no concept of logging out or changing passwords when using CAC.
-
CAC is only available on an LDAP-authenticated Site.
-
CAC is incompatible with RADIUS, RSA, PCI DSS, ODBC, NT authentication, AD authentication, and Globalscape authentication. PCI DSS Compliance reports do not report on CAC-enabled Sites.
-
Refer also to Knowledgebase article #11329, Enabling Workspaces for external users on CAC-enabled Site
-
EFT v8.x does not support UPLOADS from CAC-authenticated users when using Chrome or Edge browsers. Firefox (and possibly other browsers) will work.
When CAC is enabled on a Site:
-
Any attempt to access any of the account management pages causes a "page not found" error.
-
When HTTP and HTTPS are both enabled, the Redirect HTTP to HTTPS check box is selected and disabled, forcing redirection of HTTP traffic to HTTPS.
-
When FTPS is enabled, the username and password provided are ignored; the authentication is provided by the certificate.
-
The method EnableCAC() can be used to enable CAC via the COM API.
-
The following major events are logged:
-
Could not find proper SAN field in certificate
-
The value received from the SAN field
-
If user had no certificates in LDAP
-
If certificates were present but no certificate matched
-
More than one user was retrieved when LDAP was queried (authentication is only attempted against the first one)
Related Topics
-
Defining Connections (Sites) for details of creating an LDAP-authenticated Site that uses CAC.
-
Guidelines for enabling smart card logon with third-party certification authorities (Microsoft Support article)