EFT Client Activity Log
To monitor EFT client activity, you can reference EFT’s log files, including registration state of modules, server/site functions, SFTP, SSL/TLS connections, and of course, errors and warnings.
-
The EFT client activity log, also known as "TED6" logs, is used to log client connection information (event rules and outbound transfers), client commands/requests, remote server responses, and status messages.
-
EFT client log files are saved in the C:\ProgramData\Globalscape\EFT Server\Logs\ folder.
- The EFT<servername>.log file is the root logger and controls all logging items as defined in logging.cfg. Individual loggers can be enabled and increased in verbosity as needed. Some loggers contain sub appenders to log specific aspects.
- For information about the Audit Database logs, refer to Auditing Database Errors and Logging. (Not to be confused with Audit Database Settings.)
- For event rule logging (such as cl060312.log) refer to Event Rules Client Log.
- For installation logs, refer to Installation Logging.
- For DMZ Gateway logging, refer to DMZ Gateway Logging.
- For Windows Event Logs, refer to Windows Event Log (WEL) Action.
The EFT client activity (TED6) logs are available as W3C, Microsoft IIS, and NCSA log file formats. Depending on the log file format selected in administration interface Server > Logs tab, a 2-letter abbreviation is prepended to the filename, as described in the table below. The information in the file is the same; it's just in a different file format to accommodate different (external) log readers. Server events are logged to a file named [log file format]yymmdd.log, where YY, MM, and DD indicate the numeric year, month, and day respectively.
For example, a log file in the Microsoft IIS format created on August 22, 2024 is named in240822.log.
| Log File Format | Abbreviation |
|---|---|
|
ex |
|
|
nc |
|
|
in |
When using HA, you need to specify a unique location (local) on each node for the log files. This is for troubleshooting purposes (to know on which node an issue occurred). Also, having two nodes write to the same file causes issues with file locking, which will cause data in the logs to be lost.
To specify EFT activity log settings
-
In the administration interface, connect to EFT and click the Server tab.
-
On the Server tab, click the Server node.
-
In the right pane, click the Logs tab.
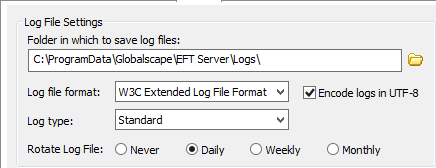
-
In the Log File Settings area, in the Folder in which to save log files box, type the path to the directory in which to save this Server's log files. To browse for a path, click the folder icon
 .
. -
In the Log file format list, click W3C Extended, Microsoft IIS, NCSA Common, or No Logging. Changing the log file format disconnects all active users. It is recommended to stop all Sites or wait until all users are inactive before changing the log file format. The W3C format records all times in GMT (Greenwich Mean Time).
-
Clear the Encode logs in UTF-8 check box if you do not want to encode logs in UTF-8 format. When the check box is cleared, the u_ex*.log file is named ex*.log.
From Microsoft TechNet:
When using the UTF-8 logging feature, note the following:
-
A log file logged in UTF-8 does not contain a Byte Order Mark (BOM). File editors use this mark to identify text as UTF-8 text. Therefore, if you attempt to open a log file that is logged in UTF-8 in Notepad by double-clicking the file or by using the Open With option, the file might not display correctly. To open the file in a way that displays it correctly, use the Open command on the File menu and then select UTF-8 in the Encoding box.
-
UTF-8 is a double-byte character-set standard. ASCII is a single-byte character-set standard. Because of this disparity, logging UTF-8 information to an ASCII file causes a ? to be logged for the characters that cannot be converted to the code page of the server.
-
-
In the Log type list, click Standard or Verbose. (Verbose provides more details, but makes larger files.)
-
In the Rotate Log File area, specify Never, Daily, Weekly, or Monthly.
-
Click Apply to save the changes on EFT.
Log Example
Below is an example of an ex-formatted log:
#Version: 1.0 #Software: CuteLogger #Date: 2010-04-08 20:07:50 #Fields: date time c-ip c-port cs-username cs-method cs-uri-stem cs-uri-query sc-status sc-bytes cs-bytes s-name s-port 2010-04-08 20:07:07 192.168.241.1 - test [1]user test - 331 - - - 22 2010-04-08 20:07:07 192.168.241.1 - test [1]pass ******* - 230 - - - 22 2010-04-08 20:07:16 192.168.241.1 - test [1]created /Test+File+1.txt - 226 - 54 - 22 2010-04-08 20:08:23 192.168.241.1 - test [1]rnfr /Test+File+1.txt - 350 - - - 22 2010-04-08 20:08:23 192.168.241.1 - test [1]rnto /Test+File+2.txt - 250 - - - 22 2010-04-08 20:08:26 192.168.241.1 - test [1]sent /Test+File+2.txt - 226 - 54 - 22 2010-04-08 20:10:02 192.168.241.1 - test [1]dele /Test+File+2.txt - 250 - - - 22 2010-04-08 20:10:08 192.168.241.1 - test [1]ssh_disconnect timeout - 421 - - - 22 2010-04-08 20:10:09 192.168.241.1 - test [1]ssh_disconnect timeout - 421 - - - 22 2010-04-08 20:11:57 192.168.241.1 - test [2]user test - 331 - - - 990 2010-04-08 20:11:57 192.168.241.1 - test [2]pass ****** - 230 - - - 990 2010-04-08 20:12:04 192.168.241.1 - test [2]created /Test+File+1.txt - 226 - 54 - 990 2010-04-08 20:12:16 192.168.241.1 - test [2]rnfr /Test+File+1.txt - 350 - - - 990 2010-04-08 20:12:16 192.168.241.1 - test [2]rnto /Test+File+2.txt - 250 - - - 990 2010-04-08 20:12:28 192.168.241.1 - test [2]rnfr /Test+File+2.txt - 350 - - - 990 2010-04-08 20:12:28 192.168.241.1 - test [2]rnto /Test+File+3.txt - 250 - - - 990 2010-04-08 20:12:31 192.168.241.1 - test [2]sent /Test+File+3.txt - 226 122 - - 990
The log can be read as described below: