Enabling and Configuring the Mobile Transfer Client in EFT
Perhaps the most important feature available to the MTC, aside from an always secure connection, is the centrally managed security controls that dictate what users can and cannot do within the MTC app when connected to EFT.
Server and Site administrators can also block MTC connections, effectively terminating the connection based on the user-agent string that identifies the client as an MTC client. (This does not prevent other file transfer clients—mobile or desktop—from connecting to EFT.)
MTC's security policy only applies to files in the remote directory. The security policy does not apply to files in the vault, which means that any file downloaded to the vault can be shared or opened in third-party applications. If the EFT administrator doesn't want users to share files or open them in third-party apps, then EFT should be configured to not allow users to save files to device's vault.
MTC is configured at the Site level for all Settings Templates and users.
To enable the MTC in EFT and configure security controls
-
In the administration interface, connect to EFT and click the Server tab.
-
On the Server tab, click the Site that you want to configure.
-
In the right pane, click the Connections tab.
-
If not already enabled, enable HTTPS and create and assign an SSL certificate for the Site.
-
Select the Allow Globalscape Mobile Transfer Client (MTC) over HTTPS check box.
-
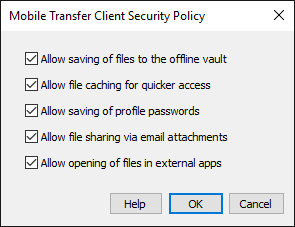
Click Configure. The Mobile Transfer Client Security Policy dialog box appears.
-
Each time a user connects or makes specific requests to MTC, their profile is updated with the latest security control settings. Select (enable) or clear (disable) the following check boxes:
-
Allow saving of files to the offline vault—The vault in the MTC app is an encrypted storage area* where a user can download a copy of a remote file (from this or possibly another EFT account) for subsequent access, even when offline, and even if the user no longer has an account on EFT. If you disable the ability to store files in the vault then you should alsoconsider disabling Allow file sharing via email attachments and Allow opening of file in external apps, since in all three instances files essentially leave your control.
-
Allow file caching for quicker access—The cache is an account (MTC profile)-specific secure storage area* that MTC uses to keep copies of files that were downloaded. The next time a user taps on a file (to open in the internal PDF viewer, for example), the file will be opened from the device's cache (assuming it isn’t stale data) rather than downloaded again from the server, resulting in a better end-user experience. The cache is semi-permanent in that it will grow as files are downloaded, and is not cleaned up unless space is needed or the user decides to clear the local cache (similar to how a browser's cache works). Disabling this option doesn’t disable file caching altogether, but rather makes caching temporary, cleaning up cached data upon application exit.
-
Allow saving of profile passwords—Preventing the user from saving the password forces them to re-type it each time they connect to EFT. Once authenticated, the app will retain the password in memory until the app is exited. If this setting is disabled in EFT, the password field appears dimmed in the MTC app (for this profile) and passwords for this profile are removed from the mobile keychain (iOS) or database (Android), if stored there. If this setting is enabled, then it is up to the user to decide whether to store the password in the MTC app.
-
Allow file sharing via email attachments—After downloading a file, an MTC user can optionally share the file as an email attachment with another user (taking the file outside of MTC's control). If this setting is disabled in EFT, then sharing won’t be allowed from within the MTC application. If you disable the ability to share files, then you should also consider disabling Allow opening of file in external apps and Allow saving of files to the offline vault, since in all three instances files essentially leave your control.
-
Allow opening of file in external apps—After downloading a file, an MTC user can optionally open the file in a third-party app, which is often necessary if there is no internal MTC viewer that can open the particular file extension.
When the user performs an "Open In" operation, the file is decrypted so that the external app can accept the file (which is now outside of MTC's control). This setting provides administrators the ability to block users from opening files in other apps, forcing them to use the in-app viewer (if available) or nothing at all. If you disable the ability to open files, then you should also consider disabling Allow file sharing via email attachments and Allow saving of files to the offline vault, since in all three instances files essentially leave your control. -
*Read the section on data encryption in the MTC FAQ. Files saved to disk on Android are not sandboxed, as in iOS, thus minimizing the effectiveness of some of the above controls. However, MTC does leverage Android’s “Internal Storage” for keeping it segmented and inaccessible to other apps, at the cost of much less available disk space than if the standard physical storage had been used, which is “world shareable” and thus unsuitable for storing corporate data, even if device encryption is enabled. (The third-party app cannot arbitrarily do so; the user must perform an "Open" operation from the other app and select the file located elsewhere in the data folder.)
-
-
Click Apply to save the changes on EFT.
To disable or block MTC
-
Clear the Allow Globalscape Mobile Transfer Client (MTC) over HTTPS check box or disable HTTPS.
Related Topics