Scan a File Using the File: Scan Action
The File: Scan Action is used to send a file to an antivirus or data loss prevention scanner for processing.
To scan a file using the File: Scan Action
-
Create a new Event Rule, such as a Folder Monitor Event.
-
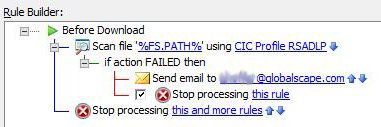
Add the Content Integrity Control Action. For example:
-
In the Action, click either of the underlined/linked items. The Content Integrity Control dialog box appears.
-
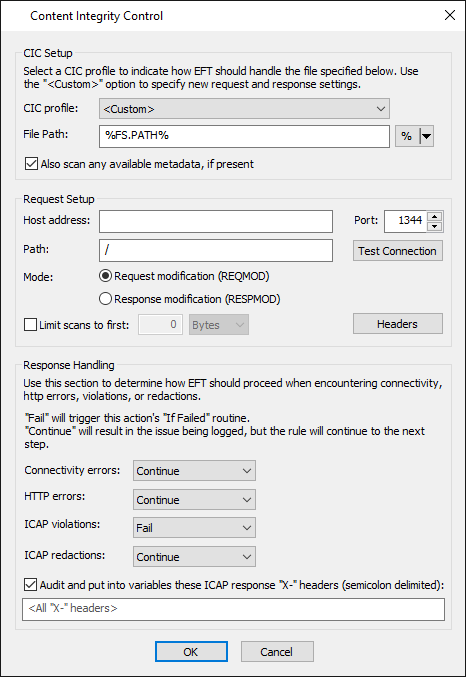
Click the CIC Profile drop-down list to select a predefined profile, or select <Custom>.
-
File Path - Physical location of the file to send to the ICAP server; %FS.PATH% is the default. You can specify another variable or drive and UNC paths. Wildcards are unsupported.
-
Also scan any available metadata, if present - Metadata includes the field name of Workspaces send operations. Consult your ICAP server for detailed information. The check box is selected by default.
-
The context variables Workspace Subject (%WORKSPACE.SUBJECT%) and Workspace Message (%WORKSPACE.MESSAGE%) (see above) relate to this feature.
-
If you specified a <Custom> profile, complete the rest of the fields in the dialog box:
-
Host address, Path, Port - These settings depend on settings in the antivirus or DLP (ICAP) server.
-
The Host address field should be the URL of the ICAP server (the field cannot be blank).
-
By default, the port is set to 1344.
-
Test Connection - After you specify the connection to the ICAP server, test the connection. If connection fails, verify these settings match the settings defined in the antivirus or DLP solution. (In earlier versions, Test Connection doesn't work with %variable% in the connection field.)
-
Mode - Specify one of the following:
-
Request modification (REQMOD) - - Request modification mode: Embeds file contents in an HTTP PUT request body, which is then sent in the body of an ICAP request to the server. The ICAP server may respond with a modified version of the embedded request, or a new HTTP response. The ICAP response will depend on your ICAP server’s implementation.
-
Response modification (RESPMOD) - Response modification mode: Embeds file contents in an HTTP 200 OK response body, which is then sent in the body of an ICAP request to the server. The ICAP server may respond with a modified version of the embedded response. The ICAP response will depend on your ICAP server’s implementation.
-
Limit scans to first n bytes - (Optional) Specify the number of bytes to scan. Some antivirus solutions only require a subset of a file's contents to test against their database of malware signatures. To keep from transferring large files in their entirety when we only need the first n bytes, you can specify how many bytes are sent to the ICAP server. When this check box is cleared, the entire file is transferred to the ICAP server. If the file is smaller than the Max scan size, the entire file will be transferred for scanning.
-
Headers - (Optional) In v8.0.5 and later, only set these values if needed for problematic ICAP connections. Headers can be used to override the REQMOD/RESPMOD X-headers sent by EFT, to fine-tune the connection to the ICAP server. These headers are displayed in the ICAP server logs.
-
HTTP host - The EFT site's local host address (do not use "localhost"); The default is to show the EFT HTTP Host if supplied (not localhost), otherwise "www.origin-server.com"; If you override the Host value, then that value is used instead. The order is: user override value -> EFT HTTP Host if supplied (not localhost) -> or www.origin-server.com as last resort.
-
X-Client-IP - Blank by default
-
X-Server-IP - Blank by default
-
X-Subscriber-ID - Blank by default
-
X-Authentication User - Provide a string with variables.
-
LDAP - Example: "LDAP://pdc/samaccountName=%LOGIN.LOGIN%,DC=s5development,DC=local"
-
AD - Examples: WinNT://{NetBIOSDomainName/sAMAccountName}, WinNT://pdc/s5dev\arybin
-
Other - Examples: Local://%USER.LOGIN%, Local://%SERVER.NODE_NAME%
-
X-Authenticated Groups - Blank by default
-
User can override and use context variables if desired as field elements. EFT will base-64 encode.
-
Under Response Handling:
-
Specify whether transfer should Continue or Fail when the following occur: Connection errors, HTTP errors, ICAP redactions.
-
Audit and put into variables these ICAP response "X-" headers - (Optional) Specify “X-“ headers for auditing using ARM. If this option is enabled and no “X-“ headers are specified, all “X-“ headers will be audited. Use semicolons between multiple items. Note this check box only affects whether the specified headers are audited by ARM, regardless of success or failure.
-
Click OK to save the changes in the Event Rule. The name of the profile appears in the Event Rule Action.
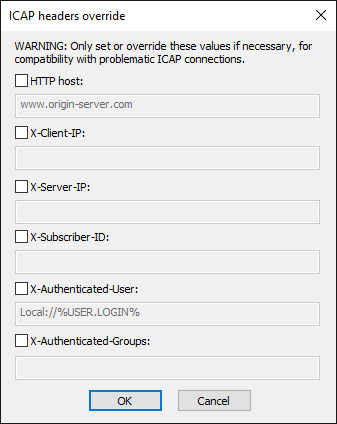
Note the difference between "ICAP Header" and "HTTP Header." The ICAP Header is a header with service information EFT sends to the ICAP server. The HTTP header is a part of information EFT sends to ICAP for analysis. That is, the HTTP header will be analyzed, not the ICAP header. The HTTP header is shown in ICAP log files.
Related Topics