Active Directory Configuration
On the Active Directory Settings page, you can configure Mail Express's Active Directory settings. When configured to use Active Directory, Outlook Add-In users and Internal users accessing the Drop-Off Portal or Internal Portal may log in using their existing Active Directory domain account credentials. When users initially log in, an internal user account will be created within the Mail Express Server that corresponds to the Active Directory account. This allows Mail Express administrators to customize the user account further as it pertains to the Mail Express system. To use the Single Sign On (SSO) capability of Mail Express, you must also configure AD authentication.
Mail Express logs all information regarding AD configuration changes made within the Administration Portal, including the administrator performing the modification, the time and date of modification, and the Active Directory settings after modification.
|

|
If a manually created Internal user account has a username that matches a username in the defined set of Active Directory user accounts, Mail Express will only authenticate against the manually created user account. It will not attempt to authenticate against the Active Directory account.
|
When authenticating an Active Directory-backed user with the Mail Express Server, the server will attempt to locate the following attributes on the user account:
-
mail - The email address for the user is used to populate the email address for the user within Mail Express. This field should exist since the LDAP-backed users inherently originate from the Outlook Add-In, and thus should have mail server accounts. This field is required.
-
displayName - The display name for the user is not required, but if present, it will be used to populate the user's display name within Mail Express.
If a user account lacking the "mail" attribute attempts to authenticate with the Mail Express Server, an ERROR level log message appears in the MailExpressServer.log similar to the following:
ERROR Failed to locate attribute "mail" for user "IdontHaveAnEmail"
To enable and configure Active Directory authentication
-
Launch the Mail Express Server administration interface. (e.g., click Start > Programs > Globalscape > Mail Express > Mail Express Admin or double-click the desktop shortcut).
-
Log in using the Mail Express Server administrator username and password that you specified during installation of the server.
-
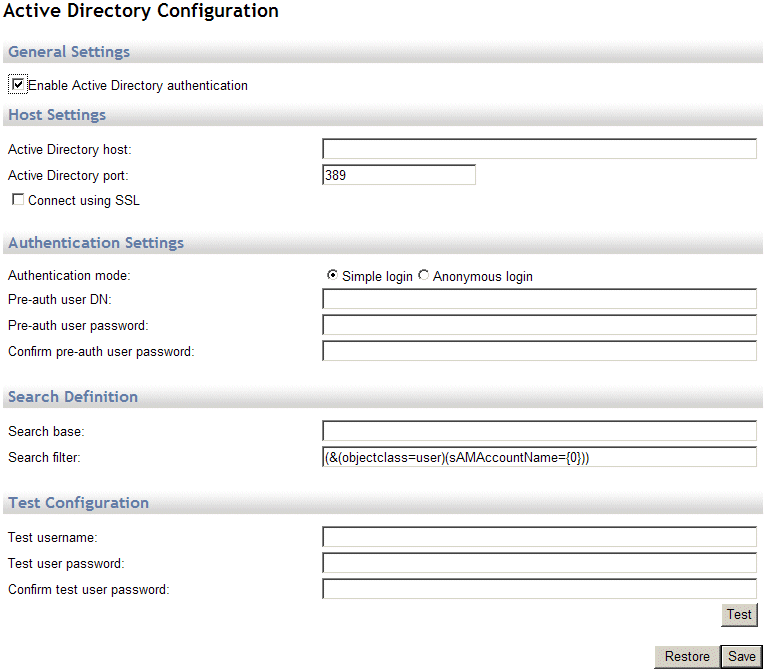
In the navigation pane, click Configuration > Active Directory. The Active Directory Configuration page appears.
-
Select the Enable Active Directory authentication check box (cleared by default). The page expands to display the AD options.
-
In the Active Directory host box, provide the host name or IP address (e.g., 10.1.1.1) of the Active Directory server.
-
In the Active Directory port box, provide the port on which Active Directory listens for LDAP communication. (The default port is 389; with SSL, the default is typically 636.)
|

|
If users from child domains need access to the Mail Express portals, use the domain name or domain IP address in the Active Directory host box and use the global catalog port (3268) in the Active Directory port box.
|
-
Select the Connect using SSL check box if you are using SSL for AD. When SSL is enabled, the Trusted Certificate Authority (CA) Certificate box appears.
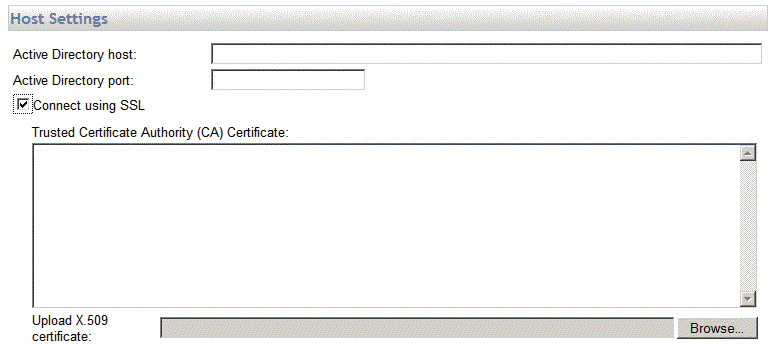
- In the Upload X.509 certificate box, browse to the location of the Base-64 encoded X.509 signed certificate that is to be used to validate the certificate chain. A certificate in this format must begin with "-----BEGIN CERTIFICATE-----" and end with "-----END CERTIFICATE-----".”
|

|
The Public Certificate that you must upload is the Public Certificate of the Certificate Authority that signs the Public Certificate for the Active Directory Server to which you are connecting. However, in most cases the Public Certificate for the Active Directory will be self-signed. In this case, you will just upload the Public Certificate of the AD Server.
|
-
In the Authentication mode area, specify Simple login or Anonymous. For Simple login, provide the Pre-Auth User DN and Password.
-
In the Pre-Auth User DN box, specify the user Distinguished Name for Simple login authentication. The following formats are supported:
-
-
Distinguished Name (e.g., CN=user,OU=users,DC=forests,DC=intranet,DC=example)
-
User Principal Name (UserName@DomainName, e.g., joeuser@forest.intranet.example)
-
Down-Level Logon Name (DOMAIN\UserName, e.g. ExampleDomain\joeuser)
-
In the Pre-Auth User Password and Confirm Pre-Auth User Password boxes, specify the password for Simple login authentication. (For information about preauthentication, refer to Preauthentication in Microsoft TechNet.)
-
In the Search base box, provide the base Active Directory container that Mail Express searches to find users that it will try to authenticate (e.g., CN=users,DC=forest,DC=intranet,DC=example). This is most often just the root AD name. Mail Express will search the full sub-tree starting at this top-level container (e.g., DC=DEMO,DC=VM).
-
In the Search filter box, provide the search filter that is used to find accounts under the search base. For example, with the following search filter:
(&(memberof=CN=MailExpressUsers,OU=Users,DC=DEMO,DC=VM)(objectclass=user)(sAMAccountName={0}))
AD users can only be found in the MailExpressUsers group (CN=MailExpressUsers) which resides in the Users (OU=Users) Container which is in the root active directory DEMO.VM. The {0} is the placeholder that will be populated with the username when performing the search. (Also refer to the section below, Searching Nested Groups with Mail Express.)
-
(Optional, but recommended) Provide the credentials for a known AD account in the Test username, Test user password, and Confirm test user password boxes, then click Test.
|

|
When testing Active Directory configuration via the Active Directory Configuration page, you should test using a user account that possesses a “mail” attribute. Otherwise, you will see an error in the MailExpressServer.log.
|
-
Click Save to save your changes on the server, or click Restore to cancel changes. If you navigate away from the page without clicking Save, your changes are discarded.
Searching Nested Groups with Mail Express
To query a single AD Group that contains nested groups and validate users that are part of the nested groups, add each of the groups that you want queried into a single LDAP filter.
For example:
-
User A is member of Group A
-
Group A is member of Group B
-
Therefore, User A is also a member of Group B
You cannot query Group B to find User A, so you must query Group A and Group B separately to find their users.
In this example, Group A and Group B are both located in the Users container under domain DEMO.VM, so the query construction would look like this:
GROUP A = CN=Group A,CN=Users,DC=DEMO,DC=VM
GROUP B = CN=Group B,CN=Users,DC=DEMO,DC=VM
You want to know if the user is part of Group A or Group B, so use the or (|) operator:
(|(memberOf=CN=Group A,CN=Users,DC=DEMO,DC=VM) (memberOf=CN=Group B,CN=Users,DC=DEMO,DC=VM))
And because you need to know what type of object you're trying to find, use the default settings:
(objectclass=user)(sAMAccountName={0})
Put it all together:
(&(|(memberOf=CN=Group A,CN=Users,DC=DEMO,DC=VM) (memberOf=CN=Group B,CN=Users,DC=DEMO,DC=VM)) (objectclass=user)(sAMAccountName={0}))
The leading & operator indicates that you want all these items to match up:
(&(Any of these Groups)(User objects only)(Account Name of {variable}))
![]()

