Audit Log
Intermapper records changes that people make to Intermapper's data model, which includes all of the information Intermapper stores about the monitored network. This information is written to the log files and can be viewed in one of the Log windows. The Audit Log is a predefined log that is included with Intermapper.
If someone edits a map by moving, adding, editing, or deleting an item, those activities are recorded in the audit log. Information, such as the date and time, who made the change, from which computer they connected, and what was changed, are recorded in this log.
Bulk changes initiated by people can generate many entries in the audit log, such as the following:
-
A user initiates an autodiscovery.
-
A user initiates a network scan.
-
A user imports data.
Other changes that are not initiated by a person, such as device or interface status changes or the sending of notifications are not written to the audit log because they are not initiated by a person. They are instead recorded in the Event Log.
To open the Audit log:
From the Logs submenu of the Window menu, select Audit.
Security
The Audit log cannot be edited, even by an administrator, without the change being detected.
Creation and Location of Audit Logs
Audit logs, along with other Intermapper logs, are stored in the InterMapper Settings/InterMapper Logs directory. The log filenames use the format of AuditYYYYMMDD.txt, where YYYY is the year, MM is the month, and DD is the day. New log files are created at midnight, or the first time the Intermapper server starts on a new day, so it can contain up to a day's worth of events.
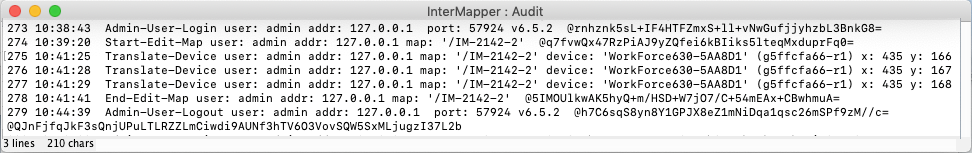
Sample Audit Log Entries
1 15:41:59 Starting Intermapper Audit Log File (6.5.2b2/Build 14C153/i386/Darwin/64-bit). @J0GfOVGUNFvZIkYxUJ5NZrPO8H4+Mg+Jsj+ENT2yh1I=
2 15:42:12 Admin-User-Login user: Admin addr: 127.0.0.1 port: 59629 v6.5.2 @5BFu6dgkl3bIy/stBiW+HTNDjpaveK5k6kvTSvPjpzw=
3 15:46:54 Start-Edit-Map user: Admin addr: 127.0.0.1 map: '/My Island' @BgmJ9yD+ip5NvfJxnkGZaVfyQSntRE/YtsM6WFohHlY=
4 15:47:20 Translate-Device user: Admin addr: 127.0.0.1 map: '/My Island' device: 'Tex-Ubuntu' (g5f3135c8-r9) x: 531 y: 97 @JJZVGPvchCHz7CILyonWXgi8Y704lgRPLCLBlvNHeSc=
5 15:47:30 End-Edit-Map user: Admin addr: 127.0.0.1 map: '/My Island' @mpdQbP8akL+BDvghiIxwsS9/Mx4dG76EAx84haUFols=@9vbwYcHvamfYZwwK17G3mjj1qWy/2GOqRGNPB2hLlGHpE94CPVk2oQyH68xSWgEU
Log Entry Structure
The Audit log entries use the following structure:
The first line of the Audit log does not follow the standard log pattern. Instead, it indicates the time when the audit log file is created, Intermapper's version number, build number, computer information, and operating system.
Subsequent lines follow a consistent pattern; the first 5 fields are always present. The fields are as follows:
line number
timestamp
event type
The fourth and subsequent fields start with a field name and colon. The fields are as follows:
name:
addr:
where name: is the username that triggered the event and addr: is the IP address of the computer the user is connected from.
The next one or more fields indicate which object is affected by the event. In many cases, the object is a map, indicated by the field name map: followed by the name of the map in single quotation marks (' ').
Commonly, the object is a device on a map. In this case, this includes 'map:', map name, device:, the nickname of the device, and the device ID in parentheses. For example, g5f3135c8-r9.
There might be other information beyond the object of the event, such as the x and y coordinates. This information is also in the form field_name: followed by the value.
All lines in the audit log end with a digital signature, which implements the security feature of the Audit log.
Events Recorded in the Audit Log
The following table shows the events that are recorded in the Audit log:
| Event | Associated Object | Other Information |
|---|---|---|
| Admin-User-Login | none | port: and Intermapper client version |
| User-Login | none | port: and Intermapper client version |
| Failed-Admin-Login | none | port: and Intermapper client version |
| Failed-User-Login | none | port: and Intermapper client version |
| Admin-User-Logout | none | port: and Intermapper client version |
| User-Logout | none | port: and Intermapper client version |
| Create-Notifier | name: | type: |
| Edit-Notifier | name: | type: |
| Delete-Notifier | name: | type: |
| Create-CSR | CSR: | |
| Upload-SSL-Cert | none | |
| Create-Map | map: | |
| Delete-Map | map: | |
| Import-Map | map: | filename: |
| Export-Map | map: | filename: |
| Import-Data-Directive | file: | directive: |
| Export-Data-Directive | file: | directive:, maps: |
| Edit-Retention-Policy | policy: | newValues: |
| Remove-Retention-Policy | policy(s): | |
| Set-Retention-Policy | map:, device: | variable:, policy: |
| Set-Retention-Policy | map:, interface: | variable:, policy: |
| Set-Probe-Data | map:, device: | probeName:, type: |
| Set-Community-String | map:, device: | |
| Set-Timeout | map:, device: | timeout: |
| Set-Poll-Interval | map:, device: | pollInterval: |
| Set-Ignore-Outages | map:, device: | ignoreOutages: |
| Set-Address | map:, device: | address: |
| Set-Device-Threshold | map:, device: | useMapDefaults:
maxAllowedLostPackets: criticalInterfaceErrs: alarmInterfaceErrs: warningInterfaceErrs: criticalPktLossThresh: alarmPktLossThresh: warningPktLossThresh: criticalRTTThresh: alarmRTTThresh: warningRTTThresh: |
| Set-Device-Threshold | map: | useServerDefaults: maxAllowedLostPackets: criticalInterfaceErrs: alarmInterfaceErrs: warningInterfaceErrs: criticalPktLossThresh: alarmPktLossThresh: warningPktLossThresh: criticalRTTThresh: alarmRTTThresh: warningRTTThresh: |
| Set-Device-Threshold | Server-Settings | maxAllowedLostPackets:
criticalInterfaceErrs: alarmInterfaceErrs: warningInterfaceErrs: criticalPktLossThresh: alarmPktLossThresh: warningPktLossThresh: criticalRTTThresh: alarmRTTThresh: warningRTTThresh: |
| Reset-Short-Term-Packet-Loss | map:, device: | |
| Set-Data-Retention-Policy | map:, device: | |
| Set-remoteaccess-ACLs | map: ACL-for-user: | |
| Set-webacccess-ACLs | map: ACL-for-user: | |
| Acknowledge-Device | map:, device: | |
| Acknowledge-Interface | map:, interface: | |
| Maintenance-Device | map:, device: | |
| Maintenance-Interface | map:, interface: | |
| Translate-Device | map:, device: | |
| Translate-Network | map:, network: | |
| Add-Edge | map:, device: | end: |
| Remove-Edge | edge: | |
| Add-Network | map:, network: | |
| Remove-Network | map:, network: | |
| Hide-Edge | map:, interface: | |
| Show-Edge | map:, interface: | |
| Add-Device | map:, device: | |
| Remove-Device | map:, device: | |
| Remove-Subnet | subnet: | |
| Change-Poll-Interval | map: | pollInterval: |
Securing Audit Logs
To secure the Audit log, encryption and mechanisms are used to prevent the following from occuring:
-
Removing or changing the last summary line.
-
Removing or changing the encrypted text (after @) on any line.
-
Removing or changing text lines before @.
-
Changing the timestamp or line number of a line.
-
Removing any lines or the first line.
-
Adding more lines after the original file.
-
Switching two lines (even when their timestamps are exactly the same).
-
Changing the numerical portion of the file name (other portions can be changed). For example, changing Audit202011240000.txt to Audit202011240000_A.txt is allowed. However, if you change the numerical portion to Audit202011250000.txt, the verification can fail.
Audit Log Verification Example
To verify an audit log file, you must first shutdown the Intermapper Sever, and then issue the following command:
Windows: Run as administrator
intermapper --verify-auditlog "C:\ProgramData\InterMapper\InterMapper Settings\InterMapper Logs\Audit202011250000.txt"
Linux: You need to be root or privileged user to run this command, use 'su' command. You also need to add the flag "--debug" in additional to --verify-auditlog:
intermapperd --debug --verify-auditlog "/var/local/InterMapper_Settings/InterMapper Logs/Audit202011250000.txt"
macOS: You need to be root or privileged user to run this command, use 'su' command.
intermapperd --verify-auditlog "/Library/Application Support/InterMapper/InterMapper Logs/Audit202011250000.txt"
Encryption/Decryption and Hash Algorithms
The following are used:
-
Encryption/decryption algorithm
AES-256 encryption with OpenSSL library using CBC mode ciphers with 256-bit key and 128-bit IV
-
MD5 Message-Digest Algorithm
Used to calculate log line hash and then encrypts the hash along with other parameters to form a line summary at the end of the line and a file summary at the end of the file.