Powertech Antivirus for IBM i Features
Powertech Antivirus for IBM i includes the following features.
Trellix's preeminent staff backs each new update of the virus-scanning engine and release of virus definition .DAT files. Their worldwide virus research team develops weekly updates for the virus definition .DAT files, leaving you confident that your IBM i server is well protected from attack. Powertech Antivirus for IBM i incorporates the latest generation of Trellix's scanning engine, in turn making Powertech Antivirus for IBM i a mature product backed by battle-tested technology, advanced heuristic analysis, and generic detection and cleaning.
- Scans within compressed files
- Decompresses and scans files compressed in packages such as PKZip, .LHA, and .ARJ
- Detects and cleans macro and script viruses
- Detects and cleans encrypted and polymorphic viruses
- Detects and cleans new viruses in executable files and OLE compound documents
- Detects and removes "Trojan horses", worms, and many other types of malicious software (malware)
- Upgrades easily to new scanning technology
- Includes technology to combat the latest and future threats
- Support for many more Packed Executable formats in which known malware is often re-packaged for obfuscation purposes
- Specific detection and reporting of files compressed or packaged with known suspicious applications
- Enhancements to enable scanning of non-standard ZIP archives
Powertech Antivirus for IBM i uses exit points to perform its job. See the IBM i Operating System Integration section. Starting in version 8.09, Powertech Antivirus for IBM i can share those exit points with other solutions.
IBM i Operating System Integration
Starting with V5R3, IBM integrated virus scanning support into the operating system. Powertech Antivirus for IBM i fully supports these features. The result is better security and substantially lower overhead when compared to other platforms and file systems. The following table lists some of the ways the operating system has integrated virus scanning:
|
NetServer (mapped drives) |
Files that are opened and modified from mapped drives are scanned for viruses. The operating system will not allow infected files to be opened, thus preventing a virus from spreading to other PC clients. |
|
open() |
The open() API is used by applications to open stream files in the IFS. IBM i can be configured to call Powertech Antivirus for IBM i to scan files before allowing them to be opened (on-access scanning). The operating system will not allow applications to open stream files that are infected with a virus. |
|
Save (SAV) command |
The SAV command is used to backup the files in the IFS. There are new parameters on the SAV command to specify if you want to scan files before saving to media, and if you want to save infected files (default is *NO). |
|
Restore (RST) command |
Files that are restored to the IFS (including vendor application files) will be marked as requiring a scan before they can be first used. |
|
Copy (CPY) command |
The CPY command is used to copy IFS files. The CPY command will not copy files that are infected with a virus. |
|
Check Object Integrity (CHGOBJITG) |
The CHKOBJITG command will report on any files in the IFS that have failed a scan. |
|
System audit journal (QAUDJRN) |
The system audit journal records virus scanning and cleaning activity. |
|
System values (QSCANFS and QSCANFSCTL) |
QSCANFS controls if virus scanning is enabled (default is ON). QSCANFSCTL provides options to tune scanning performance. |
|
File-level scanning attributes |
See following discussion |
About IBM i File Scanning Attributes
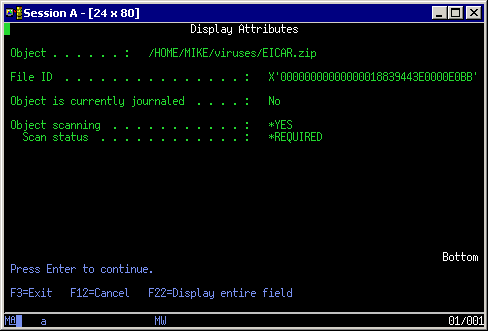
Figure 1 shows the attributes of a file that has never been scanned. This information can be seen using the Work with Object Links (WRKLNK) command and then option 8 next to a stream file.
Figure 1. This screen shows attributes of a file that has never been scanned.
Press page down several times to see the scan information. In this example the file is enabled for scanning and the file will be scanned before it is next opened (Scan status = *REQUIRED). All files in the Root, QOpenSys and User-defined file systems have these default values.
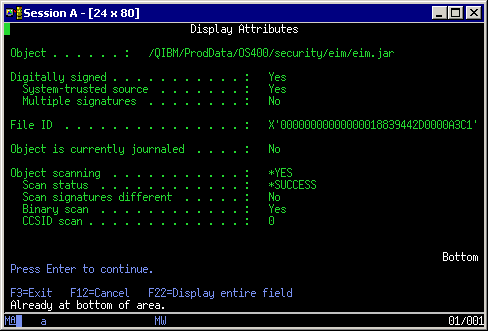
Figure 2 shows the attributes of a file that has been scanned with Powertech Antivirus for IBM i. This file is not infected (Scan status = *SUCCESS) and the file will not be scanned again unless it is changed or the virus definitions are updated (Scan signatures different = No).
Figure 2. This screen shows attributes of a file that has been scanned.
When you run on-access scanning, Powertech Antivirus for IBM i knows not to scan this file because nothing has changed that would allow this file to be infected. The result is on most days a full system scan can run in minutes instead of hours or days. Think of it as a "scan changed objects" command.
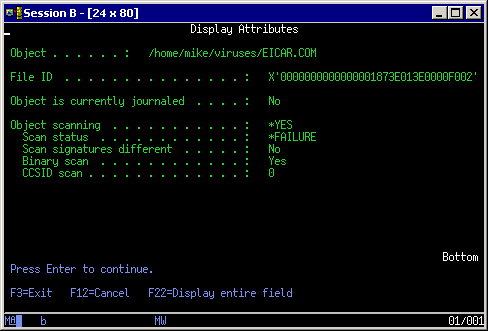
Figure 3 shows the attributes of a file after a virus has been detected. Powertech Antivirus for IBM i has updated the >Scan status= to *FAILURE. The operating system logs the error in the system audit journal and messages are generated. Finally, IBM i will not allow any application to open or copy a file that has failed a scan.
Figure 3. This screen shows attributes of a file after a virus has been detected.
Powertech Antivirus for IBM i provides real-time protection against virus threats by scanning files dynamically, as they are opened. You can separately enable on-access scanning for file server accesses (NetServer mapped drives, FTP) and 5250 environments (host-based applications, like Java, Websphere, etc).
The operating system uses the file scan information to avoid having to scan files that have not changed and have already been scanned (see discussion on the previous page). The result is the first user to open the file will wait for the scan, while subsequent accesses to that file (by that user or any other user) will not cause the file to be scanned again. Only when the file has changed, or when new virus definitions are updated, will the file be scanned again.
See On-Access Scanning.
Powertech Antivirus for IBM i provides on-demand scanning which allows you to scan all or part of the system at scheduled times. You can configure the directories to scan and the schedules at which to run the scan. This allows you to configure scanning to run during off-peak times to reduce the CPU impact on other applications. Once a file has been scanned using on-demand scanning, the file will not need to be scanned when accessed (no on-access overhead for that file) unless the file has changed or the virus definitions are updated. This allows you to use off-peak times to "pre-scan" files that rarely change, thus reducing the CPU overhead of on-access scanning and improved balancing of scanning workload.
See On-Demand Scanning.
Powertech Antivirus prevents ransomware attacks by detecting and alerting system administrators of potential ransomware threats, and can also be configured to automatically take action when a threat is detected.
See Anti-Ransomware.
Powertech Antivirus for IBM i can scan inbound and outbound email messages passing through the IBM i SMTP server. Powertech Antivirus for IBM i can perform virus scanning on emails before they reach your PC clients (or customers).
Powertech Antivirus for IBM i scans the IBM i Operating System (and user libraries) for objects that have been tampered with and have the potential to cause serious harm to the operating system or bypass all security entirely. For more information about object integrity scanning, see Object Integrity Scanning.
Powertech Antivirus for IBM i can scan files on Linux and AIX guest partitions using the Network File System (NFS). By creating scheduled scan tasks to scan NFS mountable volumes on guest partitions, you can reduce the time, effort and costs associated with installing and configuring multiple stand-alone antivirus applications on each partition. A single installation of Powertech Antivirus for IBM i on the host partition can be used to ensure all of your Linux and AIX partitions are free of viruses, trojans, worms, malware and spyware.
Powertech Antivirus for IBM i ensures you always have the latest protection against current virus threats by automatically downloading virus definition files from Trellix. By keeping the virus definition files up-to-date automatically, Powertech Antivirus for IBM i protects you from the new virus threats that occur each day. Automatic updating can be scheduled to run automatically, and CL commands are provided to integrate within your own nightly batch processes.
Built on Fortra's proven experience with IBM i administration, security, and automation, Powertech Antivirus for IBM i was designed from the ground up as a secure, automated antivirus solution that prevents headaches, not gives you new ones. Powertech Antivirus for IBM i provides automatic scheduling and updating of virus definitions, product enhancements, and scanning tasks that you create. By automating these tasks you can rest assured that Powertech Antivirus for IBM i is providing reliable, around-the-clock protection.
Powertech Antivirus for IBM i can retrieve virus definitions and program updates from either an HTTP server, an FTP server, or a shared local network path. The path can be located on another IBM i server or partition, a Windows file server, or any network path of your choice. This allows you to use one IBM i server or partition to download the virus definitions (from Trellix's HTTP server) and the remaining servers or partitions can retrieve their virus definition files from the shared network folder.
Powertech Antivirus for IBM i provides several logging features that you can use to monitor the application's activity:
- Messages are logged to the message queue AVMSGQ. You can view the message queue manually as needed, or use third-party monitoring tools to automate the monitoring of this queue and alert you to viruses and failed downloads via your email, cell phone, or pager.
- Scan reports provide detailed information about the directories scanned, infections found and cleaning/quarantining activity.
- All changes made to Powertech Antivirus for IBM i's automation files are recorded in the AVJRN journal, recording all changes made to the product, who made them and when they were altered.
- Virus scanning activity is recorded in the system audit journal, providing a secure audit trail of virus activity within the system.