Anti-Ransomware
Ransomware is malicious software (malware) that employs encryption to hold a victim’s information at ransom. In a ransomware attack, data is encrypted, which prevents access to it, and the attacker demands a ransom payment in return for decrypting the files.
Powertech Antivirus for IBM i includes anti-ransomware security functionality consisting of the following mechanisms:
-
detecting ransomware
-
blocking detected ransomware
-
notifying system administrators of both the detection and blocking
How Powertech Antivirus Prevents Ransomware Attacks
Powertech Antivirus prevents ransomware attacks by detecting and alerting for potential ransomware attacks, and can also be configured to automatically take action when an attack is detected.
The detection mechanisms are based on the IBM i file server exit point. Our detection only considers accesses performed through the file server. In most cases, this will be the IBM i's built in TCP file server, the IBM i NetServer. Detection through either mechanism results in mitigation and notification responses.
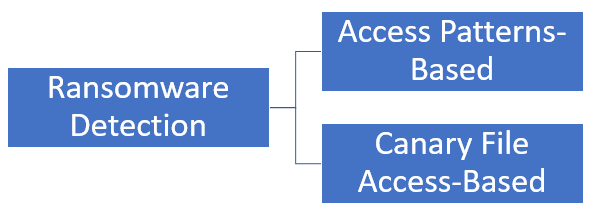
Powertech Antivirus helps protect against ransomware attacks in two ways:
-
The APEX (Access Pattern and Encryption Activity eXtended) detection method evaluates patterns in NetServer access to the Integrated File System (IFS). When APEX detects suspicious encryption activity, this suspicion level is compared to two thresholds:
a Message Threshold, which defines when a warning message is sent to the Powertech Antivirus message queue; and
a Block Threshold, which defines when the accessing user is blocked.
-
Canary files can be defined. A canary file is a decoy file placed within the IFS by the system administrator. If a defined canary file is modified, renamed, or deleted, it will immediately block the user.
Access Patterns-Based Detection (APEX)
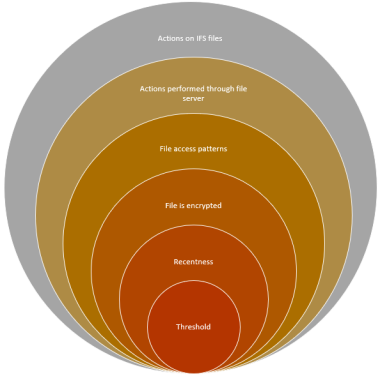
With this type of detection, Powertech Antivirus for IBM i looks for a combination of the following criteria:
Criterion 1: One of the following file access patterns happens that indicate files getting encrypted:
-
A file is read, then overwritten in place
-
A file is moved, then read, then overwritten, then moved back
-
A file is read, then a new file is created, then the old file is deleted or overwritten
Criterion 2: Encryption: The original, replaced file was not encrypted, but the file that replaces it is encrypted. We use a proprietary mechanism for determining a file's "encryptedness", which can identify encryption without being tied to any individual encryption algorithm.
Any event that matches these criteria adds an impact to a score. The maximum score is 100. The current impact on the score is:
| Number of Files Encrypted | Scoring Impact |
|---|---|
| 1 | -6 |
| 2 | 14 |
| 3 | 32 |
| 4 | 46 |
| 5 | 57 |
| 6 | 66 |
| 7 | 73 |
| 8 | 78 |
| 9 | 83 |
| 10 | 86 |
| 11 | 89 |
| 12 | 92 |
| 13 | 94 |
| 14 | 95 |
| 15 | 96 |
| 16 | 97 |
| 17 | 98 |
| 18 | 98 |
| 19 | 99 |
| 20+ | 100 |
Events have a lower scoring impact when they are not recent. In other words, Powertech Antivirus for IBM i only looks at the frequency of events inside a five minute time window.
The score is then compared to user-configurable action thresholds for sending a message and for blocking the user profile. The thresholds can be configured with the Configure APEX Thresholds (AVCFGTHR) command.
The following diagram depicts the criteria used by the access-patterns-based detection mechanism:
APEX Overrides
APEX overrides can be described as specific rules that influence the detection mechanisms. There are two types of APEX overrides, directory overrides and user overrides.
Directory Overrides
A directory override is used to instruct the APEX detection to ignore activity in specific IFS directories. For instance, on a customer's system, an automatic process may exist that automatically encrypts files in a specific directory when the files are deposited in that directory. The system administrator should then configure an override for that directory.
Directory overrides are always created manually. See AVCFGDIR Configure Directory Exclusions for more information on directory override parameters.
User Overrides
A user override is used to instruct the APEX detection to ignore activity performed by a specific user profile. For instance, an automatic process may exist that automatically encrypts files in different directories through the file server, and does so with a dedicated user profile. The system administrator should then configure an override for that user profile. See also the Implementation Recommendations section.
User overrides can be created manually or by the mitigation.
When the mitigation blocks a user profile, it does so by adding a user override for the offending user profile. In that scenario, the "Block user on threshold" parameter of the user override is set to *YES. See Configure User Overrides (AVCFGUSR) for parameter information.
Canary File Access Detection
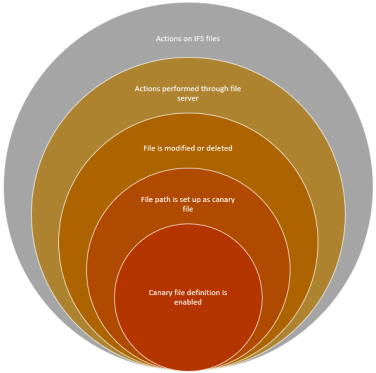
A canary file is a file that should not be modified during normal operations. Modifications or deletion of such a file can indicate ransomware activity. The term canary comes from the use of canaries in coal mines, where they were used as an early indicator of danger.
From the perspective of the anti-ransomware functionality, a canary file is a user-configured file path.
Detection will only be triggered if the access to a canary file either modifies the file or deletes it. Read-only accesses will not cause the detection to kick in. Otherwise, detection could, for instance, be triggered when a Windows PC's search indexer indexes files on a shared IFS directory.
Some ransomware programs search the victim's files for sensitive information by scanning for key terms in the files' name and contents. Such key terms could for instance be "confidential", "strategic" or "security".
The following diagram depicts the criteria used by the canary file access-based detection mechanism:
Response to Detected Ransomware Activity
Responses to detection can be either mitigation, notification, or both.
Detection from the access patterns-based detection mechanism will lead to mitigation, notification, or both.
Detection from the canary file-based detection mechanism will lead to mitigation and notification. There is no notification-only response.
Mitigation
Mitigation consists of the anti-ransomware functionality blocking file server access for the user profile who performed the detected activity.
This blocking is only registered within the Powertech Antivirus for IBM i configuration and uses the file server exit point to implement the blocking.
When mitigation is performed, a new user override is added for the offending user profile. This override has the attribute "Currently blocked" set to *YES. If an override previously existed for this user profile, its "Currently blocked" attribute is changed to *YES.
To unblock the user profile, delete the override, or set its "User is currently blocked" parameter to *NO.
Notification
Messages placed on the STANDGUARD/AVMSGF message queue can be:
-
Viewed interactively by users through the IBM i Display Message command
-
Processed through IBM i message management solutions, for forwarding via email, or to start an automation process
-
Forwarded to SIEMs by using Powertech SIEM Agent for IBM i
See Message Queue Interface for more information.
Anti-ransomware Interfaces
There are four interfaces to the Anti-ransomware functionality:
-
A green-screen menu-based user interface
-
A command-line interface, and
-
An IBM i message queue used for notification
-
The Powertech Antivirus Server Anti-Ransomware user interface
Menu-Based User Interface
The main configuration user interface for the Anti-ransomware functionality is implemented in a new entry (option 10 = Anti-Ransomware Menu) on the Powertech Antivirus for IBM i Setup Menu.
Command Based Interface
The new functionality is available through CL commands. The command objects all reside in the product library (STANDGUARD).
Message Queue Interface
The product message queue STANDGUARD/AVMSGQ can be considered a basic notification and integration interface.
Notification consists of messages being created in the IBM i message queue STANDGUARD/AVMSGQ on the same system. The message descriptions are:
-
AVE3001 (suspicious behavior detected)
-
AVE3002 (user blocked because of suspicious behavior)
Messages that arrive on the product message queue can be:
-
Viewed interactively by users through the IBM i Display Message command.
-
Processed through Fortra's IBM i message management solutions (Robot Alert/Console/Network, Halcyon), for forwarding via email, or to start an automation process (Robot Schedule, Robot Schedule Enterprise).
-
Forwarded to SIEMs by using Powertech SIEM Agent for IBM i.
Powertech Antivirus Server Anti-Ransomware User Interface
Anti-Ransomware can be configured through Powertech Antivirus Server. See Anti-Ransomware Configurations for more information.
Anti-Ransomware Implementation Recommendations
To ensure that legitimate activity does not accidentally cause file server activity to be blocked, implementation should always be performed in two phases:
-
Observation phase
-
Enforcement phase
The observation phase could last between one week and a few weeks.
After the observe-only phase, you enable blocking, and then enter the enforcement phase.
Observation Phase
-
Double-check that no other exit program is associated with the file server exit point (any format). The file server exit point is named QIBM_QPWFS_FILE_SERV. This can be checked in Work with Registration Information (WRKREGINF). If another exit program is used on that exit point, it will need to be removed first.
-
Estimate the total system CPU load using either the Work with System Activity (WRKSYSACT) or Work with System Status (WRKSYSSTS) commands. Estimate how much of that CPU load is from NetServer by observing CPU load in subsystem QSERVER using the command: WRKACTJOB SBS(QSERVER).
-
Use the Configure APEX Thresholds (AVCFGTHR) menu option to ensure that the Block action threshold is set to *NEVER and the Send Message action threshold is set to a low value between 20 and 40.
-
If you are aware of an application that encrypts or compresses files through the file server interface, define suitable exclusions in the user overrides and/or directory overrides. Don't worry about missing an application at this point as during the Discovery phase, the anti-ransomware functionality will not block any file server activity.
-
Wait until the NetServer can be safely restarted.
-
Use the Activate/Decativate Anti-Ransomware (AVACTAR) menu option with option *ADD to add the anti-ransomware exit programs, and restart NetServer. This enables the anti-ransomware functionality in notify-only mode.
-
During the Observation Phase, check if any file server activity is detected as ransomware activity. If the answer is yes, the system administrator will need to investigate whether actual ransomware activity occurred.
-
Design and testing of the anti-ransomware functionality were specifically intended to minimize false positives, that is, mis-classification of legitimate activity as ransomware activity. However, there is always a small residual risk of mis-classification. Activity that risks being misclassified is activity that matches the above detection criteria for either detection mechanism.
-
The function of the Observation Phase is to determine whether any false positives are raised. If this happens, and legitimate activity was mis-classified as ransomware activity, set up a corresponding user override and/or directory override to exclude that activity from detection.
Enforcement Phase
In this phase, you enable the anti-ransomware functionality to not just notify you when ransomware activity occurs, but to mitigate the ransomware activity by blocking it.
To do so, use the Configure APEX Thresholds (AVCFGTHR) menu option and change the 'Block User on Threshold' parameter value to a value other than *NEVER, for example, to 30. This enables the Anti-ransomware functionality to block a user profile.
System Administrators can unblock a user profile using the Work with User Overrides menu item.
Using Anti-Ransomware
Use the following steps to activate and configure Anti-ransomware.
Activating/De-Activating Anti-Ransomware Protection
-
From the Powertech Antivirus Main Menu, choose option 50, Setup Menu, then option 10, Anti-Ransomware Settings. The Powertech Anti-Ransomware Menu appears.
-
To activate and deactivate Anti-ransomware protection, choose option 50, Activate/Deactivate Anti-Ransomware. The Activate/Deactivate Anti-Ransomware (AVACTAR) panel appears. Note that it will not be activated/deactivated until the QSERVER subsystem is restarted.
Configuring Anti-Ransomware
-
From the Powertech Antivirus Main Menu, choose option 50, Setup Menu, then option 10, Anti-Ransomware Settings. The Powertech Anti-Ransomware Menu appears.
-
Choose option 1 to open the Configure APEX Thresholds (AVCFGTHR) panel.
-
For Send Message on Threshold, specify the threshold value to be used to determine when a message will be sent, warning of a possible ransomware attack. The message is sent to message queue AVMSGQ.
-
For Block User on Threshold, specify the threshold value to be used to determine when a user will be blocked, in response to a possible ransomware attack. A message is sent to message queue AVMSGQ and the user is blocked within User Overrides.
-
-
Press F3 to return to the Anti-Ransomware menu and choose option 2, Work with APEX Directory Exclusions. The Work with Directory Exclusions (AVWRKDIR) panel appears.
-
Define the directories that will not be protected by Powertech Antivirus for IBM i Anti-Ransomware.
-
Note that an override does not apply to sub-directories; it only applies to the directory specified.
-
-
Press F3 to return to the Anti-Ransomware menu and choose option 3, Work with APEX User Overrides. The Work with User Overrides (AVWRKUSR) panel appears.
Use this option to manage users in relation to anti-ransomware protection. You can define a different message and block thresholds for specific users and also define if a user is currently blocked. When a user is automatically blocked by the anti-ransomware protection, the user will have an entry within User Overrides.
-
Press F3 to return to the Anti-Ransomware menu and choose option 10, Work with Canary Files. The Work with Canary Files panel appears.
Use this option to define decoy files you have created within the Integrated File System (IFS), which should result in the immediate blocking of a user if modified, renamed, or deleted. This will be actioned, if active, even if the canary file is within a directory that has a Directory Override, excluding it from Anti-ransomware protection.
Anti-Ransomware Performance Impact
CPU Overhead
CPU overhead from the anti-ransomware functionality was found in internal testing to increase CPU load for file server processing by a factor of about 1.15.
So, for example, if your file server processing normally consumes 10% of the available CPU, the overall CPU consumption will increase, but only to between 11 and 12%.
Anti-Ransomware Forces Single-Threaded Mode for NetServer
NetServer, by default, runs in multi-threaded mode. In environments with a high number of NetServer sessions, where hundreds or thousands of sessions can be active at any given point in time and a high number of file accesses are performed, multi-threading provides a performance advantage over single-threaded mode, by allowing parallel execution.
When the Powertech Antivirus anti-ransomware functionality is activated, NetServer connections will not be able to use multi-threading. In most environments, the impact from this change is negligible. However, in high-usage environments like those described above, enabling anti-ransomware can potentially reduce NetServer performance. Symptoms are users complaining about file actions failing that they try to perform through Windows Explorer / Windows File Explorer.
Note that some file system accesses that are performed through NetServer, such as:
-
access to the QDLS file system,
-
access to the QFileSvr.400 file system, and
-
access to save files in the QSYS.LIB file system
also cannot use multi-threading, regardless of whether the Anti-ransomware functionality is enabled or not.
Recommendations
If your system has high-volume NetServer activity, or if you are not sure whether your environment falls into that category, you should first activate the Anti-ransomware functionality on a test system. Once testing has been completed there, and has shown no or negligible impact, enable the Anti-ransomware functionality on your production system in a controlled manner, to assess the impact on NetServer performance.