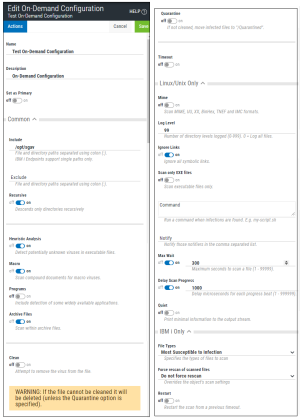
New/Edit/Duplicate On-Demand Configuration pane
How to get there
- To create a new Configuration, on the Configurations page, choose Add > On-Demand Configuration.
- To create a new Configuration starting with the settings of an existing Configuration, on the Configurations page, for an existing On-Demand Configuration, click
 > Properties.
> Properties. - To edit an existing Configuration, on the Configurations page, for an existing On-Demand Configuration, click
 > Properties.
> Properties.
What it does
The New/Edit/Duplicate On-Demand Configuration pane allows you to set configuration options, including notification settings, for on-demand scanning.
Options
Click Actions to open a submenu with the following connection management options:
- Duplicate. Choose this option to duplicate the configuration.
- Delete. Opens the Delete Configuration dialog box, where you are prompted to specify a new Configuration for endpoints assigned to the Configuration you are deleting.
- Close. Choose this option to close the submenu.
Name • Description
The name and description of the configuration.
Set as Primary
Endpoints set to the Primary Configuration (see Endpoint Properties pane) inherit the settings of the Configuration that is set as Primary. Toggle this switch to On to indicate that you would like to set endpoints currently assigned to the Primary Configuration to the Configuration you are editing. When you click Save, the number of endpoints that will change is indicated and you are prompted to confirm. Toggle this switch to Off to indicate that you would like to set endpoints assigned to the Primary Configuration to the Default Configuration. The Configuration that is currently set to Primary is indicated in the Configurations page.
Common
Include
A required colon-delimited list of path names to be included for on-demand scanning. A file that exists within any of the path names specified will be subject to scanning unless the file path name is specified as an Exclude Path. IBM i Endpoints support single paths only.
Exclude
A colon-delimited list of path names to be excluded from on-demand scanning. The exclude paths take precedence over include paths. A file that exists within any of these path names will not be subject to scanning.
Recursive
If set to On, the scan descends the specified directories recursively. If set to Off, the current directory is scanned without descending subdirectories.
Heuristic Analysis
Include heuristic analysis to find new viruses. If set to On, Powertech Antivirus employs heuristic technology to detect potentially unknown viruses in executable files (programs). If set to Off, the engine can only find viruses that are already known and identified in the current virus definition files.
Macro
If set to On, Powertech Antivirus treats embedded macros that have code resembling a virus as if they are viruses. This parameter is similar to Heuristic analysis but scans for new viruses in compound document formats; for example, Microsoft OLE formats such as Word documents. If set to Off, embedded macros that have code resembling a virus are not treated as viruses.
Programs
If set to On, Powertech Antivirus detects some widely available applications, such as password crackers or remote access utilities that can be used maliciously or pose a security threat. If set to Off, these applications are not detected.
Archive Files
If set to On, Powertech Antivirus includes archive files. Archive files contain embedded files and usually end with one of the following extensions: .ZIP, .TAR, .CAB, .LZH, .JAR and .UUE. This option will also permit scanning of MSCompress files. If set to Off, archive file types are not scanned.
Clean
If set to On, Powertech Antivirus cleans infected files by repairing the infection. Please note most infections cannot be cleaned.
Quarantine
If set to On, Powertech Antivirus quarantines the infected files by moving them to the /Quarantined directory. When Quarantine and Clean are both On, Powertech Antivirus attempts to clean the file first, and if unsuccessful, moves the file to the quarantine directory. If they are both off, no actions are taken on infected files.
Timeout
Specifies the maximum number of seconds the scan will execute in total. After the number of seconds has elapsed, the command will end without scanning any remaining files. The return code will indicate a timeout has occurred. For IBM i endpoints, the seconds you enter are converted to minutes.
Linux/Unix Only
Mime
If set to On, Powertech Antivirus scans inside MIME-encoded files, UU-encoded files, XX-encoded files, and BinHex files. If set to Off, Powertech Antivirus does not scan inside these types of files. This parameter reduces scanning performance.
Log Level
Specifies the number of directory levels that will be printed in the output listing. The default is 99.
Ignore Links
If set to On, the scan ignores all symbolic links. If set to Off, symbolic links are scanned.
Scan Only EXE Files
If set to On, Powertech Antivirus scans executable files only. The scan engine uses the file extension alone to determine whether the file is an executable. If set to Off, Powertech Antivirus scans all files regardless of the file extension.
Command
Runs the specified command string when infections are found, passing the file name as a parameter. This allows a user-written script to perform actions such as alerting an administrator. Please note this file will be a live infected file and in no way should the script attempt to read it. The intention is to allow you to process the file name. You may want to implement a procedure to notify an administrator, for example. Scripts must have execute permissions in order to be run.
Notify
Notify those notifiers in the comma separated list, which are defined in the [notify] section of config.ini. This list will override the list defined by the config.ini avscan:notify parameter. See Notification Support in avconfig command.
Max Wait
Specifies the maximum number of seconds to spend scanning any one file. After the number of seconds has elapsed the product assumes the file is OK and proceeds with the next file. The default is 300. Use this option cautiously.
Delay Scan Progress
The amount of time in microseconds the scanner should pause with each progress beat from a scanning operation. This can be used as a simple CPU limiting technique. It can be an integer value between 0 and 999999. The default value of 0 disables the feature.
Quiet
Prints minimal information to the output stream, useful for parsing the output file.
IBM i Only
File Types
Specifies the types of files to scan. The options are:
-
Most Susceptible to Infection
-
All files
-
Examine Files for Known Macro Viruses
Force rescan of scanned files
Specifies if the objects scan settings should be overridden. The options are:
-
Do not force rescan
-
Rescan all files
-
If file's "Object scanning" attribute is *NO
-
If file's "Object scanning" attribute is *CHGONLY
Restart
If set to On, the system will restart the scan from a previous timeout. If set to Off, the system will not restart the scan.