Change Field Authorization Lists (CHGFLDAUTL)
The Change Field Authorization Lists (CHGFLDAUTL) command allows authorized users to change the Authorization List settings for a field in the Field Encryption Registry.
The following users can use this command:
- QSECOFR user profile (unless excluded in the Key Officer settings)
- A user profile with *SECADM authority (unless excluded in the Key Officer settings)
- A Key Officer who has a *YES specified for the "Maintain Field Enc. Registry" authority setting
This command requires the user to have *CHANGE authority to the CRVL002 Validation List (*VLDL) object which contains the Field Encryption Registry.
NOTE: The CHGFLDAUTL command only changes the field entry settings in the registry. It will not cause any action to be performed on the actual database field in the file.
How to Get There
From the Field Encryption Menu, choose option 5. Or, prompt (F4) the command CRYPTO/CHGFLDAUTL.
Options
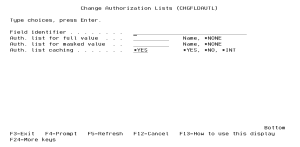
Field identifier (FLDID)
Indicate the Field identifier to change the Authorization Lists for.
Auth. list for full value (AUTLDEC)
Indicate the Authorization List that should be used by the field decryption APIs for checking the user's permissions to the full decrypted values for the field.
The possible values are:
*NONE No Authorization List is used by the field decryption APIs to check the user's permissions. However, the user will still need at least *USE authority to the Key Store which holds the Decryption Key.
authorization-list-name Indicate the name of the Authorization List. An Authorization List can be created with the IBM i command CRTAUTL. The users (or user groups) which need access to the decrypted values will need at least (*USE) authority to the Authorization List. Additionally, the users (or user groups) which need access to the decrypted values are required to have at least *USE authority to the Key Store object which holds the Decryption Key.
Auth. list for masked value (AUTLMASK)
Indicate the Authorization List that should be used by the field decryption APIs for checking the user's permissions to the masked values for the field.
The possible values are:
*NONE No authorization list is used by the field decryption APIs to check the user's permissions. However, the user will still need at least *USE authority to the Key Store which holds the Decryption Key.
authorization-list-name Indicate the name of the Authorization List. An Authorization List can be created with the IBM i command CRTAUTL. The users (or user groups) which need access to the masked values will need at least (*USE) authority to the Authorization List. Additionally, the users (or user groups) which need access to the masked values are required to have at least *USE authority to the Key Store object which holds the Decryption Key.
Auth. list caching (AUTLCACHE)
Indicate if the permissions for authorization lists are 'cached' in memory.
The possible values are:
*YES Caching will occur. When a field decrypt operation is performed, the permissions for the authorization lists will be saved (in memory) and used in future authority checks [for decrypt operations] within the job. This caching option provides the best performance.
NOTE: In order to recognize any permission changes to the authorization lists, the jobs [that are performing decrypt operations] will need to be restarted.
*NO Caching will not occur. The permissions to the authorization lists will be checked each time a decrypt operation is performed. This option is useful when you want changes to the authorization lists to be immediately recognized by jobs that are performing decrypt operations, or if you want to take advantage of program adopted authority when determining permissions to an authorization list.