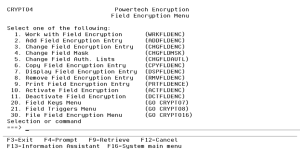
Field Encryption Menu
Field values can be encrypted and decrypted using a variety of methods in Powertech Encryption for IBM i, providing a great deal of flexibility for an organization. For each database field, you can choose the technique to utilize based on your application requirements.
The preferred option for field encryption is to use Powertech Encryption for IBM i’s innovative Field Encryption Registry, which allows an organization to indicate (register) the database fields to encrypt. When a field is “activated” in the Registry, Powertech Encryption for IBM i will perform a mass encryption of the current values for that field. Powertech Encryption for IBM i can then automatically encrypt the field values on an ongoing basis as new database records are added and when existing field values are changed.
The automated encryption function in Powertech Encryption for IBM i’s Field Encryption Registry will eliminate the need to make changes to your application programs for data encryption. If DB2 Field Procedures (available in IBM i V7R1) are utilized, the values can also be automatically decrypted without program changes. Otherwise, simple program changes can be made to decrypt values using Powertech Encryption for IBM i’s APIs.
You can optionally modify your applications to encrypt data through program (API) calls to Powertech Encryption for IBM i’s encryption procedures and programs. Powertech Encryption for IBM i also includes stored procedures and SQL functions, which can be called from within native applications or other external clients (i.e. graphical or web-based front ends) for encryption/decryption.
Encryption Basics
Encrypted data (Cipher Text) is in alphanumeric format. Since the encryption algorithms use the full character set, you will see encrypted data as a combination of letters, special characters and numbers.
Before: The quick brown fox jumped over the lazy dog
After: „Œ \ËKä°BBY ý\åê·Ñ‚C‹Ÿ^{F+rAÀJ[13]~()$j1Ï(¾Y½i›”®t
Encryption Algorithms
Powertech Encryption for IBM i implements the AES and TDES encryption algorithms (ciphers). Both of these algorithms follow standard (non-proprietary) specifications as published by the United States National Institute of Standards and Technology (NIST).
The TDES (Triple DES) standard was introduced in 1998. It is so named because it applies the Data Encryption Standard (DES) cipher algorithm three times to each data block. TDES is slowly disappearing from use because of performance issues and weaker key sizes.
The AES (Advanced Encryption Standard) standard was introduced in 2001. AES is the first publicly accessible and open cipher approved by the US Government for top secret information. AES offers high performance and provides strong key lengths up to 256 bits. AES is a very popular cipher for field encryption because of those attributes.
Encryption Modes
The AES and TDES standards offer different operating “modes” that you can choose from. Powertech Encryption for IBM i provides support for the CUSP, ECB and CBC modes.
CUSP Mode (Cryptographic Unit Support Program)
CUSP mode is supported in the AES algorithm. This is a stream-based mode, which means that the length of the encrypted data will equal the length of the input data. This mode is useful if the field data is not divisible by a block length and if you want to store the encrypted values in your existing field (if not using a DB2 Field Procedure).
With CUSP mode, you can optionally specify an Initialization Vector (IV). An Initialization Vector (IV) is an arbitrary value that you can enter, which will be used as an additional input to the encryption algorithm. Therefore, the encrypted output is dependent on the combination of the Initialization Vector, Encryption Key and the Plain Text (the data you want to encrypt).
ECB Mode (Electronic Code Book)
ECB mode is supported in both AES and TDES algorithms. This is a block-based * mode.
With ECB mode, you cannot specify an Initialization Vector.
CBC Mode (Cipher Block Chaining)
CBC mode is supported in both AES and TDES algorithms. This is a block-based * mode.
With CBC mode, you can optionally specify an Initialization Vector (IV) to use as an additional input to the encryption algorithm.
*Notes on Block-based Modes
When using the AES algorithm with CBC or ECB modes, the length of the encrypted data will be a minimum of 16 bytes long. Its “block-based” length will be divisible by 16 or 24. For instance:
| Original Field Length | Encrypted Length |
|---|---|
| 10 bytes | 16 bytes |
| 16 bytes | 16 bytes |
| 17 bytes | 24 bytes |
| 24 bytes | 24 bytes |
| 31 bytes | 32 bytes |
When using the TDES algorithm with CBC or ECB modes, the length of the encrypted data will be a minimum of 8 bytes long. Its “block-based” length will be divisible by 8. For instance:
| Original Field Length | Encrypted Length |
|---|---|
| 5 bytes | 8 bytes |
| 8 bytes | 8 bytes |
| 9 bytes | 16 bytes |
| 16 bytes | 16 bytes |
How to Get There
From the Main Menu, choose option 4, Field Encryption Menu. Or, submit the command GO CRYPTO/CRYPTO4.
Options
1. Work with Field Encryption (WRKFLDENC)
Choose this option to open the Work with Field Encryption Registry (WRKFLDENC) panel, which allows you to specify (register) the database fields that require encryption.
2. Add Field Encryption Entry (ADDFLDENC)
Choose this option to open the Add Field Encryption Entry (ADDFLDENC) panel, which allows authorized users to add a new entry into the Field Encryption Registry.
3. Change Field Encryption Entry (CHGFLDENC)
Choose this option to open the Change Field Encryption Entry (CHGFLDENC) panel, which allows authorized users to change an entry in the Field Encryption Registry.
4. Change Field Mask (CHGFLDMSK)
Displays the Change Field Mask (CHGFLDMSK) panel, where you can change the field mask using the CHGFLDMSK command.
5. Change Field Auth. Lists (CHGFLDAUTL)
Displays the Change Authorization Lists (CHGFLDAUTL) panel, where you can change the field Authority lists using the CHGFLDAUTL command.
6. Copy Field Encryption Entry (CPYFLDENC)
Displays the Copy Field Encryption Entry (CPYFLDENC) panel, where you can copy the field entry using the CPYFLDENC command.
7. Display Field Encryption Entry (DSPFLDENC)
Displays the Display Field Encryption Entry (DSPFLDENC) panel, which shows the values for the field entry using the DSPFLDENC command.
8. Remove Field Encryption Entry (RMVFLDENC)
Displays a prompt to confirm the removal of the field entry using the RMVFLDENC command.
9. Print Field Encryption Entry (PRTFLDENCE)
Displays a prompt to print field encryption entries using the PRTFLDENCE command.
10. Activate Field Encryption (ACTFLDENC)
Displays a prompt to activate the field entry for encryption using the ACTFLDENC command.
11. Deactivate Field Encryption (DCTFLDENC)
Displays a prompt to deactivate the field entry from encryption using the DCTFLDENC command.
20. Field Keys Menu (GO CRYPTO/CRYPTO7)
Choose this option to open the Field Keys Menu.
21. Field Triggers Menu (GO CRYPTO/CRYPTO8)
Choose this option to open the Field Triggers Menu, which allows you to Remove or Add Field Triggers.
30. File Field Encryption Menu (GO CRYPTO/CRYPTO16)
Choose this option to open the File Field Encryption Menu, where you can work with file fields.