Configuring Authentication for the QSECOFR Profile
Use the following instructions to configure multi-factor authentication for the QSECOFR profile.
After completing the following procedure, the QSECOFR profile will be locked out of the system if, for any reason, the RSA SecurID Agent libraries do not exist on the system. Access to the system could also be prohibited if the program object that is used as an initial program is damaged.
IBM i Configuration
There are two possible methods that can be used to configure the IBM i, the initial program method or the subsystem routing program method.
Initial program method
-
Check for restricted state.
If the IBM i is in restricted state, it is most likely that communication with the RSA Authentication Manager is not possible. Therefore, the authentication should not be attempted (steps 3 and 4). The program logic can finish (step 5).
-
Check whether the process can reach the RSA Authentication Manager.
If the RSA Authentication Manager cannot be reached, the authentication would not be successful, therefore, the authentication should not be attempted (steps 3 and 4). The program logic can finish (step 5).
-
Run the following command:
@ACE/ATHPRF OBJ(*DSA)
-
Check the return message id and perform required action:
MLT1733 – TCP/IP address required when using remote authentication
MLT1734 – Authentication failed
MLT1735 – Authentication program for &1 not found in library list - End the program.
Subsystem routing program method
As an alternative, a safer solution would be to consider using a Subsystem Routing Program. Such a solution does not require changing the User Profile. Unfortunately, using a Routing Program would require changes to the existing subsystems that are used for interactive sign on activity. In other words, it involves more than simply installing and configuring software. To use a Routing Program requires changes to at least one subsystem that has not been supplied/created by Fortra. Any routing program that is used and/or changed to process SecurID authentication would need to use logic similar to that above.
For the Routing Program, the logic could be “guarded” with a condition so that the logic is only performed when QSECOFR is attempting sign on.
As a caveat, some regulations that require administration profiles to be authenticated with multi-factor authentication, for example, PCI, do not require authentication at the physical console. Therefore, a customized subsystem routing program may not be required to be configured within the subsystem that allows access via the physical console. Of course, the final decision rests with you, the client.
RSA Authentication Manager Configuration
Use the following instructions to activate authentication for the QSECOFR profile.
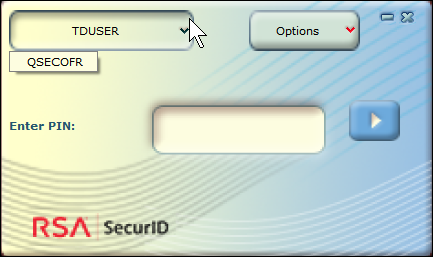
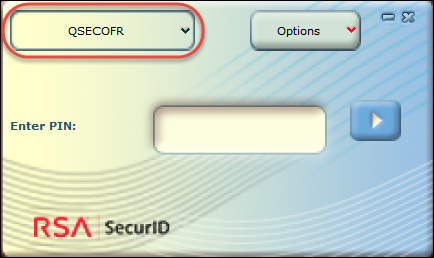
As an administrator, you may need to access a system using either QSECOFR or another user profile that is secured with SecurID authentication. You can do this by configuring multiple tokens on the same PC, which allows you to choose the token for the desired user profile as part of the authentication process using the top-left drop-down menu as shown here (TDUSER and QSECOFR):
Activating QSECOFR
- From the Master Menu, choose 1 to open the Powertech RSA SecurID Agent Maintenance screen.
- Press Enter to continue without creating a new configuration, then press Enter again to display the Work with Profiles for SecurID Agent screen.
-
Enter 2 for the QSECOFR profile.
WARNING: When attempting to activate SecurID authentication against QSECOFR, a warning splash screen is displayed. This screen outlines the potential risks of such action. For example, if the agent's Initial Program does not exist or is inaccessible (e.g. damaged), QSECOFR may not be able to sign on. Such a situation impacts other User Profiles and not just QSECOFR. However, being the most powerful profile, the main consideration is that in the case QSECOFR is not able to sign on, some activity may not be able to be performed by any user profile on the system. Consequently, a lengthy restore activity and/or even a system reset could be required just to ensure QSECOFR can sign on. In addition, as with requiring the use of DR or HA, this sort of obstruction is most likely at the most inopportune time. - Press F14 to accept risks.
- On the Work with Profiles for SecurID Agent, also configure option 7 (IBM i Restricted State) and option 9 (Auth Manager Unavailable) to allow QSECOFR to login when in a restricted state or when SecurID is not running.
-
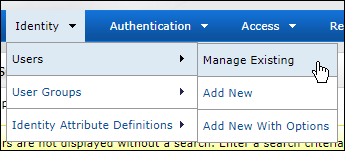
Open the RSA Portal and go to Identity > Users > Manage Existing.
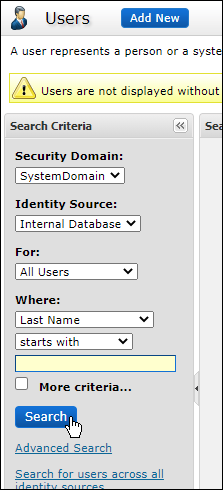
-
Choose Search.
-
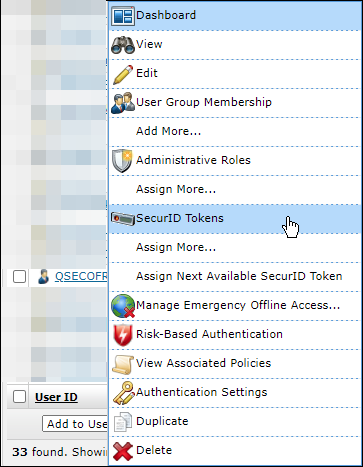
For QSECOFR, which may need to be added if new, go to SecurID Tokens.
-
Choose Assign Token.
-
Chose the next available token. Choose to “Distribute it” and download the Zip file.
-
Import the Token into the RSA SecurID Token PC software:
- Proceed with the standard process to activate the Token:
- Login to a 5250 session as QSECOFR.
- Enter 0000 (four zeroes) as the PIN in the token.
- Enter the PASSCODE presented.
- Change the PIN as requested.
- Wait for the PASSCODE to change, then use the new PIN to get a new PASSCODE.
- Access is granted and the Token is activated, the same as any other 5250 login.