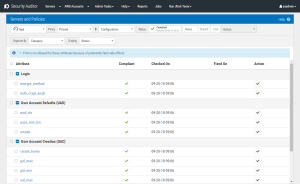
Servers and Policies - Configuration
Use this screen to configure and manage Configuration Policy Templates. When you initialize the Configuration category, Security Auditor identifies your current server configuration settings and lists them as Compliant. You can check these settings in the future to identify settings that have changed, or update the Configuration template to modify your security policy's configuration settings. Many administrators are comfortable with the current settings for these configuration settings and want to make sure that they remain set that way. The way to use Security Auditor to ensure they remain the same is to start by initializing the Security Auditor Configuration category. Go to Servers > Initialize Policies and choose to initialize the Configuration category.
How to get there
In the Manage Servers screen, choose  for a server.
for a server.
What it Does
The Configuration page of the Servers and Policies screen displays an overview of the status of Configuration policy templates.
Status
Displays the status of the Policies and when they were last checked.
Notes
Choose this option to open the Configuration Policy Notes screen where you can record any notes related to the Policy. Notes appear in reports and provide a place to explain the intent of defined policies.
CheckIt
Use this button to run CheckIt, which performs a compliance check for the selected attribute(s).
FixIt
Use this button to run FixIt, which changes the value on the server to match that of Security Auditor.
Action; Enable CheckIt • Disable CheckIt • Enable FixIt • Disable FixIt
Use these options to enable/disable CheckIt and/or FixIt for selected attributes.
Organize By; Category • List
Choose Category to organize the attributes by category (Login, User Account Defaults (UAD), User Account Creation (UAC), and UAC (Password)). Choose List to display the Sort By drop-down menu, where you can choose the method to sort the selected attributes.
Sort By
Choose List in the 'Organize By' drop-down menu to activate this menu, which you can use to select how you want to sort the attributes.
Linux Attributes (RHEL, CentOS, Oracle)
Display; Status • Policy
Choose Status to view each Attribute's Category, Compliance status, and Checked On/Fixed On date and time. Choose Policy to replace the Category and Checked On/Fixed On columns with the Policy Value and Server Value columns, which show the exact values for each attribute on the server compared to the value in Security Auditor.
Default attributes applied when a user logs in
encrypt_method
This defines the system default encryption algorithm for encrypting passwords (if no algorithm are specified on the command line). It can take one of these values:
- DES (default)
- MD5
- SHA256
- SHA512. Note: this parameter overrides the MD5_CRYPT_ENAB variable.
md5_crypt_enab
This variable is deprecated. You should use ENCRYPT_METHOD. Indicate if passwords must be encrypted using the MD5—based algorithm. If set to yes, new passwords will be encrypted using the MD5—based algorithm compatible with the one used by recent releases of FreeBSD. It supports passwords of unlimited length and longer salt strings. Set to no if you need to copy encrypted passwords to other systems which do not understand the new algorithm. Default is no. This variable is superseded by the ENCRYPT__METHOD variable or by any command line option used to configure the encryption algorithm.
mail_dir
The mail spool directory. This is needed to manipulate the mailbox when its corresponding user account is modified or deleted. If not specified, a compile-time default is used.
pass_min_len
Minimum acceptable password Iength.
unmask
Determines file permissions at time of creation: the default is 022.
uid_min
Minimum range of user IDs used for the creation of regular users by useradd or newusers.
uid_max
Maximum range of user lDs used for the creation of reqular users by useradd or newusers.
gid_min
Minimum range of group IDs used for the creation of regular groups by useradd, groupadd, or newusers.
gid_max
Maximum range of group IDs used for the creation of regular groups by useradd, groupadd, or newusers.
userdel_cmd
If defined, this command is run when removing a user. It should remove any at/cron/printjobs etc. owned by the user to be removed (passed as the first argument).
create_home
Indicate if a home directory should be created by default for new users. This setting does not apply to system users, and can be overriden on the command line.
usergroups_enab
This enables userdel to remove user groups if no members exist.
pass_max_days
The maximum number of days a password may be used. If the password is older than this, a password change will be forced. If not specified, -1 will be assumed (which disables the restriction). (PASS_MAX_DAYS, PASS_MIN_DAVS and PASS_WARN_AGE are only used at the time of account creation. Any changes to these settings won't affect existing accounts).
pass_min_days
The minimum number of days allowed between password changes. Any password changes attempted sooner than this will be rejected. If not specified, -1 will be assumed (which disables the restriction). (PASS_MAX_DAYS, PASS_MIN_DAYS and PASS_WARN_AGE are only used at the time of account creation. Any changes to these settings won't affect existing accounts).
pass_warn_age
The number of days warning given before a password expires. A zero means warning is given only upon the day of expiration, a negative value means no warning is given. If not specified, no warning will be provided. (PASS_MAX_DAVS, PASS_MIN_DAVS and PASS_WARN_A6E are only used at the time of account creation. Any changes to these settings won't affect sting accounts).
Linux Attributes (Ubuntu)
Default attributes applied when a user logs in
encrypt_method
This defines the system default encryption algorithm for encrypting passwords (if no algorithm are specified on the command line). It can take one of these values:
- DES (default)
- MD5
- SHA256
- SHA512. Note: this parameter overrides the MD5_CRYPT_ENAB variable.
md5_crypt_enab
This variable is deprecated. You should use ENCRYPT_METHOD. Indicate if passwords must be encrypted using the MD5—based algorithm. If set to yes, new passwords will be encrypted using the MD5—based algorithm compatible with the one used by recent releases of FreeBSD. It supports passwords of unlimited length and longer salt strings. Set to no if you need to copy encrypted passwords to other systems which do not understand the new algorithm. Default is no. This variable is superseded by the ENCRYPT__METHOD variable or by any command line option used to configure the encryption algorithm.
chfn_restrict
This parameter specifies which values in the gecos field of the /etc/passwd file may be changed by regular users using the chfn program. It can be any combination of letters f, r, w, h, for Full name, Room number, Work phone, and Home phone, respectively. For backward compatibility, yes is equivalent to rwh and no is equivalent to frwh. If not specified, only the superuser can make any changes. The most restrictive setting is better achieved by not installing chfn SUID.
default_home
Indicate if login is allowed if we cant cd to the home directory. Default in no. If set to yes, the user will login in the root (/) directory if it is not possible to cd to her home directory.
env_path
If set, it will be used to define the PATH environment variable when a regular user login. The value can be preceded by PATH=, or a colon separated list of paths (for example /bin:/usr/bin). The default value is PATH=/bin:/usr/bin.
env_supath
If set, it will be used to define the PATH environment variable when the superuser login. The value can be preceded by PATH=, or a colon separated list of paths (for example /sbin:/bin:/usr/sbin:/usr/bin). The default value is PATH=/sbin:/bin:/usr/sbin:/usr/bin.
erasechar
Terminal ERASE character (010 = backspace, 0177 = DEL). The value can be prefixed "0" for an octal value, or "0x" for an hexadecimal value.
faillog_enab
Enable logging and display of /var/log/faillog login failure info. This option conflicts with the pam_tally PAM module.
ftmp_file
If defined, login failures will be logged in this file in a utmp format. last, when invoked as lastb, will read /var/log/btmp
hushlogin_file
If defined, this file can inhibit all the usual chatter during the login sequence. If a full pathname is specified, then hushed mode will be enabled if the users name or shell are found in the file. If not a full pathname, then hushed mode will be enabled if the file exists in the users home directory.
killchar
Terminal KILL character (025 = CTRL/U). The value can be prefixed "0" for an octal value, or "0x" for an hexadecimal value.
login_retries
Maximum number of login retries in case of bad password. This will most likely be overridden by PAM, since the default pam_unix module has its own built in of 3 retries. However, this is a safe fallback in case you are using an authentication module that does not enforce PAM_MAXTRIES.
login_timeout
Max time in seconds for login.
log_ok_logins
Enable logging of successful logins.
log_unkfail_enab
Enable display of unknown usernames when login failures are recorded. Note: logging unknown usernames may be a security issue if an user enter her password instead of her login name.
su_name
If defined, the command name to display when running "su -". For example, if this is defined as "su" then a "ps" will display the command is "-su". If not defined, then "ps" would display the name of the shell actually being run, e.g. something like "-sh".
syslog_sg_enab
Enable syslog logging of sg activity.
syslog_su_enab
Enable "syslog" logging of su activity - in addition to sulog file logging.
ttygroup
The terminal permissions: the login tty will be owned by the TTYGROUP group, and the permissions will be set to TTYPERM. By default, the ownership of the terminal is set to the users primary group and the permissions are set to 0600. TTYGROUP can be either the name of a group or a numeric group identifier. If you have a write program which is "setgid" to a special group which owns the terminals, define TTYGROUP to the group number and TTYPERM to 0620. Otherwise leave TTYGROUP commented out and assign TTYPERM to either 622 or 600.
ttyperm
The terminal permissions: the login tty will be owned by the TTYGROUP group, and the permissions will be set to TTYPERM. By default, the ownership of the terminal is set to the users primary group and the permissions are set to 0600. TTYGROUP can be either the name of a group or a numeric group identifier. If you have a write program which is "setgid" to a special group which owns the terminals, define TTYGROUP to the group number and TTYPERM to 0620. Otherwise leave TTYGROUP commented out and assign TTYPERM to either 622 or 600.
mail_dir
The mail spool directory. This is needed to manipulate the mailbox when its corresponding user account is modified or deleted. If not specified, a compile-time default is used.
unmask
Determines file permissions at time of creation: the default is 022.
uid_min
Minimum range of user IDs used for the creation of regular users by useradd or newusers.
uid_max
Maximum range of user lDs used for the creation of reqular users by useradd or newusers.
gid_min
Minimum range of group IDs used for the creation of regular groups by useradd, groupadd, or newusers.
gid_max
Maximum range of group IDs used for the creation of regular groups by useradd, groupadd, or newusers.
usergroups_enab
This enables userdel to remove user groups if no members exist.
dshell
The dshell variable specifies the default login shell on your system.
dhome
The dhome variable specifies the directory containing users home directories.
grouphomes
If grouphomes is yes, then the home directories will be created as /home/groupname/user.
letterhomes
If letterhomes is yes, then the created home directories will have an extra directory - the first letter of the user name. For example: /home/u/user.
skel
The skel variable specifies the directory containing skeletal user files; in other words, files such as a sample .profile that will be copied to the new users home directory when it is created.
first_system_uid
first_system_[gu]id to last_system_[gu]id inclusive is the range for UIDs for dynamically allocated administrative and system accounts/groups. Please note that system software, such as the users allocated by the base-passwd package, may assume that UIDs less than 100 are unallocated.
last_system_uid
first_system_[gu]id to last_system_[gu]id inclusive is the range for UIDs for dynamically allocated administrative and system accounts/groups. Please note that system software, such as the users allocated by the base-passwd package, may assume that UIDs less than 100 are unallocated.
first_system_gid
first_system_[gu]id to last_system_[gu]id inclusive is the range for UIDs for dynamically allocated administrative and system accounts/groups. Please note that system software, such as the users allocated by the base-passwd package, may assume that UIDs less than 100 are unallocated.
last_system_gid
first_system_[gu]id to last_system_[gu]id inclusive is the range for UIDs for dynamically allocated administrative and system accounts/groups. Please note that system software, such as the users allocated by the base-passwd package, may assume that UIDs less than 100 are unallocated.
first_uid
first_[gu]id to last_[gu]id inclusive is the range of UIDs of dynamically allocated user accounts/groups.
last_uid
first_[gu]id to last_[gu]id inclusive is the range of UIDs of dynamically allocated user accounts/groups.
first_gid
first_[gu]id to last_[gu]id inclusive is the range of UIDs of dynamically allocated user accounts/groups.
last_gid
first_[gu]id to last_[gu]id inclusive is the range of UIDs of dynamically allocated user accounts/groups.
usergroups
The usergroups variable can be either yes or no. If yes each created user will be given their own group to use as a default. If "no", each created user will be placed in the group whose gid is USERS_GID (see below).
users_gid
If usergroups is no, then users_gid should be the GID of the group users (or the equivalent group) on your system.
dir_mode
If dir_mode is set, directories will be created with the specified mode. Otherwise the default mode 0755 will be used.
quotauser
If quotauser is set, a default quota will be set from that user with `edquota -p quotauser newuser
skel_ignore_regex
If skel_ignore_regex is set, adduser will ignore files matching this regular expression when creating a new home directory.
pass_max_days
The maximum number of days a password may be used. If the password is older than this, a password change will be forced. If not specified, -1 will be assumed (which disables the restriction). (PASS_MAX_DAYS, PASS_MIN_DAVS and PASS_WARN_AGE are only used at the time of account creation. Any changes to these settings won't affect existing accounts).
pass_min_days
The minimum number of days allowed between password changes. Any password changes attempted sooner than this will be rejected. If not specified, -1 will be assumed (which disables the restriction). (PASS_MAX_DAYS, PASS_MIN_DAYS and PASS_WARN_AGE are only used at the time of account creation. Any changes to these settings won't affect existing accounts).
pass_warn_age
The number of days warning given before a password expires. A zero means warning is given only upon the day of expiration, a negative value means no warning is given. If not specified, no warning will be provided. (PASS_MAX_DAVS, PASS_MIN_DAVS and PASS_WARN_A6E are only used at the time of account creation. Any changes to these settings won't affect sting accounts).
Linux Attributes (SLES)
chfn_restrict
This parameter specifies which values in the gecos field of the /etc/passwd file may be changed by regular users using the chfn program. It can be any combination of letters f, r, w, h, for Full name, Room number, Work phone, and Home phone, respectively. For backward compatibility, yes is equivalent to rwh and no is equivalent to frwh. If not specified, only the superuser can make any changes. The most restrictive setting is better achieved by not installing chfn SUID.
Console
If defined, either full pathname of a file containing device names or a ":" delimited list of device names. Root logins will be allowed only upon these devices.
console_groups
List of groups to add to the users supplementary group set when logging in on the console (as determined by the CONSOLE setting). Default is none.
default_home
Indicate if login is allowed if we cant cd to the home directory. Default is no. If set to yes, the user will login in the root (/) directory if it is not possible to cd to her home directory.
encrypt_method
This defines the system default encryption algorithm for encrypting passwords (if no algorithm are specified on the command line). It can take one of these values: DES (default), MD5, SHA256, SHA512. Note: this parameter overrides the MD5_CRYPT_ENAB variable.
encrypt_method_nis
This defines the system default encryption algorithm for encrypting passwords for NIS systems (if no algorithm are specified on the command line). It can take one of these values: DES (default), MD5, SHA256, SHA512.
env_path
If set, it will be used to define the PATH environment variable when a regular user login. The value can be preceded by PATH=, or a colon separated list of paths (for example /bin:/usr/bin). The default value is PATH=/bin:/usr/bin.
env_rootpath
The default PATH settings for root (used by login)
env_supath
If set, it will be used to define the PATH environment variable when the superuser login. The value can be preceded by PATH=, or a colon separated list of paths (for example /sbin:/bin:/usr/sbin:/usr/bin). The default value is PATH=/sbin:/bin:/usr/sbin:/usr/bin.
erasechar
Terminal ERASE character
fail_delay
Delay in seconds before being allowed another attempt after a login failure.
hushlogin_file
If defined, this file can inhibit all the usual chatter during the login sequence. If a full pathname is specified, then hushed mode will be enabled if the users name or shell are found in the file. If not a full pathname, then hushed mode will be enabled if the file exists in the users home directory.
killchar
Terminal KILL character (025 = CTRL/U). The value can be prefixed "0" for an octal value, or "0x" for an hexadecimal value.
log_ok_logins
Enable logging of successful logins.
log_unkfail_enab
Enable display of unknown usernames when login failures are recorded. Note: logging unknown usernames may be a security issue if an user enter her password instead of her login name.
login_retries
Maximum number of login retries in case of bad password. This will most likely be overridden by PAM, since the default pam_unix module has its own built in of 3 retries. However, this is a safe fallback in case you are using an authentication module that does not enforce PAM_MAXTRIES.
login_timeout
Max time in seconds for login.
motd_file
If defined, ":" delimited list of "message of the day" files to be displayed upon login.
sha_crypt_max_rounds
Only works if ENCRYPT_METHOD is set to SHA256 or SHA512. Define the number of SHA rounds. With a lot of rounds, it is more difficult to brute forcing the password. But note also that it more CPU resources will be needed to authenticate users. If not specified, the libc will choose the default number of rounds (5000). The values must be inside the 1000-999999999 range. If only one of the MIN or MAX values is set, then this value will be used. If MIN > MAX, the highest value will be used.
sha_crypt_min_rounds
Only works if ENCRYPT_METHOD is set to SHA256 or SHA512. Define the number of SHA rounds. With a lot of rounds, it is more difficult to brute forcing the password. But note also that it more CPU resources will be needed to authenticate users. If not specified, the libc will choose the default number of rounds (5000). The values must be inside the 1000-999999999 range. If only one of the MIN or MAX values is set, then this value will be used. If MIN > MAX, the highest value will be used.
sulog_file
If defined, all su activity is logged to this file.
syslog_sg_enab
Enable syslog logging of sg activity.
syslog_su_enab
Enable "syslog" logging of su activity - in addition to sulog file logging.
ttygroup
The terminal permissions: the login tty will be owned by the TTYGROUP group, and the permissions will be set to TTYPERM. By default, the ownership of the terminal is set to the users primary group and the permissions are set to 0600. TTYGROUP can be either the name of a group or a numeric group identifier. If you have a write program which is "setgid" to a special group which owns the terminals, define TTYGROUP to the group number and TTYPERM to 0620. Otherwise leave TTYGROUP commented out and assign TTYPERM to either 622 or 600.
ttyperm
The terminal permissions: the login tty will be owned by the TTYGROUP group, and the permissions will be set to TTYPERM. By default, the ownership of the terminal is set to the users primary group and the permissions are set to 0600. TTYGROUP can be either the name of a group or a numeric group identifier. If you have a write program which is "setgid" to a special group which owns the terminals, define TTYGROUP to the group number and TTYPERM to 0620. Otherwise leave TTYGROUP commented out and assign TTYPERM to either 622 or 600.
ttytype_file
If defined, file which maps tty line to TERM environment parameter. Each line of the file is in a format something like "vt100 tty01".
groupadd_cmd
If defined, this command is run when adding a group.
umask
Determines file permissions at time of creation; the default is 022.
create_home
Indicate if a home directory should be created by default for new users. This setting does not apply to system users, and can be overriden on the command line.
gid_max
Maximum range of group IDs used for the creation of regular groups by useradd, groupadd, or newusers.
gid_min
Minimum range of group IDs used for the creation of regular groups by useradd, groupadd, or newusers.
max_members_per_group
If set to a non-nul number, the shadow utilities will make sure that groups never have more than this number of users on one line. This permits support to split groups (groups split into multiple lines, with the same group ID, to avoid limitation of the line length in the group file). 0 is the default value and disables this feature.
sys_gid_max
(SUSE 12) SYS_GID_MIN to SYS_GID_MAX inclusive is the range for GIDs for dynamically allocated administrative and system groups.
sys_gid_min
(SUSE 12) SYS_GID_MIN to SYS_GID_MAX inclusive is the range for GIDs for dynamically allocated administrative and system groups.
sys_uid_max
(SUSE 12) SYS_UID_MIN to SYS_UID_MAX inclusive is the range for UIDs for dynamically allocated administrative and system accounts.
sys_uid_min
(SUSE 12) SYS_UID_MIN to SYS_UID_MAX inclusive is the range for UIDs for dynamically allocated administrative and system accounts.
uid_max
Maximum range of user IDs used for the creation of regular users by useradd or newusers.
uid_min
Minimum range of user IDs used for the creation of regular users by useradd or newusers.
useradd_cmd
If defined, this command is run when adding a user.
userdel_cmd
If defined, this command is run when removing a user. It should remove any at/cron/print jobs etc. owned by the user to be removed (passed as the first argument).
userdel_postcmd
If defined, this command is run after removing a user.
userdel_precmd
UserAccountCreationMisc
usergroups_enab
This enables userdel to remove user groups if no members exist.
pass_max_days
The maximum number of days a password may be used. If the password is older than this, a password change will be forced. -1 value means the restriction is disabled. If not specified, -1 will be assumed. (PASS_MAX_DAYS, PASS_MIN_DAYS and PASS_WARN_AGE are only used at the time of account creation. Any changes to these settings will not affect existing accounts).
pass_min_days
The minimum number of days allowed between password changes. Any password changes attempted sooner than this will be rejected. -1 value means the restriction is disabled. If not specified, -1 will be assumed. (PASS_MAX_DAYS, PASS_MIN_DAYS and PASS_WARN_AGE are only used at the time of account creation. Any changes to these settings will not affect existing accounts).
pass_warn_age
The number of days warning given before a password expires. A zero means warning is given only upon the day of expiration. -1 value means no warning is given. If not specified, -1 will be assumed (which disables the warning). (PASS_MAX_DAYS, PASS_MIN_DAYS and PASS_WARN_AGE are only used at the time of account creation. Any changes to these settings will not affect existing accounts).
AIX Attributes
binmode
Controls whether bin collection, as defined in the bin stanza, is used.
streammode
Controls whether stream data collection, as defined in the file specified in the stream stanza, is configured at the start up of the audit system.
trail
Specifies the path name of the audit trail file.
bin1
Specifies the path name that the auditbin daemon uses for its primary bin file.
bin2
Specifies the path name that the auditbin daemon uses for its secondary bin file.
binsize
Specifies a decimal integer string that defines the threshold size (in bytes) of each audit bin.
bincmds
Specifies the path name of the file that contains the audit backend commands called by the auditbin daemon.
freespace
Specifies a decimal integer string that defines the recommended number of 512-byte free blocks in the file system where the audit trail file is located.
streamcmds
To enable the auditbin daemon to set up stream collection, add lines to the start and stream stanzas of the /etc/security/audit/config file.
auth_type *
Defines the route through which all users will be authenticated (in supported applications).
dist_uniqid
Defines the system configuration for resolving ID collision for creating/modifying user/group accounts among registries.
logintimeout
Defines the time (in seconds) the user is given to type the login name and the password.
maxlogins
Defines the maximum number of simultaneous logins to the system.
maxroles
Defines the maximum number of roles that each session allows.
mkhomeatlogin
Specifies whether to create a home directory at login if the home directory does not already exist.
shells
Defines the valid shells on the system.
pwd_algorithm *
Defines the loadable password algorithm to use when you store user passwords.
admin
Defines the administrative status of the user. Possible values are: (1) true - The user is an administrator. Only the root user can change the attributes of users defined as administrators. (2) false- The user is not an administrator. This is the default value.
admgroups
Lists the groups the user administrates. The value parameter is a comma-separated list of group names.
auth1 *
Primary auth method (Deprecated: use SYSTEM), Lists the primary methods for authenticating the user.
auth2 *
Lists the secondary methods for authenticating the user.
SYSTEM *
Defines the system authentication mechanism for the user.
capabilities
Defines the system privileges (capabilities) which are granted to a user by the login or su commands.
default_roles *
Specifies the default roles for the user; can only contain roles assigned to the user in the roles attribute. You can use the ALL keyword to signify that the default roles for the user are all their assigned roles.
rcmds
Controls the remote execution of the r-commands (rsh, rexec, rcp); Possible values are allow (default), deny, and hostlogincontrol, which specifies that the ability of remote command execution is determined by the hostsallowedlogin and hostsdeniedlogin attributes. The user is only allowed to execute remote commands on a target system if the user (or target user) is allowed to log in the target system.
roles *
Lists the administrative roles for this user. The Value parameter is a list of role names, separated by commas.
su
Indicates whether another user can switch to the specified user account with the su command - true (default) or false.
sugroups
Lists the groups that can use the su command to switch to the specified user account; a value of ALL indicates all groups. An ! (exclamation point) in front of a group name excludes that group. If this attribute is not specified, all groups can switch to this user account with the su command.
umask
Determines file permissions at time of creation; the default is 022.
dictionlist *
Defines the password dictionaries used when creating new passwords.
histexpire
Defines the period of time (in weeks) that a user cannot reuse a password. The value is a decimal integer string. The default is 0, indicating that no time limit is set. Only an administrative user can change this attribute.
histsize
Defines the number of previous passwords a user cannot reuse. The value is a decimal integer string. The default is 0. Only an administrative user can change this attribute.
maxage
Defines the maximum age in weeks of a password. The password must be changed by this time. The value is a decimal integer string. The default is a value of 0, indicating no maximum age. Range: 0 to 52
maxexpired
Defines the maximum time in weeks beyond maxage that a user can change an expired password. After this defined time, only an administrative user can change the password. The value is a decimal integer string. The default is -1, which means the user can always change their expired password regardless of how many weeks have passed. If the maxexpired attribute is 0, the password expires when the maxage value is met. If the maxage attribute is 0, the maxexpired attribute is ignored. Range: 0 to 52 (a root user is exempt from maxexpired)
maxrepeats
Defines the maximum number of times a character can be repeated in a new password. Since a value of 0 is meaningless, the default value of 8 indicates that there is no maximum number. The value is a decimal integer string. Range: 0 to 8
minage
Defines the minimum age (in weeks) a password must be before it can be changed. The value is a decimal integer string. The default is a value of 0, indicating no minimum age. Range: 0 to 52
minalpha
Defines the minimum number of alphabetic characters that must be in a new password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
mindiff
Defines the minimum number of characters required in a new password that were not in the old password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
minlen
Defines the minimum length of a password. The value is a decimal integer string. The default is a value of 0, indicating no minimum length. The maximum value allowed is 8. This attribute is determined by by minlen and/or minalpha + minother, whichever is greater. minalpha + minother should never be greater than 8. If minalpha + minother is greater than 8, then the effective value for minother is reduced to 8 - minalpha.
minother
Defines the minimum number of non-alphabetic characters that must be in a new password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
pwdchecks *
Defines the password restriction methods enforced on new passwords. The value is a list of comma-separated method names and is evaluated from left to right. A method name is either an absolute path name or a path name relative to /usr/lib of an executable load module.
pwdwarntime
Defines the number of days before the system issues a warning that a password change is required. The value is a decimal integer string. A zero or negative value indicates that no message is issued. The value must be less than the difference of the maxage and minage attributes. Values greater than this difference are ignored and a message is issued when the minage value is reached.
account_locked *
Indicates if the user account is locked - yes, true, and always are equivalent; no, false, and never are equivalent.
expires
Identifies the expiration date of the account. The Value parameter is a 10-character string in the MMDDhhmmYY form, where MM = month, DD = day, hh = hour, mm = minute, and YY = last 2 digits of the years 1939 through 2038. All characters are numeric. If the Value parameter is 0, the account does not expire. The default is 0.
login
Indicates if the user can log into the system with the login command - true (default) or false.
logindelay
The time in seconds between login prompts. This will be multiplied with the number of failed attempts; for example, 5,10,15,20 seconds when 5 is the initial value.
logindisable
Disable login on this terminal after logintimes consecutive failed attempts.
loginreenable
Re-enable the terminal after it was automatically disabled after specified minutes.
loginretries
Defines the number of unsuccessful login attempts allowed after the last successful login before the system locks the account; A zero or negative value indicates that no limit exists.
logininterval
Terminal will be disabled when the specified invalid attempts have been made within specified seconds.
logintimes
Defines the days and times that the user is allowed to access the system.
maxulogs
Defines the maximum number of logins for the user. If the concurrent login number for a user exceeds the maximum number of allowed logins, the login is denied.
rlogin *
Indicates if the user can access the account remotely with the telnet or rlogin commands - true (default) or false.
sak_enabled
Values for the sak_enabled attribute are: true - SAK processing is enabled, so the key sequence establishes a trusted path for the port: false - SAK processing is not enabled, so a trusted path cannot be established. This is the default value.
admgroups
Lists the groups the user administrates. The value parameter is a comma-separated list of group names.
auth1 *
Primary auth method (Deprecated: use SYSTEM), Lists the primary methods for authenticating the user.
auth2 *
Lists the secondary methods for authenticating the user.
SYSTEM *
Defines the system authentication mechanism for the user.
capabilities
Defines the system privileges (capabilities) which are granted to a user by the login or su commands.
default_roles *
Specifies the default roles for the user; can only contain roles assigned to the user in the roles attribute. You can use the ALL keyword to signify that the default roles for the user are all their assigned roles.
home
Full path name of the home directory of the user. The $USER macro can be used for defining policy, e.g. /home/$USER.
rcmds
Controls the remote execution of the r-commands (rsh, rexec, rcp); Possible values are allow (default), deny, and hostlogincontrol, which specifies that the ability of remote command execution is determined by the hostsallowedlogin and hostsdeniedlogin attributes. The user is only allowed to execute remote commands on a target system if the user (or target user) is allowed to log in the target system.
roles *
Lists the administrative roles for this user. The Value parameter is a list of role names, separated by commas.
shell
Defines the program run for the user at session initiation - full path name.
su
Indicates whether another user can switch to the specified user account with the su command - true (default) or false.
sugroups
Lists the groups that can use the su command to switch to the specified user account; a value of ALL indicates all groups. An ! (exclamation point) in front of a group name excludes that group. If this attribute is not specified, all groups can switch to this user account with the su command.
umask
Determines file permissions at time of creation; the default is 022.
admgroups
Lists the groups the user administrates. The value parameter is a comma-separated list of group names.
auth1 *
Primary auth method (Deprecated: use SYSTEM), Lists the primary methods for authenticating the user.
auth2 *
Lists the secondary methods for authenticating the user.
SYSTEM *
Defines the system authentication mechanism for the user.
capabilities
Defines the system privileges (capabilities) which are granted to a user by the login or su commands.
default_roles *
Specifies the default roles for the user; can only contain roles assigned to the user in the roles attribute. You can use the ALL keyword to signify that the default roles for the user are all their assigned roles.
home
Full path name of the home directory of the user. The $USER macro can be used for defining policy, e.g. /home/$USER.
rcmds
Controls the remote execution of the r-commands (rsh, rexec, rcp); Possible values are allow (default), deny, and hostlogincontrol, which specifies that the ability of remote command execution is determined by the hostsallowedlogin and hostsdeniedlogin attributes. The user is only allowed to execute remote commands on a target system if the user (or target user) is allowed to log in the target system.
roles *
Lists the administrative roles for this user. The Value parameter is a list of role names, separated by commas.
shell
Defines the program run for the user at session initiation - full path name.
su
Indicates whether another user can switch to the specified user account with the su command - true (default) or false.
sugroups
Lists the groups that can use the su command to switch to the specified user account; a value of ALL indicates all groups. An ! (exclamation point) in front of a group name excludes that group. If this attribute is not specified, all groups can switch to this user account with the su command.
umask
Determines file permissions at time of creation; the default is 022.
auditclasses *
Lists the users audit classes. The Value parameter is a list of comma-separated classes, or a value of ALL to indicate all audit classes.
pgrp
Identifies the users primary group - value cannot be null. The $USER macro can be used for defining policy, e.g. $USER.
groups
Identifies the groups the user belongs to. The $USER macro can be used for defining policy, e.g. $USER group2 group3.
dictionlist *
Defines the password dictionaries used when creating new passwords.
histexpire
Defines the period of time (in weeks) that a user cannot reuse a password. The value is a decimal integer string. The default is 0, indicating that no time limit is set. Only an administrative user can change this attribute.
histsize
Defines the number of previous passwords a user cannot reuse. The value is a decimal integer string. The default is 0. Only an administrative user can change this attribute.
maxage
Defines the maximum age in weeks of a password. The password must be changed by this time. The value is a decimal integer string. The default is a value of 0, indicating no maximum age. Range: 0 to 52
maxexpired
Defines the maximum time in weeks beyond maxage that a user can change an expired password. After this defined time, only an administrative user can change the password. The value is a decimal integer string. The default is -1, which means the user can always change their expired password regardless of how many weeks have passed. If the maxexpired attribute is 0, the password expires when the maxage value is met. If the maxage attribute is 0, the maxexpired attribute is ignored. Range: 0 to 52 (a root user is exempt from maxexpired)
maxrepeats
Defines the maximum number of times a character can be repeated in a new password. Since a value of 0 is meaningless, the default value of 8 indicates that there is no maximum number. The value is a decimal integer string. Range: 0 to 8
minage
Defines the minimum age (in weeks) a password must be before it can be changed. The value is a decimal integer string. The default is a value of 0, indicating no minimum age. Range: 0 to 52
minalpha
Defines the minimum number of alphabetic characters that must be in a new password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
mindiff
Defines the minimum number of characters required in a new password that were not in the old password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
minlen
Defines the minimum length of a password. The value is a decimal integer string. The default is a value of 0, indicating no minimum length. The maximum value allowed is 8. This attribute is determined by by minlen and/or minalpha + minother, whichever is greater. minalpha + minother should never be greater than 8. If minalpha + minother is greater than 8, then the effective value for minother is reduced to 8 - minalpha.
minother
Defines the minimum number of non-alphabetic characters that must be in a new password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
pwdchecks *
Defines the password restriction methods enforced on new passwords. The value is a list of comma-separated method names and is evaluated from left to right. A method name is either an absolute path name or a path name relative to /usr/lib of an executable load module.
pwdwarntime
Defines the number of days before the system issues a warning that a password change is required. The value is a decimal integer string. A zero or negative value indicates that no message is issued. The value must be less than the difference of the maxage and minage attributes. Values greater than this difference are ignored and a message is issued when the minage value is reached.
account_locked *
Indicates if the user account is locked - yes, true, and always are equivalent; no, false, and never are equivalent.
expires
Identifies the expiration date of the account. The Value parameter is a 10-character string in the MMDDhhmmYY form, where MM = month, DD = day, hh = hour, mm = minute, and YY = last 2 digits of the years 1939 through 2038. All characters are numeric. If the Value parameter is 0, the account does not expire. The default is 0.
login
Indicates if the user can log into the system with the login command - true (default) or false
loginretries
DDefines the number of unsuccessful login attempts allowed after the last successful login before the system locks the account; A zero or negative value indicates that no limit exists.
maxulogs
Defines the maximum number of logins for the user. If the concurrent login number for a user exceeds the maximum number of allowed logins, the login is denied.
rlogin *
Indicates if the user can access the account remotely with the telnet or rlogin commands - true (default) or false.