User-driven Attack Packages
The best attacks are not exploits. Rather, the best attacks take advantage of normal features to get code execution. Cobalt Strike makes it easy to setup several user-driven attacks. These attacks take advantage of listeners you’ve already setup. Navigate in the menu to Payloads and choose one of the following options.
HTML Application
An HTML Application is a Windows program written In HTML and an Internet Explorer supported scripting language. This package generates an HTML Application that runs a Cobalt Strike listener.
Navigate to Payloads -> HTML Application.
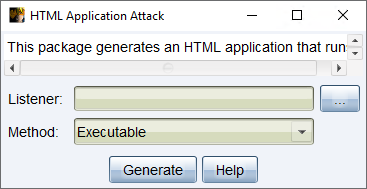
figure 36 - HTML Application Attack
Listener - Press the ... button to select a Cobalt Strike listener you would like to output a payload for.
Method - Use the drop-down to select one of the following methods to run the selected listener:
Executable: This method writes an executable to disk and run it.
PowerShell: This method uses a PowerShell one-liner to run your payload stager.
VBA: This method uses a Microsoft Office macro to inject your payload into memory. The VBA method requires Microsoft Office on the target system.
Press Generate to create the HTML Application.
MS Office Macro
The Microsoft Office Macro tool generates a macro to embed into a Microsoft Word or Microsoft Excel document.
Navigate to Payloads -> MS Office Macro.
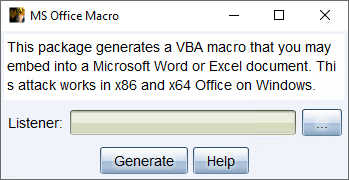
figure 37 - MS Office Macro
Choose a listener and press Generate to create the step-by-step instructions to embed your macro into a Microsoft Word or Excel document.
This attack works well when you can convince a user to run macros when they open your document.
Payload Generator
Cobalt Strike's Payload Generator outputs source code and artifacts to stage a Cobalt Strike listener onto a host. Think of this as the Cobalt Strike version of msfvenom.
Navigate to Payloads -> Stager Payload Generator.
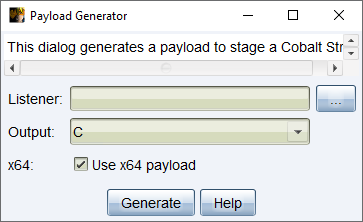
figure 38 - Payload Generator
Listener - Press the ... button to select a Cobalt Strike listener you would like to output a payload for.
Output - Use the drop-down to select one of the following output types (most options give you shellcode formatted as a byte array for that language):
C: Shellcode formatted as a byte array.
C#: Shellcode formatted as a byte array.
COM Scriptlet: A .sct file to run a listener
Java: Shellcode formatted as a byte array.
Perl: Shellcode formatted as a byte array.
PowerShell: PowerShell script to run shellcode
PowerShell Command: PowerShell one-liner to run a Beacon stager.
Python: Shellcode formatted as a byte array.
Raw: blob of position independent shellcode.
Ruby: Shellcode formatted as a byte array.
Veil: Custom shellcode suitable for use with the Veil Evasion Framework.
VBA: Shellcode formatted as a byte array.
x64 - Check the box to generate an x64 stager for the selected listener.
Press Generate to create a Payload for the selected output type.
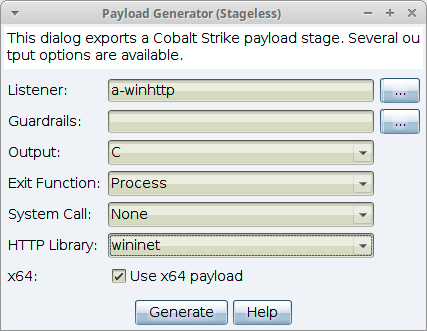
Payload Generator (Stageless)
Cobalt Strike's Payload Generator outputs source code and artifacts, without a stager, to a Cobalt Strike listener onto a host.
Navigate to Payloads -> Stageless Payload Generator.
figure 39 - Stageless Payload Generator
Listener - Press the ... button to select a Cobalt Strike listener you would like to output a payload for.
![]()
figure 40 - Guardrail Settings
Output - Use the drop-down to select one of the following output types (most options give you shellcode formatted as a byte array for that language):
C: Shellcode formatted as a byte array.
C#: Shellcode formatted as a byte array.
Java: Shellcode formatted as a byte array.
Perl: Shellcode formatted as a byte array.
Python: Shellcode formatted as a byte array.
Raw: blob of position independent shellcode.
Ruby: Shellcode formatted as a byte array.
VBA: Shellcode formatted as a byte array.
Exit Function - This function determines the method/behavior that Beacon uses when the exit command is executed.
Process: Terminates the whole process.
Thread: Terminates only the current thread.
None: Use the standard Windows API function.
Direct: Use the Nt* version of the function.
Indirect: Jump to the appropriate instruction within the Nt* version of the function.
HTTP Library - Select the Microsoft library (WinINet or WinHTTP) for the generated payload.
DNS Comm Mode - This option allows you to use DNS Over HTTPS (DOH) for egressing from the target using a DNS Beacon. The default value is determined by Malleable C2 “comm_mode“ option from listener definition. You can define more DOH configuration options in Malleable C2.
x64 - Check the box to generate an x64 stager for the selected listener.
Press Generate to create a Payload for the selected output type.
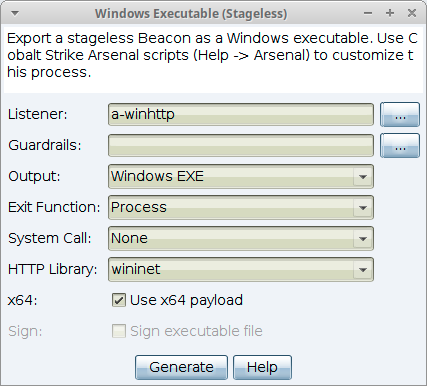
Windows Executable
This package generates a Windows executable artifact that delivers a payload stager.
Navigate to Payloads -> Windows Stager Payload.
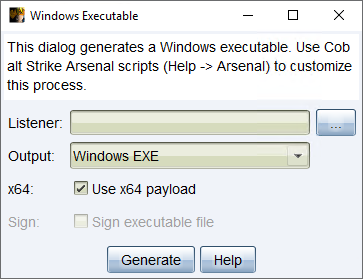
figure 41 - Window Executable
This package provides the following output options:
Listener - Press the ... button to select a Cobalt Strike listener you would like to output a payload for.
Output - Use the drop-down to select one of the following output types.
Windows EXE: A Windows executable.
Windows Service EXE: A Windows executable that responds to Service Control Manager commands. You may use this executable to create a Windows service with sc or as a custom executable with the Metasploit Framework’s PsExec modules.
Windows DLL: A Windows DLL that exports a StartW function that is compatible with rundll32.exe. Use rundll32.exe to load your DLL from the command line.
rundll32 foo.dll,StartW
x64- Check the box to generate x64 artifacts that pair with an x64 stager. By default, this dialog exports x64 payload stagers.
sign - Check the box to sign an EXE or DLL artifact with a code-signing certificate. You must specify a certificate in a Malleable C2 profile. The check box is enabled/disabled based on the selected listener’s Malleable C2 profile.
Press Generate to create a payload stager artifact.
Cobalt Strike uses its Artifact Kit to generate this output.
Windows Executable (Stageless)
This package exports Beacon, without a stager, as an executable, service executable, 32-bit DLL, or 64-bit DLL. A payload artifact that does not use a stager is called a stageless artifact. This package also has a PowerShell option to export Beacon as a PowerShell script and a raw option to export Beacon as a blob of position independent code.
Navigate to Payloads -> Windows Stageless Payload.
figure 42 - Windows Stageless Executable
This package provides the following output options:
Listener - Press the ... button to select a Cobalt Strike listener you would like to output a payload for.
Guardrails - If your listener has been configured with guardrails, the value is displayed as the default. Use the ... button to override the settings for the beacon.
![]()
figure 43 - Guardrail Settings
Output - Use the drop-down to select one of the following output types.
PowerShell: A PowerShell script that injects a stageless Beacon into memory.
Raw: A blob of position independent code that contains Beacon.
Windows EXE: A Windows executable.
Windows Service EXE: A Windows executable that responds to Service Control Manager commands. You may use this executable to create a Windows service with sc or as a custom executable with the Metasploit Framework's PsExec modules.
Windows DLL: A Windows DLL that exports a StartW function that is compatible with rundll32.exe. Use rundll32.exe to load your DLL from the command line.
rundll32 foo.dll,StartW
Process: Terminates the whole process.
Thread: Terminates only the current thread.
None: Use the standard Windows API function.
Direct: Use the Nt* version of the function.
Indirect: Jump to the appropriate instruction within the Nt* version of the function.
HTTP Library - -Select the Microsoft library (WinINet or WinHTTP) for the generated payload.
DNS Comm Mode - This option allows you to use DNS Over HTTPS (DOH) for egressing from the target using a DNS Beacon. The default value is determined by Malleable C2 “comm_mode“ option from listener definition. You can define more DOH configuration options in Malleable C2.
x64 - Check the box to generate an x64 artifact that contains an x64 payload. By default, this dialog exports x64 payloads.
sign - Check the box to sign an EXE or DLL artifact with a code-signing certificate. You must specify a certificate in a Malleable C2 profile. The check box is enabled/disabled based on the selected listener’s Malleable C2 profile.
Press Generate to create a stageless artifact.
Cobalt Strike uses its Artifact Kit to generate this output.
Windows Executable (Stageless) Variants
This option generates all the stageless payloads (in x86 and x64) for all the configured listeners. Use the listeners_stageless aggressor function to see the list that will be used for the active team server.
Navigate to Payloads -> Windows Stageless Generate All Payloads.
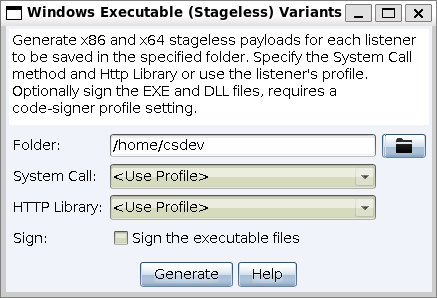
figure 44 - Windows Stageless Executable Variants
Folder - Press the folder button to select a location to save the listener(s).
None: Use the standard Windows API function.
Direct: Use the Nt* version of the function.
Indirect: Jump to the appropriate instruction within the Nt* version of the function.
User Profile: Use the value specified in the listener’s profile.
HTTP Library - Select the Microsoft library (WinINet or WinHTTP) for the generated payload. [
WinInet: Use the WinInet library.
WinHTTP: Use the WinHTTP library.
User Profile: Use the value specified in the listener’s profile.
DNS Comm Mode - This option allows you to use DNS Over HTTPS (DOH) for egressing from the target using a DNS Beacon. The “<Use Profile>" option uses the Malleable C2 “comm_mode“ option from the listener definition for each generated payload. You can define more DOH configuration options in Malleable C2.
Sign - Check the box to sign an EXE or DLL artifact with a code-signing certificate. You must specify a certificate in a Malleable C2 profile. When connected to one team server the check box is enabled when the certificate is configured in the Malleable C2 profile. When connected to more than one team server the check box will be enabled, and if checked the executable file will be signed with the certificate that is configured in the listener’s profile for the payload being generated.
Press Generate to create a stageless artifact.